Upload an SSL Certificate
Certificates are used to validate outbound SSL connections.
- Sign in to Oracle Integration.
- In the navigation pane,
click Settings, then
Certificates.
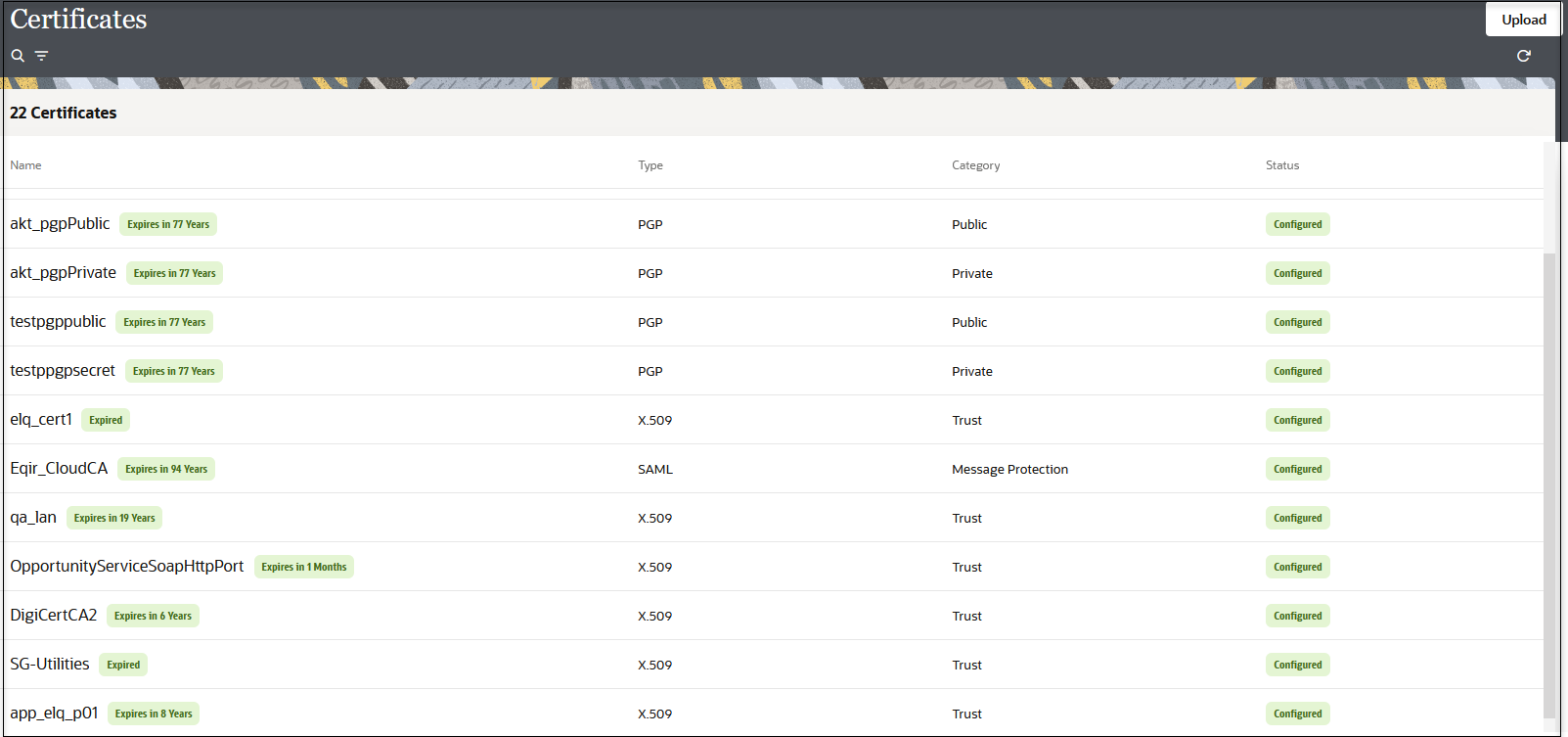
All certificates currently uploaded to the trust store are displayed on the Certificates page.
- Click Filter
 to filter by name, certificate expiration date, status, type, category,
and installation method (user-installed or system-installed). Certificates
installed by the system cannot be deleted.
to filter by name, certificate expiration date, status, type, category,
and installation method (user-installed or system-installed). Certificates
installed by the system cannot be deleted.
- Click Upload at the top of the page.
The Upload certificate panel is displayed.
- Enter an alias name and optional description.
- In the Type field, select the certificate type. Each certificate type enables Oracle Integration to connect with external services.
X.509 (SSL transport)
- Select a certificate category.
- Trust: Use this option to upload a
trust certificate.
- Click Choose File, then
select the trust file (for example,
.ceror.crt) to upload.
- Click Choose File, then
select the trust file (for example,
- Identity: Use this option to upload a
certificate for two-way SSL communication.
- Click Choose File, then
select the keystore file (
.jks) to upload. - Enter the comma-separated list of passwords
corresponding to key aliases.
Note
When an identity certificate file (.jks) contains more than one private key, all the private keys must have the same password. If the private keys are protected with different passwords, the private keys cannot be extracted from the keystore. - Enter the password of the keystore being imported.
- Click Choose File, then
select the keystore file (
- Click Upload.
- Trust: Use this option to upload a
trust certificate.
SAML (Authentication & Authorization)
- Note that Message Protection is automatically selected as the only available certificate category and cannot be deselected. Use this option to upload a keystore certificate with SAML token support. Create, read, update, and delete (CRUD) operations are supported with this type of certificate.
- Click Choose File, then select the
certificate file (
.ceror.crt) to upload. - Click Upload.
PGP (Encryption & Decryption)
- Select a certificate category. Pretty Good Privacy (PGP) provides
cryptographic privacy and authentication for communication. PGP is used for
signing, encrypting, and decrypting files. You can select the private key to use
for encryption or decryption when configuring the stage file action.
- Private: Uses a private key of the
target location to decrypt the file.
- Click Choose File, then select the PGP file to upload.
- Enter the PGP private key password.
- Public: Uses a public key of the
target location to encrypt the file.
- Click Choose File, then select the PGP file to upload.
- In the ASCII-Armor Encryption
Format field, select Yes
or No.
- Yes shows the format of the encrypted message in ASCII armor. ASCII armor is a binary-to-textual encoding converter. ASCII armor formats encrypted messaging in ASCII. This enables messages to be sent in a standard messaging format. This selection impacts the visibility of message content.
- No causes the message to be sent in binary format.
- From the Cipher Algorithm
list, select the algorithm to use. Symmetric-key algorithms for
cryptography use the same cryptographic keys for both encryption
of plain text and decryption of cipher text. The following
supported cipher algorithms are FIPS-compliant:
- AES128
- AES192
- AES256
- TDES
- Click Upload.
- Private: Uses a private key of the
target location to decrypt the file.
Signing key
A signing key is a secret key used to establish trust between applications. Signing keys are used to sign ID tokens, access tokens, SAML assertions, and more. Using a private signing key, the token is digitally signed and the server verifies the authenticity of the token by using a public signing key. You must upload a signing key to use the OAuth Client Credentials using JWT Client Assertion and OAuth using JWT User Assertion security policies in REST Adapter invoke connections. Only PKCS1- and PKCS8-formatted files are supported.
- Select Public or Private.
- Click Choose file to upload a key file.
If you selected Private, and the private key is encrypted, a field for entering the private signing key password is displayed after key upload is complete.
- Enter the private signing key password. If the private signing key is not encrypted, you are not required to enter a password.