Getting Started
Before you can get started with Exadata Fleet Update as shown in the diagram here, there are some prerequisites that need to be met. Review the prerequisites listed below carefully.
Figure 3-1 Exadata Fleet Update
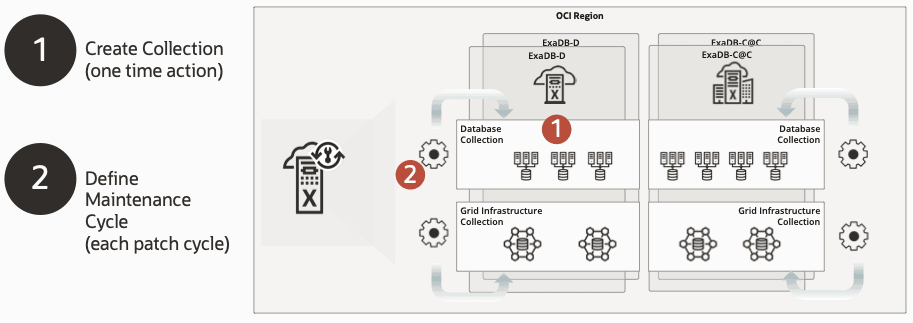
- Required Network Setup
Review the security rules to use with your ExaDB-D Infrastructure. Security rules control the types of traffic allowed for the client network and backup network of the Exadata's compute nodes. - Required IAM Policies to Manage Collections
Review the IAM policies required to manage an Exadata Fleet Update collection of Oracle Exadata Database Service on Dedicated Infrastructure (ExaDB-D) or Oracle Exadata Database Service on Cloud@Customer (ExaDB-C@C) resources. - Required IAM Policies to Manage Maintenance Cycles
Review the IAM policies required to manage Exadata Fleet Update Maintenance Cycle and Action resources for Oracle Exadata Database Service on Dedicated Infrastructure (ExaDB-D) or Oracle Exadata Database Service on Cloud@Customer (ExaDB-C@C) resources. - Policy Builder
Use the policy builder to generate policy statements and create the policy if you have the necessary permissions.