Enabling Network Communication
Specific network settings are required to enable communication between Ops Insights and Oracle Cloud Databases.
You must enable communication between Ops Insights and the Oracle Cloud Database by adding the ingress and egress security rules to an NSG or a Security List in the VCN in which the Oracle Cloud Database can be accessed.
Before you enable communication between Ops Insights and the Oracle Cloud Database, you must:
- Ensure that you're familiar with security rules. For information, see Security Rules.
- Depending on whether you want to use NSGs or Security Lists to add the ingress and egress rules, you must have the required permissions and be familiar with how to add security rules.
Note
- An NSG must be available to create an Ops Insights private endpoint. For more information, see Network Security Groups.
- A security list rule that allows access over the database port number is applied to the NSG for access within the VCN or subnet CIDR block. For more information, see Security Lists.
- Make a note of the Oracle Cloud Database private IP addresses and port details and the Ops Insights private IP addresses. These are details that you may have to enter when you add security rules, and here's information on where you can find them:
- For Oracle Cloud Database port details, see the DB System Information section on the Database System Details page for Oracle Databases on Bare Metal and Virtual Machine DB systems. For Oracle Databases on Exadata Cloud service, see Network details on the Exadata VM Cluster Details page.
- For Oracle Cloud Database private IP addresses, see the Nodes section on the Database System Details page for single instance databases on Bare Metal and Virtual Machine DB systems. For RAC databases, use the Scan IP Address, which is available on the DB System Details page for the Virtual Machine DB system and on the Exadata VM Cluster Details page for the Exadata Cloud service.
For Ops Insights to communicate with the Oracle Cloud Database, you must add ingress and egress security rules using either Network Security Groups (NSG) or Security Lists. The following examples illustrate how to enable communication between an Ops Insights private endpoint and the Oracle Databases on a Virtual Machine DB system using NSGs and Security Lists.
Create an NSG to enable communication between the Ops Insights private endpoint and a Virtual Machine DB system
In the following example, an NSG is created and added to:
- A Virtual Machine DB system
- An Ops Insights private endpoint for single instance Oracle Cloud Databases (which is already created)
On completing the tasks listed in this example, the Ops Insights private endpoint will have access to all the single instance databases in the Virtual Machine DB system's VCN without impacting the VCN's subnet architecture.
For information on creating an NSG in the Virtual Machine DB system's VCN, see To create an NSG.
The Virtual Machine DB system's VCN port is configured by the user, enter the port number you previously configured.
- Ingress rule for the Virtual Machine DB system's VCN: The Virtual Machine DB system's VCN can receive incoming traffic from the Ops Insights private endpoint's subnet (10.0.0.0/24) from any port.
- Egress rule for the Ops Insights private endpoint: The Ops Insights private endpoint's subnet (from any port) can send requests to the Virtual Machine DB system's VCN (10.0.0.0/16) on port 1521.
Enter the port you have configured for the TCPS enabled database if the port is different from 1521.
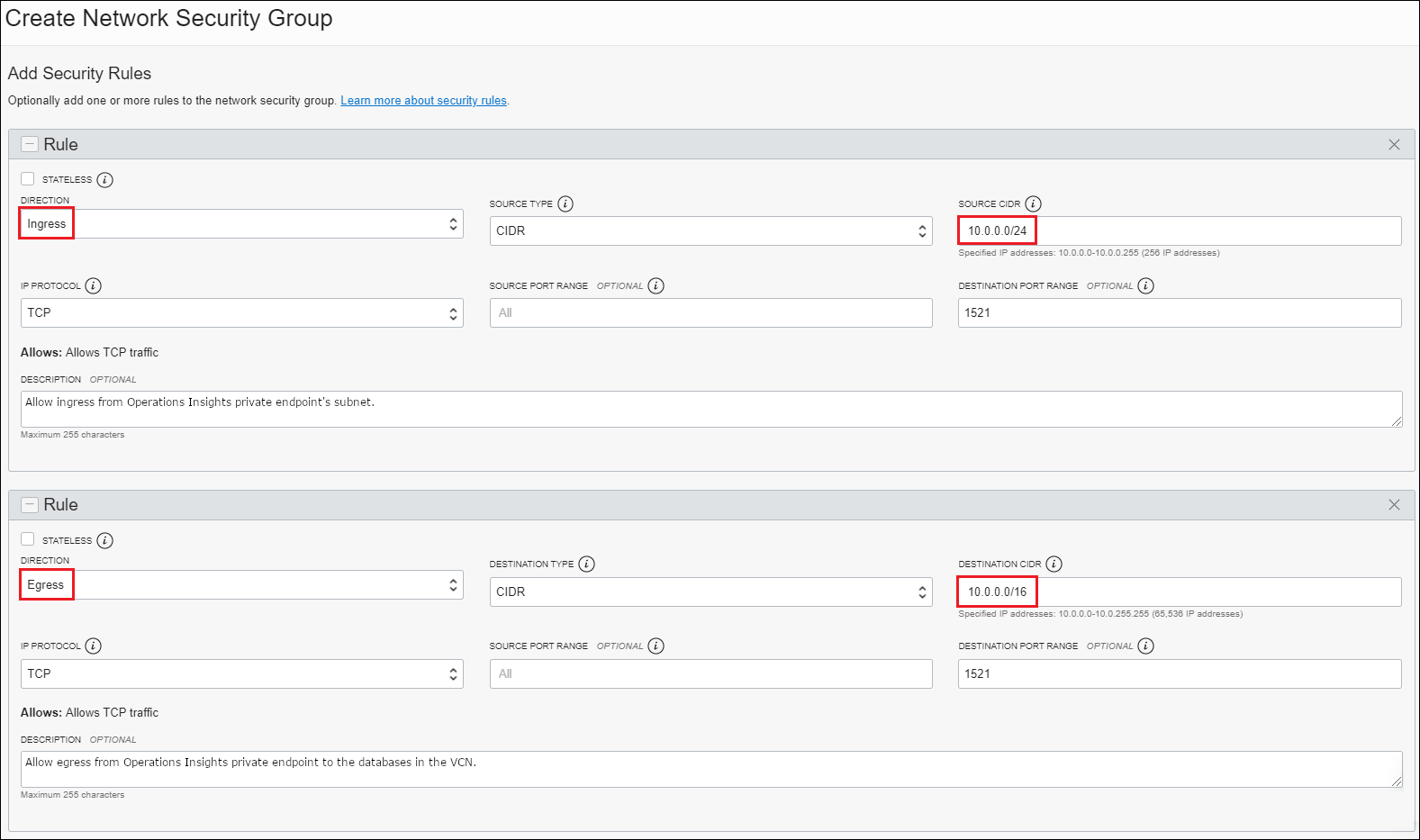
After you create the NSG, you must add it to the Virtual Machine DB system and the Ops Insights private endpoint.
For information on how to add the NSG to the Virtual Machine DB system, see Adding or Removing a Resource from an NSG.
To add the NSG to the Ops Insights private endpoint, go to the Ops Insights Private Endpoint Administration page (Administration > Private Endpoints) and click the private endpoint to which you want to add the NSG. On the Private Endpoint Details page, click Edit against Network Security Groups and add the newly created NSG.
Add security rules to a Security List to enable communication between an Ops Insights private endpoint and a Virtual Machine DB system
In the following example, stateful security rules are added to an existing Security List in the Virtual Machine DB system's VCN to enable communication between an Ops Insights private endpoint for single instance Oracle Cloud Databases and all the subnets in the VCN. This ensures that the Ops Insights private endpoint can access all the single instance databases in the VCN.
For information on updating an existing Security List, see To update rules in an existing security list.
The Virtual Machine DB system's VCN port is configured by the user, enter the port number you previously configured.
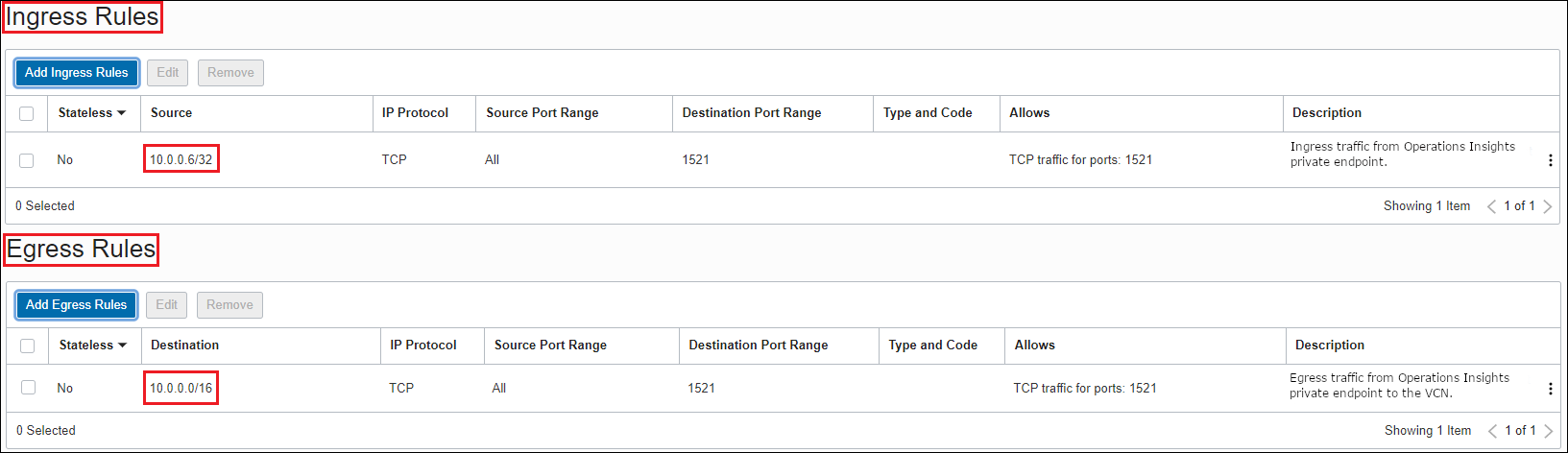
- Ingress rule for the Virtual Machine DB system's VCN: The Virtual Machine DB system's VCN can receive incoming traffic from the Ops Insights private IP address (10.0.0.6/32) from any port.
- Egress rule for the Ops Insights private endpoint: The Ops Insights private IP address (from any port) can send requests to the Virtual Machine DB system's VCN (10.0.0.0/16) on port 1521.
Enter the port you have configured for the TCPS enabled database if the port is different from 1521.
Obtaining CIDR Block Values
The CIDR block values used to define rules will be specific to your environment and not those shown in the above examples. You can obtain the correct CIDR ingress/egress rule values for your Ops Insights environment as follows:
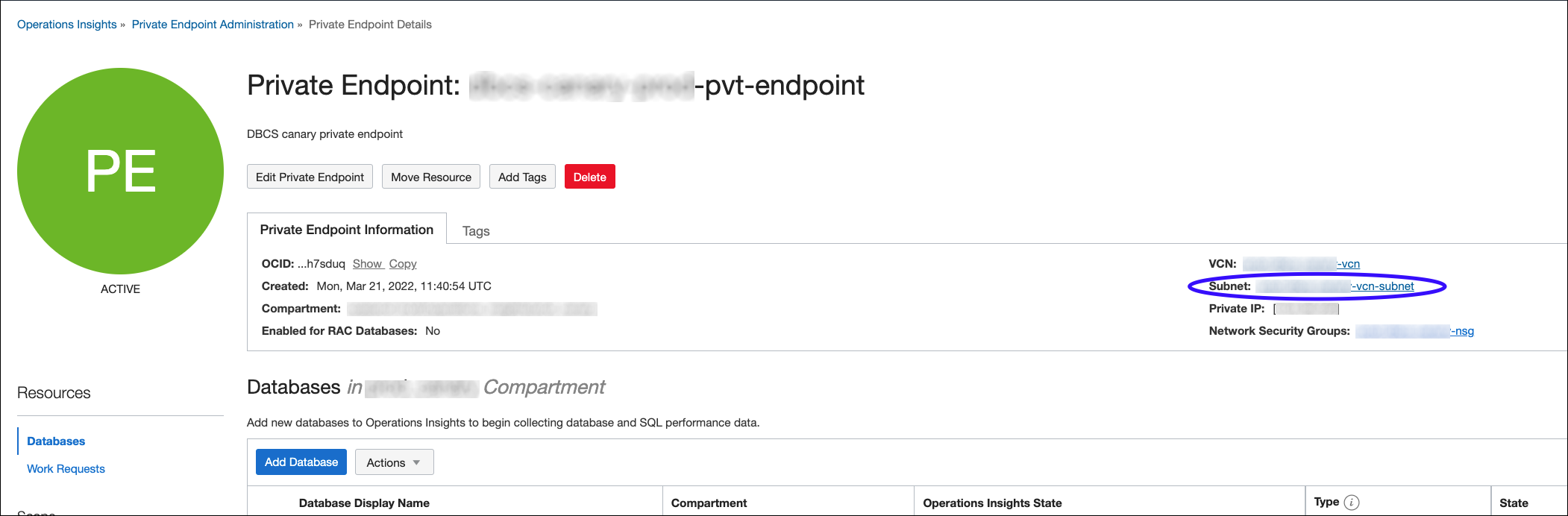
- Ingress Rules
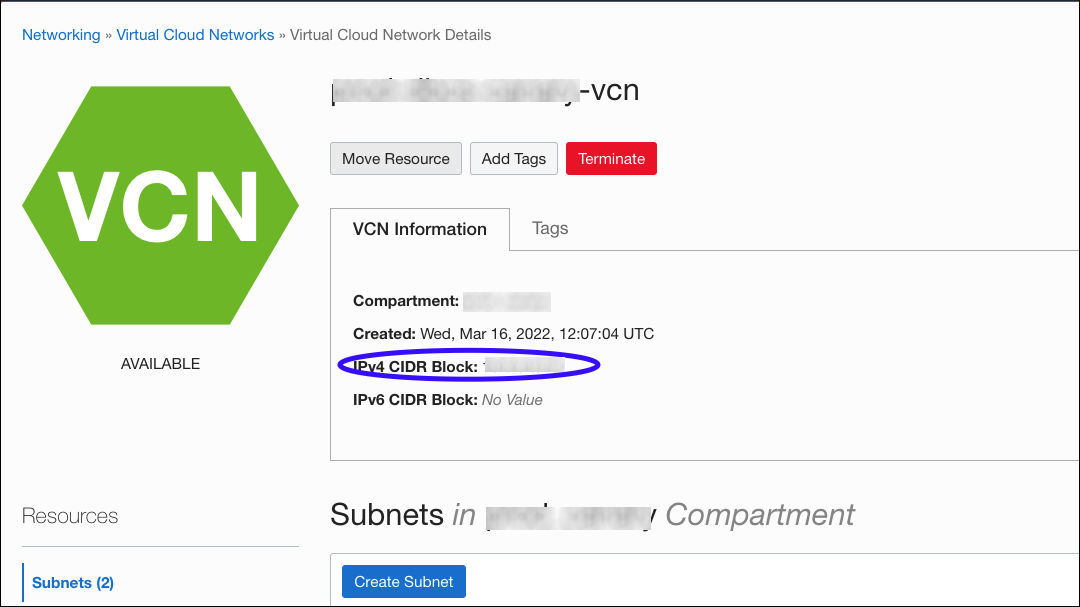
The ingress rule you need to create depends on the subnet specified when creating the private endpoint. You can find the CIDR block on the VCN/Subnet page. Ops Insights also provides a convenient link to the VCN/Subnet page directly from the Private Endpoint Details page.
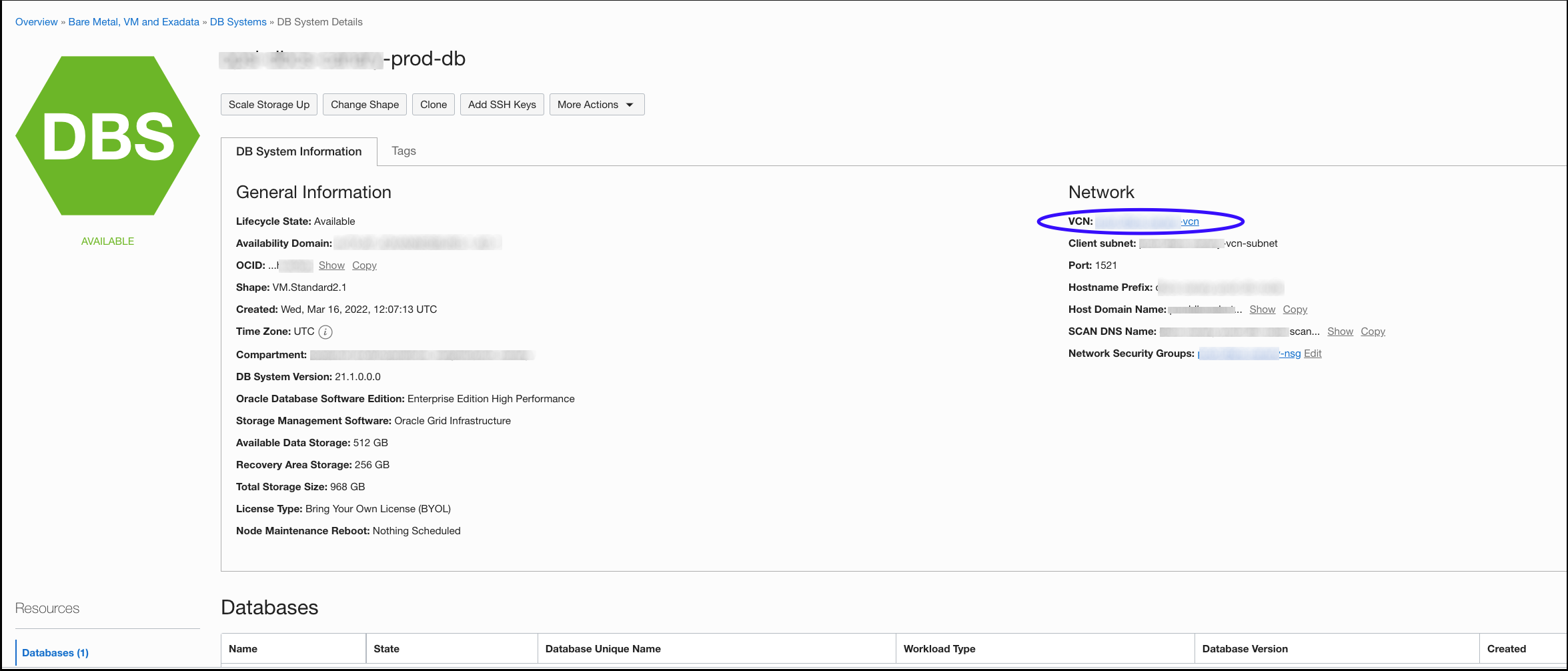
- Egress Rules
The egress rule you need to create depends on the VCN in which your Oracle Cloud Database(s) reside. You can find the CIDR block by navigating to the database details page where you'll find a link to the associated VCN.
 Note
Note
You should write your rule using the entire CIDR block so that the private endpoint can be used for all databases in the VCN.
TCPS Enabling Permissions
If you opt to use the TCP/IP with Transport Layer Security (TCPS) protocol to securely connect to the Oracle Cloud Database, then you're required to enter the port number and upload the database wallet when enabling Database Management.
- Java Keystore (JKS): To save a Java Keystore wallet as a secret, you're required to enter the Keystore password, Keystore content (.jks file), Truststore password, Truststore content (.jks file), and the Certificate Distinguished Name (DN) for the wallet.
- Public-Key Cryptography Standards (PKCS) # 12: To save a PKCS#12 wallet as a secret, you're required to enter the wallet password, wallet content (.p12 file), and the certificate DN for the wallet.
For information on how to configure TLS authentication, see Configuring Transport Layer Security Authentication.