Oracle Database Use Cases
The Database Tools service allows you to create connections to Oracle database systems running in Oracle Cloud Infrastructure. Connections work with Autonomous Database (ADB) Shared, ADB Dedicated, Oracle Base Database (VM, BM, and Exadata DB Systems), and customer-managed Oracle databases running on OCI compute instances.
The following are some examples of using Database Tools connections with different Oracle Database configurations.
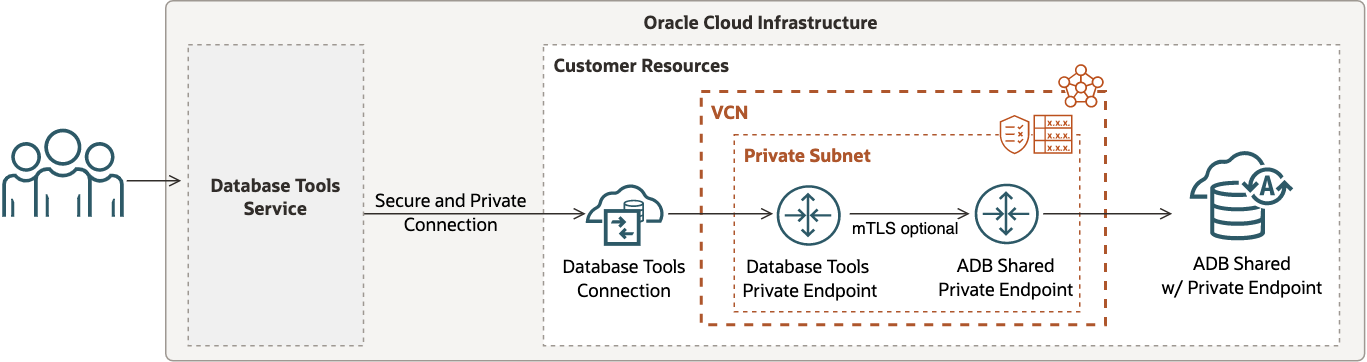
ADB Shared with Private Endpoint Access
When ADB on shared Exadata infrastructure is configured to restrict network access to the database using a private endpoint, then a Database Tools private endpoint should be setup in a subnet such that network traffic can be routed from the Database Tools service to the private endpoint associated with ADB.
In this scenario:
- There are two distinct private endpoints for routing traffic through the same virtual cloud network (VCN).
- The setup requires configuration of route tables and security lists or network security groups.
- Mutual TLS (mTLS) authentication is optional unless marked as required by ADB.
- A Database Tools private endpoint can be setup in the same subnet or a different subnet (beside the ADB private endpoint). However, using isolated subnets may require additional VCN configuration to allow traffic to be routed accordingly.
- Secrets stored in a vault may include the wallet (if mTLS is required) and must include the database password.
The following figure shows one possible way to configure your Database Tools connection for this use case.
See Getting Started with Autonomous Database for more information about ADB.
See Creating a Connection for more information about creating Database Tools connections.
See Using Private Endpoints with Database Tools for more information about Database Tools private endpoints.
Familiarity with the following topics may also be useful when configuring a VCN.
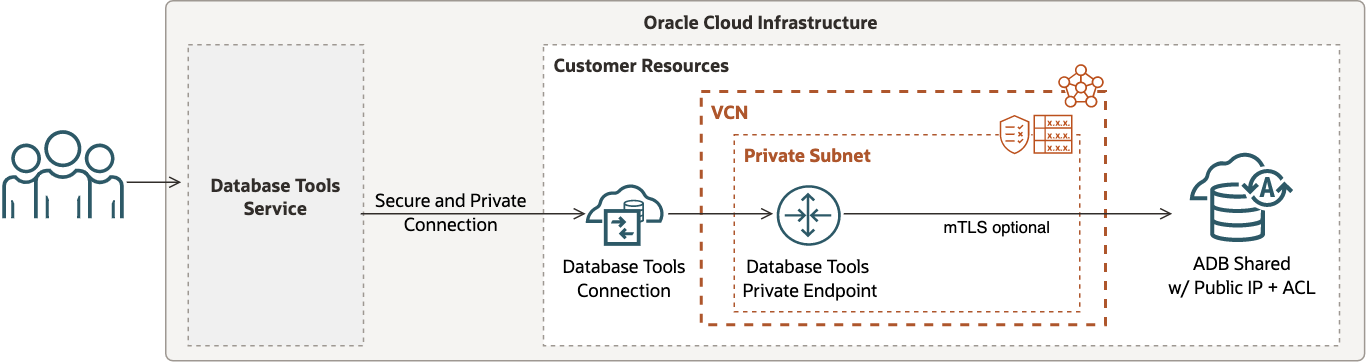
ADB Shared with Public IP and ACL
When ADB on shared Exadata infrastructure is configured to restrict network access to the database using a public IP address with an access control list (ACL), then a Database Tools private endpoint should be setup in a subnet such that network traffic can be routed from the Database Tools service to ADB.
In this scenario:
- There is one private endpoint for routing Database Tools traffic through the VCN.
- The setup requires configuration of a route table and security list or network security group.
- mTLS authentication is optional unless marked as required by ADB.
- Configuration of ACL Rules is required to allow access to ADB through the Database Tools private end.
- Secrets stored in a vault may include the wallet (if mTLS is required) and must include the database password.
The following figure shows one possible way to configure your Database Tools connection for this use case.
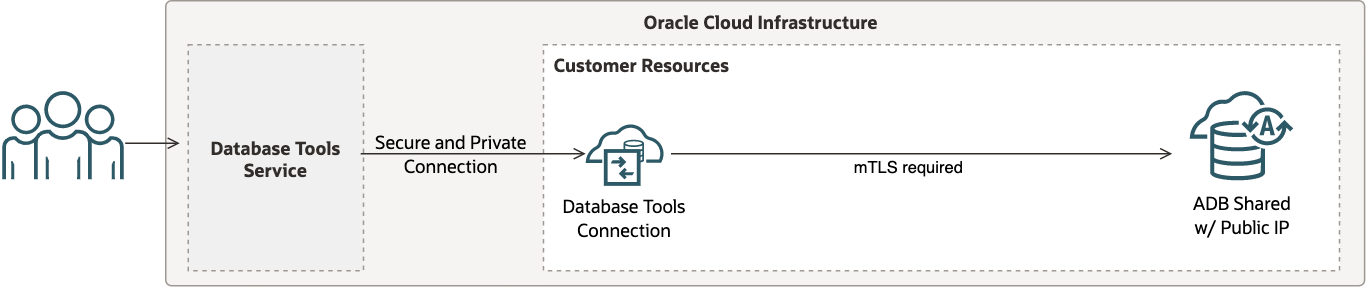
ADB Shared with Public IP
When ADB on shared Exadata infrastructure is configured with a public IP address for secure access from everywhere, then a Database Tools private endpoint is not required to create a connection.
In this scenario:
- mTLS authentication is required by ADB.
- Secrets stored in a vault must include the wallet and database password.
The following figure shows one possible way to configure your Database Tools connection for this use case.
See Getting Started with Autonomous Database for more information about ADB.
See Creating a Connection for more information about creating database tools connections.
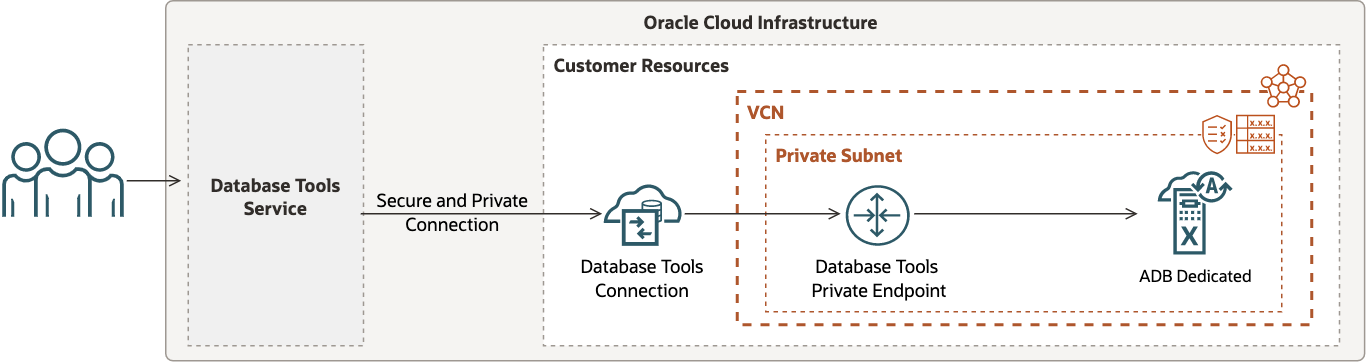
ADB Dedicated with Private IP
When ADB on dedicated Exadata infrastructure is configured to restrict network access to the database using a private subnet, then a Database Tools private endpoint should be setup in a subnet such that network traffic can be routed from the Database Tools service to the the target database.
In this scenario:
- There is one Database Tools private endpoint for routing traffic through the VCN.
- The setup requires configuration of a route table and security list or network security group for the subnet.
- A Database Tools private endpoint can be setup in the same subnet or a different subnet (as ADB Dedicated). However, using isolated subnets may require additional VCN configuration to allow traffic to be routed accordingly.
- Secrets stored in a vault may include the wallet (if mTLS is required) and must include the database password.
A wallet must be provided when the use of mutual TLS (mTLS) authentication is required, or when TLS authentication is used and the database returns a certificate not signed by a trusted certificate authority.
The following figure shows one possible way to configure your Database Tools connection for this use case.
See Autonomous Database on Dedicated Exadata Infrastructure for more information about ADB Dedicated.
See Creating a Connection for more information about creating Database Tools connections.
See Using Private Endpoints with Database Tools for more information about Database Tools private endpoints.
Familiarity with the following topics may also be useful when configuring a VCN.
Oracle Base Database (VM, BM)
When an Oracle DB System (VM or BM) is configured to restrict network access using a private subnet, then a Database Tools private endpoint should be setup in a subnet such that network traffic can be routed from the Database Tools service to the target database.
In this scenario:
- There is one Database Tools private endpoint for routing traffic through the VCN.
- The setup requires configuration of a route table and security list or network security group for the subnet.
- A Database Tools private endpoint can be setup in the same subnet or a different subnet (as the DB system). However, using isolated subnets may require additional VCN configuration to allow traffic to be routed accordingly.
- Secrets stored in a vault may include the wallet (if mTLS is required) and must include the database password.
A wallet must be provided when the use of mTLS authentication is required, or when TLS authentication is used and the database returns a certificate not signed by a trusted certificate authority.
The following figure shows one possible way to configure your Database Tools connection for this use case.
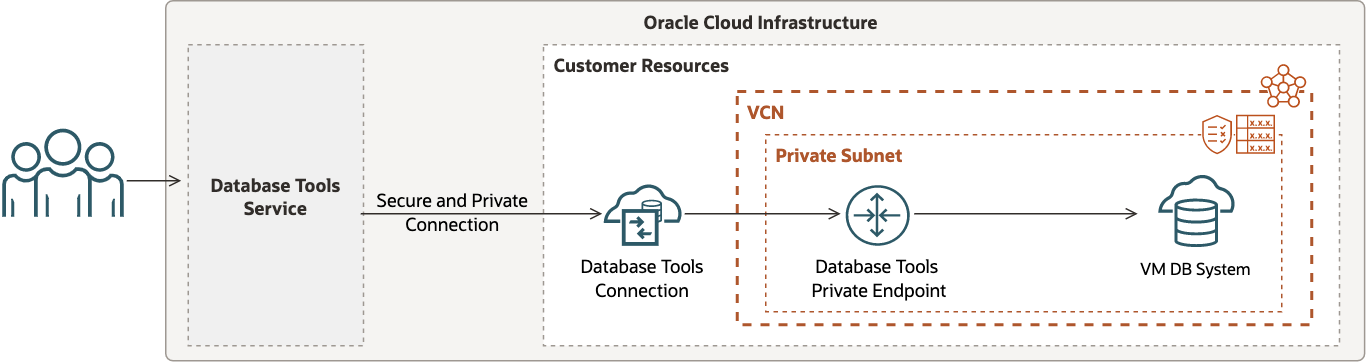
See About Oracle Base Database Service for more information about Oracle DB systems.
See Creating a Connection for more information about creating database tools connections.
See Using Private Endpoints with Database Tools for more information about Database Tools private endpoints.
Familiarity with the following topics may also be useful when configuring a VCN.
Oracle Database (Customer Managed)
When a customer-managed Oracle database is configured with a public IP address for access from everywhere, then a Database Tools private endpoint is not required to create a connection. This configuration is supported but is not considered best practice.
In this scenario:
- The setup requires configuration of a route table and security list or network security group for the subnet.
- Firewall rules of the database server should allow traffic to reach the database.
- A secret stored in a vault must include the database password.
A wallet must be provided when the use of mTLS authentication is required, or when TLS authentication is used and the database returns a certificate not signed by a trusted certificate authority.
The following figure shows one possible way to configure your Database Tools connection for this use case.
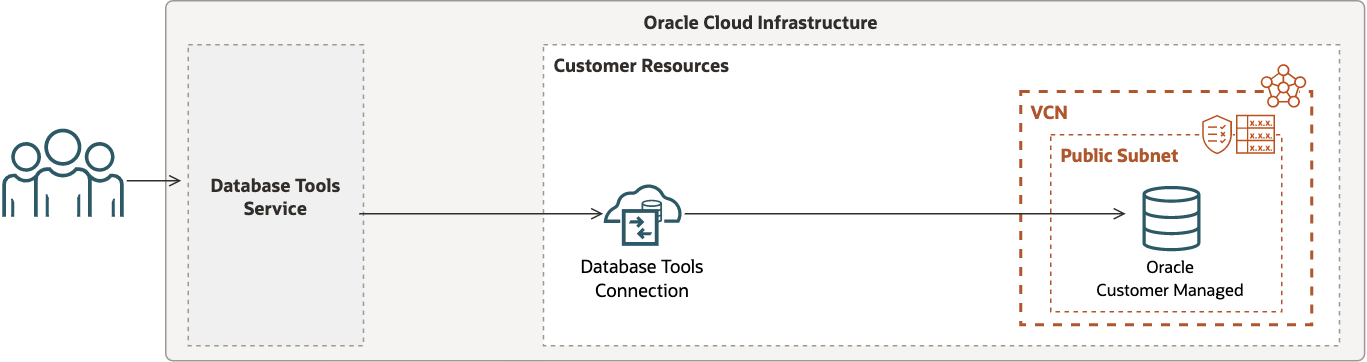
See Creating a Connection for more information about creating database tools connections.