Service Mesh: Configure client mTLS
In this tutorial, configure a Oracle Cloud Infrastructure (OCI) Service Mesh ingress gateway to support mTLS encrypted connections from a web browser.
Key tasks include how to:
- Issue the required certificates for mTLS.
- Issue the required certificate authority bundle.
- Configure mTLS for your ingress gateway.
- Configure your browser for mTLS support.
- Connect from your browser to the BookInfo application over a secure connection.
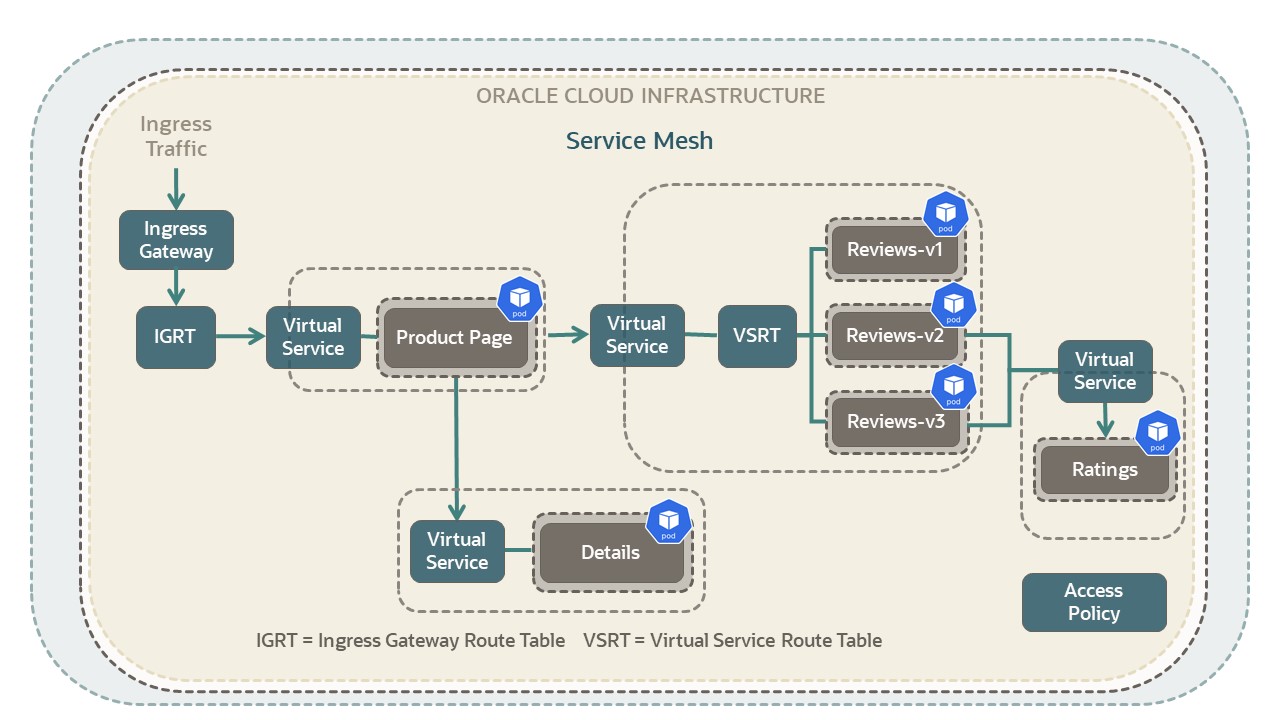
The gray rectangular boxes in the picture represent virtual deployments in the application. The named virtual deployments include: Product Page, Details, Reviews v1 to v3, and Ratings.
For additional information, see:
Before You Begin
To successfully perform this tutorial, you must have the following:
- Completion of the OCI Service Mesh Overview Tutorial. All steps and setup required for the overview tutorial must be completed to perform this tutorial.
- Additonal requirements:
1. Prepare 🔗
Prepare your environment to create and deploy your application.
Collect the following information from the Oracle Cloud Infrastructure Console.
- The OCID for your Service Mesh compartment.
- The ingress gateway certificate OCID once the certificate is created.
- The
bookinfoCA Bundle OCID once the bundle is created.
2. Create and Configure Certificates for your Ingress Gateway 🔗
Create and configure the certificates needed for your ingress gateway.
The steps assume you have a Certificate Authority called
mesh-demo-ca
for the Mesh. The Certificate Authority issues certificates for the mTLS between ingress
gateway and browser.Follow these steps to create the required certificates and configure your application.
Issue a Certificate for the Ingress Gateway
To create a certificate for your ingress gateway, perform the following steps:
- Open the navigation menu and click Identity & Security. Under Certificates, click Certificate Authorities.
- Select the compartment where the certificate authority is located.
- Select your certificate authority: mesh-demo-ca
- Click Issue Certificate.
- Fill out the Basic Information dialog:
- Compartment: <Select-your-Compartment>
- Certificate Type: Issued by internal CA
- Name: bookinfo-ingress
- Description: Add your description (Optional)
Note
Avoid entering confidential information.
Note
This example, uses bookinfo-ingress for the certificate name. When implementing your own certs, create your own unique name for the cert. - Click Next.
- Fill out the Subject Information dialog:
- Common name: bookinfo.example.com
- Subject Alternative Names: <leave-blank>
- Click Next
- Fill out the Certificate Configuration dialog:
- Certificate Profile type: TLS Server or Client
- Other fields: <take-defaults>
- Click Next
- Fill out the Rules dialog:
- All fields: <take-defaults>
- Click Next
- Review your choices in the Summary dialog.
- Click Create Certificate.
Issue a Certificate for the Browser
To create a certificate for browsers, perform the following steps:
- Open the navigation menu and click Identity & Security. Under Certificates, click Certificate Authorities.
- Select the compartment where the certificate authority is located.
- Select your certificate authority: mesh-demo-ca
- Click Issue Certificate.
- Fill out the Basic Information dialog:
- Compartment: <Select-your-Compartment>
- Certificate Type: Issued by internal CA
- Name: bookinfo-client
- Description: Add your description (Optional)
Note
Avoid entering confidential information.
Note
This example, uses bookinfo-client for the certificate name. When implementing your own certs, create your own unique name for the cert. - Click Next.
- Fill out the Subject Information dialog:
- Common name: bookinfo-client
- Subject Alternative Names: <leave-blank>
- Click Next
- Fill out the Certificate Configuration dialog:
- Certificate Profile type: TLS Server or Client
- Other fields: <take-defaults>
- Click Next
- Fill out the Rules dialog:
- All fields: <take-defaults>
- Click Next
- Review your choices in the Summary dialog.
- Click Create Certificate.
Create a Certificate Bundle for the Certificate Authority
To get your Certificate Chain PEM, perform the following steps:
- Open the navigation menu and click Identity & Security. Under Certificates, click Certificate Authorities.
- Select your certificate authority: mesh-demo-ca
- In the left nav, click Versions.
- In the "latest" row, click ... to the right of the row.
- Click View Content.
- For Certificate Chain PEM, click Copy.
To create a CA Bundle, perform the following steps:
- Open the navigation menu and click Identity & Security. Under Certificates, click Certificates.
- In the left nav, click CA Bundles.
- Click Create CA Bundle.
- Fill out the Create CA Bundle dialog:
- Compartment: <Select-your-Compartment>
- Name: bookinfo
- PEM file: Select Paste Content
- Paste your copied content into the dialog.
- Click Create.
Configure mTLS with a Configuration file
Use the following meshify-bookinfo-mtls.yaml file to configure
mTLS.
- Create the
meshify-bookinfo-mtls.yamlfile and using the following sample file as a starting point. - Update
compartmentIdfor the Ingress Gateway with your compartment OCID. - Update
certificateIdunderserverCertificateto be the Ingress Gateway certificate OCID. - Update
caBundleIdunderclientValidationto be the bookinfo CA Bundle OCID. - To apply your changes run:
kubectl apply -f meshify-bookinfo-mtls.yaml
---
kind: IngressGateway
apiVersion: servicemesh.oci.oracle.com/v1beta1
metadata:
name: bookinfo-ingress-gateway
namespace: bookinfo
spec:
compartmentId: ocid1.compartment.oc1..aaaaaaaaaa...
mesh:
ref:
name: bookinfo
hosts:
- name: bookinfoHost
hostnames:
- bookinfo.example.com
- bookinfo.example.com:443
listeners:
- port: 9080
protocol: HTTP
tls:
mode: MUTUAL_TLS
serverCertificate:
ociTlsCertificate:
certificateId: ocid1.certificate.oc1.iad.aaaaaaaaaa...
clientValidation:
trustedCaBundle:
ociCaBundle:
caBundleId: ocid1.cabundle.oc1.iad.aaaaaaaaaa...
accessLogging:
isEnabled: true
---
apiVersion: servicemesh.oci.oracle.com/v1beta1
kind: IngressGatewayDeployment
metadata:
name: bookinfo-ingress-gateway-deployment
namespace: bookinfo
spec:
ingressGateway:
ref:
name: bookinfo-ingress-gateway
deployment:
autoscaling:
minPods: 1
maxPods: 1
ports:
- protocol: TCP
port: 9080
serviceport: 443
service:
type: LoadBalancer
---3. Install the Browser Client Certificate 🔗
Install the browser client certificate you created.
Prepare the Client Certificate for the Browser
To prepare your client certificate, perform the following steps:
- Download the
bookinfo-clientcertificate.oci certificates certificate-bundle get --certificate-id ocid1.certificate.oc1.iad.aaaaaaaaaa... | jq -r '.data."certificate-pem"' > bookinfo-client.pem -
Download the
bookinfo-clientcertificate private key.oci certificates certificate-bundle get --certificate-id ocid1.certificate.oc1.iad.aaaaaaaaaa... --bundle-type CERTIFICATE_CONTENT_WITH_PRIVATE_KEY | jq -r '.data."private-key-pem"' bookinfo-client-key.pem -
Create a PKCS file containing the certificate and the private key.
openssl pkcs12 -export -in bookinfo-client.pem -inkey bookinfo-client-key.pem -out bookinfo-client.p12To provide a blank password, press enter when prompted for password.
Import the Client Certificate
Import the client certificate (PKCS file) into your browser. Typically, all browsers are configured to use the client certificates from the OS Certificate Store. This example imports the certificate into Firefox.
To import the client certificate into the Firefox browser from a PKCS file, perform the following steps:
- Open a new tab, enter about:preferences#privacy in the address bar and hit enter.
- Scroll down to Security then Certificates.
- Click on View Certificates.
- In the Certificate Manager dialog, click Your Certificates.
- Click Import.
- Navigate to the
bookinfo-client.p12file and import it.
Test your Certificate with the following steps:
- Open a new tab and navigate to https://bookinfo.example.com.
- In the popup dialog, select the bookinfo-client certificate.
4. Add Client Certificate to a Java Application 🔗
Add your client certificate to a Java HTTP client application. To allow your Java application to connect to your mesh through mTLS, add the following Java code snippet examples.
Add your client certificate to a Java HTTP client application. To allow your Java application to connect to your mesh through mTLS, add the following Java code snippet examples.
Review the Java Code to add a Client Certificate
To add a client certificate to your Java code, follow these steps:
- Fetch client certificate with private key.
GetCertificateBundleRequest getCertificateBundleRequest = GetCertificateBundleRequest.builder() .certificateId("ocid1.certificate.oc1.iad.aaaaaaaaaa...") // bookinfo-client certificate id .certificateBundleType(GetCertificateBundleRequest.CertificateBundleType.CertificateContentWithPrivateKey) .build(); CertificateBundleWithPrivateKey clientCertificate = (CertificateBundleWithPrivateKey) client.getCertificateBundle(getCertificateBundleRequest).getCertificateBundle(); - Fetch CA bundle for server cert validation.
GetCertificateAuthorityBundleRequest getCertificateAuthorityBundleRequest = GetCertificateAuthorityBundleRequest.builder() .certificateAuthorityId("ocid1.certificate.oc1.iad.aaaaaaaaaa...") // mesh-demo-ca certificate authority id .build(); CertificateAuthorityBundle caBundle = client.getCertificateAuthorityBundle(getCertificateAuthorityBundleRequest).getCertificateAuthorityBundle(); - Prepare SSLContext using a third-party library called sslcontext-kickstart.
- Add Maven dependency for the library.
<dependency> <groupId>io.github.hakky54</groupId> <artifactId>sslcontext-kickstart-for-pem</artifactId> <version>7.4.5</version> </dependency> - Create the
SSLContextin Java.SSLFactory sslFactory = SSLFactory.builder() .withIdentityMaterial(keyManager) .withTrustMaterial(trustManager) .build(); SSLContext sslContext = sslFactory.getSslContext();
- Add Maven dependency for the library.
- Initialize
HTTPClient.HttpClient httpClient = HttpClient.newBuilder() .sslParameters(sslFactory.getSslParameters()) .sslContext(sslFactory.getSslContext()) .build(); - Access https://bookinfo.example.com.
HttpClient httpClient = HttpClient.newBuilder() .sslParameters(sslFactory.getSslParameters()) .sslContext(sslFactory.getSslContext()) .build(); HttpRequest request = HttpRequest.newBuilder() .GET() .uri(URI.create("https://bookinfo.example.com")) .build(); HttpResponse<String> response = httpClient.send(request, HttpResponse.BodyHandlers.ofString());
What's Next 🔗
Congratulations! You have successfully configured ingress gateway client mTLS for your Bookinfo app Service Mesh.
To explore more information about development with Oracle products, check out these sites: