Routing Network Traffic to a Firewall
Scenarios showing how to route network traffic to a firewall.
This topic shows scenarios for routing traffic to a network firewall. For more information about network routing, see VCN Route Tables and Intra-VCN Routing.
For better performance, consider not adding stateful rules to the security list attached to the firewall subnet, or include the firewall in a network security group (NSG) that contains stateful rules.
Security list or network security group (NSG) rules associated with the firewall subnet and VNICs are evaluated before the firewall. Be sure that any security list or NSG rules allow the traffic to enter the firewall so that it can be evaluated appropriately.
If the policy you use with the firewall doesn't have any rules specified, the firewall denies all traffic.
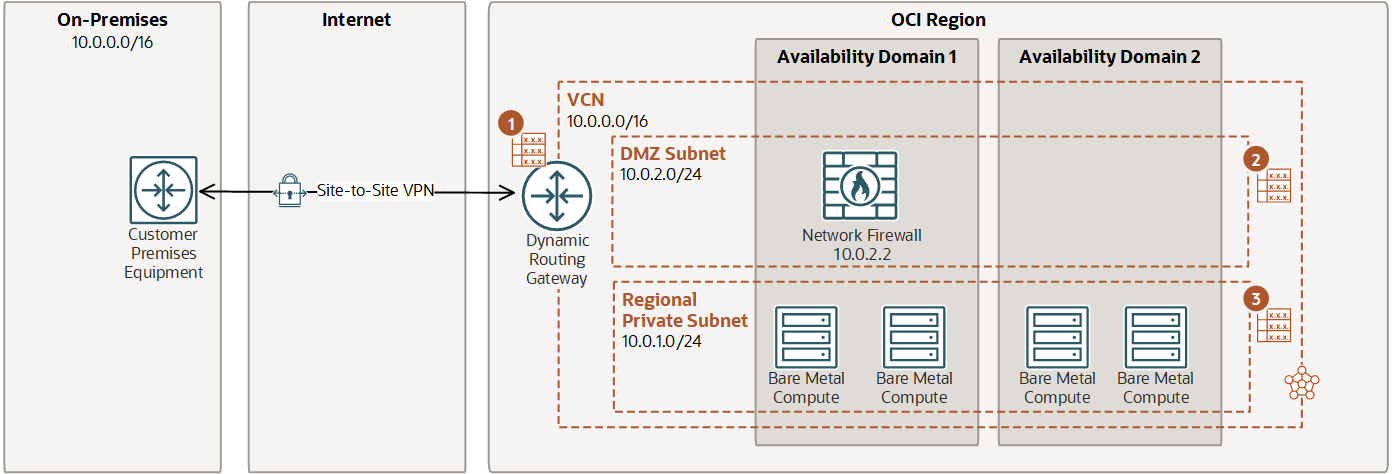
An example of how to set up routing from an on-premises network to your VCN using a Dynamic Routing Gateway (DRG).
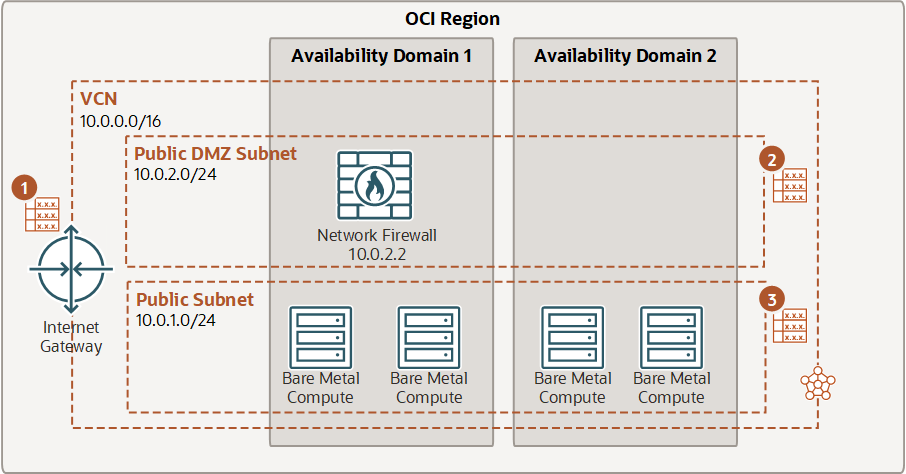
In this example, routing is configured from the internet to the firewall. Traffic is routed from the IGW, through the firewall, and then from the firewall subnet to a public subnet.
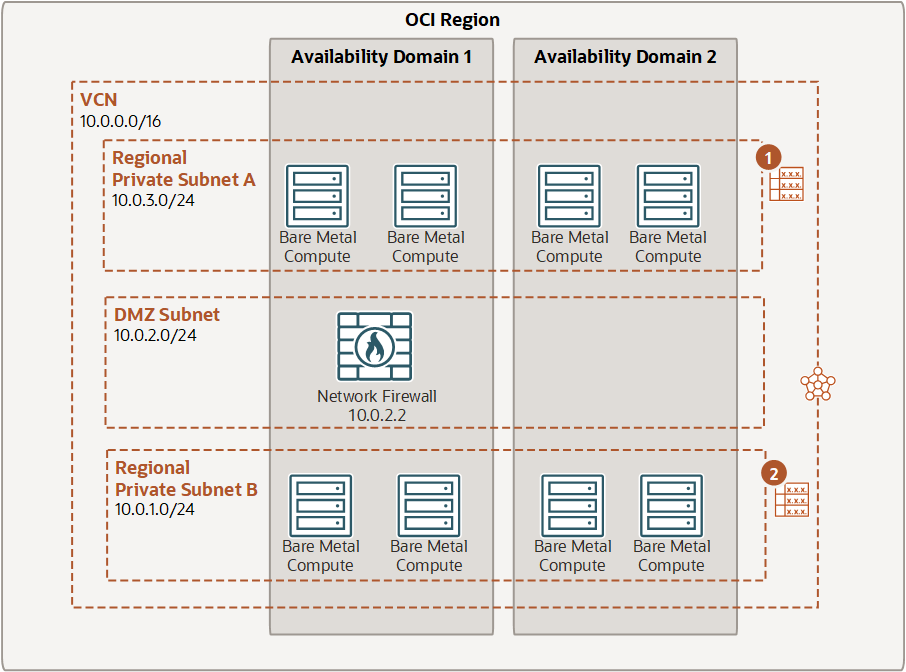
In this example, traffic is routed from Subnet A, to the firewall. From the firewall, traffic is routed to Subnet B using the implicit 10.0.0.0 to "local" (not shown).