Account and Access Concepts
Understand these components of OCI before you get started.
Tenancy
When you sign up or subscribe to Oracle Cloud services, Oracle creates a tenancy for you. You can think of the tenancy as your account, but it is also a secure and isolated partition within Oracle Cloud Infrastructure where you can create, organize, and administer your cloud resources. When you sign up, your tenancy is created in your home region, but you can subscribe your tenancy to as many regions as you need. Large organizations can have multiple tenancies. See Tenancy Management.
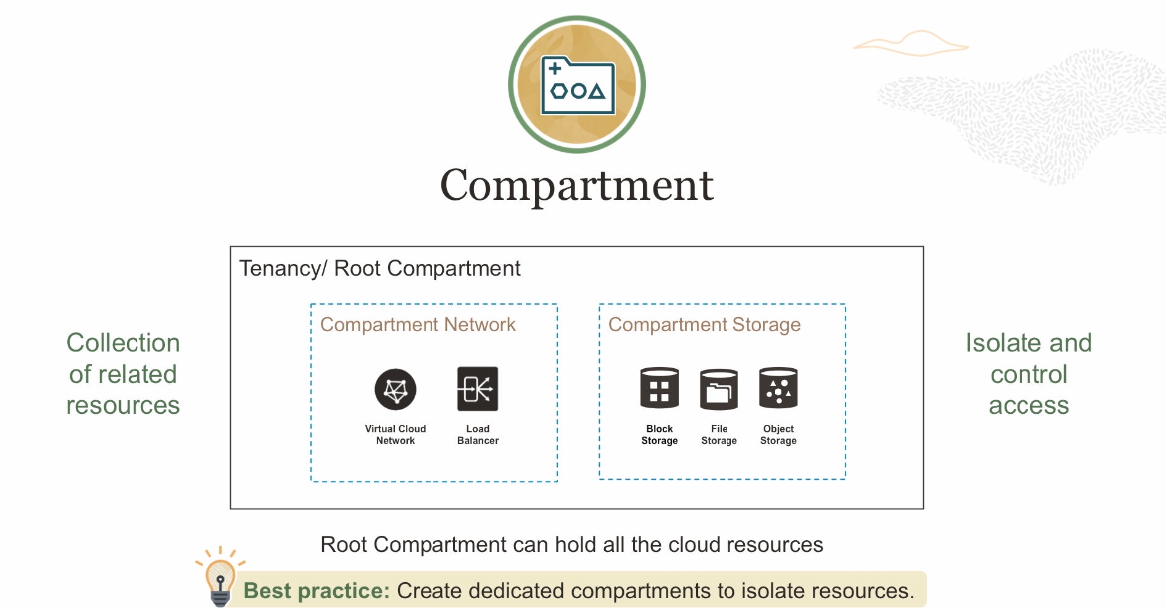
Compartments allow you to organize and control access to your cloud
resources. A compartment is a collection of related resources (such as instances,
virtual cloud networks, block volumes) that can be accessed only by certain groups that
have been given permission by an administrator. A compartment should be thought of as a
logical group and not a physical container. When you begin working with resources in the
Console, the compartment acts as a filter for what you
are viewing.
When you sign up for Oracle Cloud Infrastructure,
Oracle creates your tenancy, which is the root compartment that holds all
your cloud resources. You then create additional compartments within the tenancy (root
compartment) and corresponding policies to control access to the resources in each
compartment. When you create a cloud resource such as an instance, block volume, or
cloud network, you must specify to which compartment you want the resource to belong.
Ultimately, the goal is to ensure that each person has access to
only the resources they need.
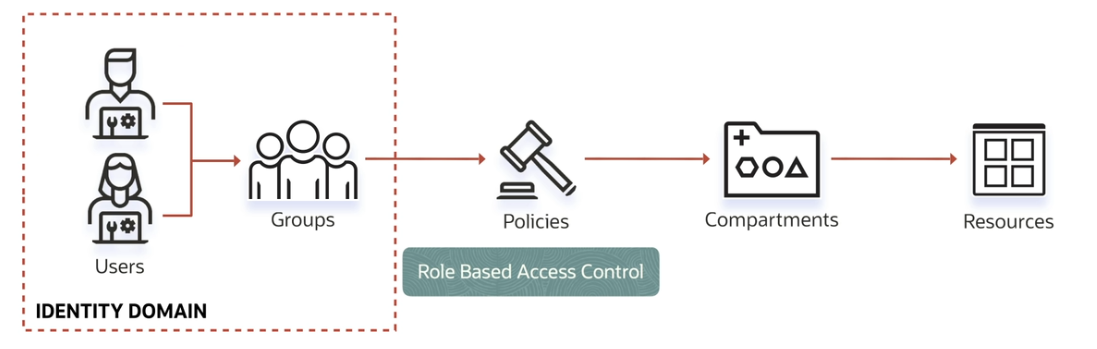
An identity domain is a container for managing users and roles, federating and provisioning of users, secure application integration through Oracle Single Sign-On (SSO) configuration, and OAuth administration. It represents a user population in Oracle Cloud Infrastructure and its associated configurations and security settings (such as MFA). See Overview of IAM.
A policy is a document that specifies who can access which resources, and how. You can write policies to control access to all of the services within Oracle Cloud Infrastructure. Access is granted at the group and compartment level, which means you can write a policy that gives a group a specific type of access within a specific compartment, or to the tenancy itself. If you give a group access to the tenancy, the group automatically gets the same type of access to all the compartments inside the tenancy. For more information, see Example Scenario and IAM Policies Overview.
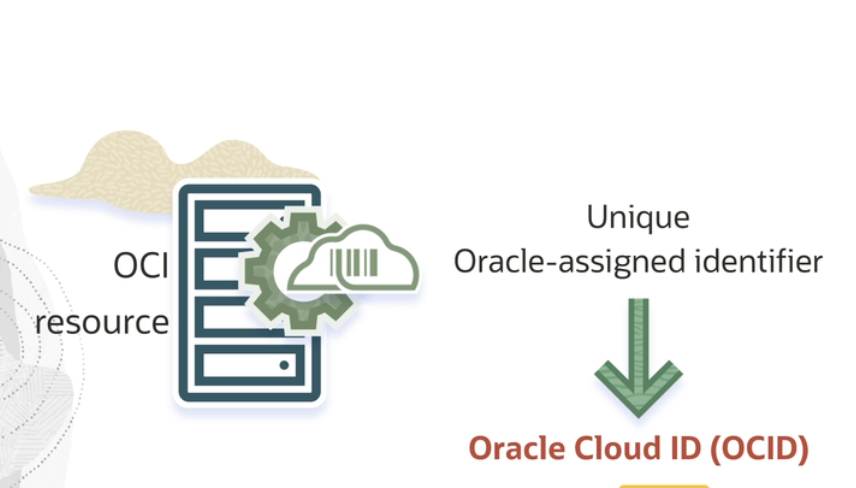
OCID
Every Oracle Cloud Infrastructure resource has an
Oracle-assigned unique ID called an Oracle Cloud Identifier (OCID). This ID is included
as part of the resource's information in both the Console and
API.
For details about the syntax of an OCID, see Resource Identifiers.
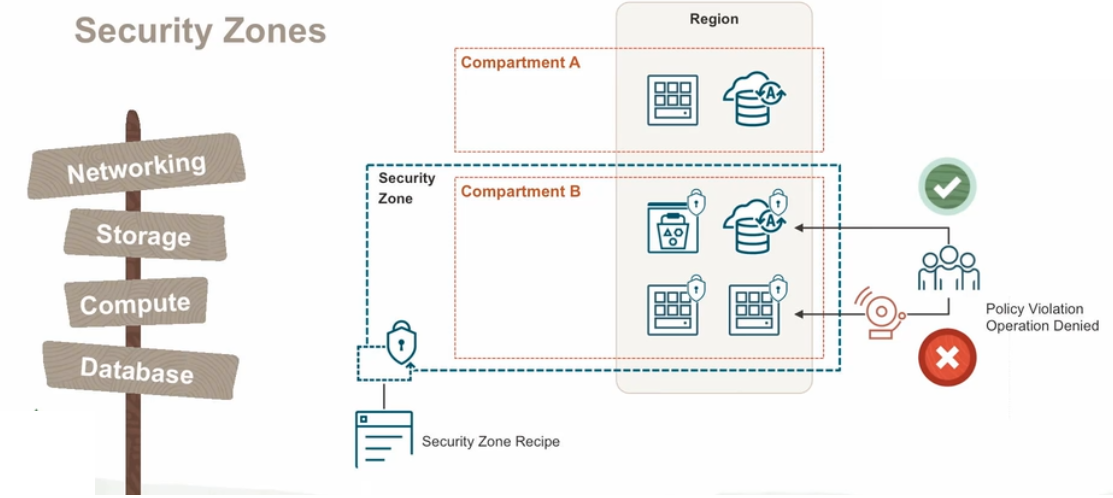
Security Zones let you be confident
that your Compute, Networking, Object Storage, Database, and other resources comply with Oracle
security principles and best practices. A security zone is associated with one or more
compartments and a security zone recipe. When you
create and update resources in a security zone, Oracle Cloud Infrastructure validates these operations against security
zone policies in the zone's recipe. If any security zone policy is violated, then the
operation is denied. For more information, see Overview of Security Zones.