Managing User Access to Applications Environments
Set up users to work with applications environments in the Oracle Cloud Console.
This topic explains how you can set up additional users to work with applications environments that are managed in the Oracle Cloud Console. If you need to add users to work in your application, see your application documentation.
Applications environment management integrates with the Identity and Access Management Service (IAM) service for authentication and authorization. IAM uses policies to grant permissions to groups. Users have access to resources (such as applications environments) based on the groups that they belong to.
The user entered during the tenancy creation step is the default administrator of the tenancy. The default administrator can perform all tasks for all services, including create groups, policies, and users to give access to the resources.
This topic provides the basic procedures for creating specific user types in your account to get you started with application environment management. For full details on managing users in the Oracle Cloud Console, see Managing Users.
Add a Tenancy Administrator
You can add a tenancy administrator by creating a user and adding them to the tenancy Administrators group. Members of the Administrators group have access to all features and services in the Oracle Cloud Console.
To add a tenancy administrator:
- On the Oracle Cloud Console home page, click Add a user to your tenancy. The list of Users in the current domain is displayed.
- Click Create user.
- Enter the user's First name and Last name.
- To have the user log in with their email address:
- Leave the Use the email address as the username check box selected.
- In the Username / Email field, enter the email address for the user account.
or
To have the user log in with their user name:- Clear the Use the email address as the username check box.
- In the Username field, enter the user name that the user is to use to log in to the Console.
- In the Email field, enter the email address for the user account.
- Under Select groups to assign this user to, select the check box for Administrators.
- Click Create.
A welcome email is sent to the address you entered for the new user. The new user can follow the account activation instructions in the email to sign in and start using the tenancy.
Add a User with Limited Access
For users who shouldn't have full administrator access, you can create policies that define the allowed access. This process consists of four steps:
- Find the identity domain.
- Create a group.
- Create a policy that grants the group appropriate access to the resources.
- Create a user and add them to the group.
You can create policies that grant different levels of access for different groups. For example, you can create a policy that grants full environment management permissions for a group called Environment-Admins. You can create a second policy that grants only monitoring capabilities for a group called Environment-Viewers.
The following tasks walk you through creating a group, policy, and user in the Identity and Access Management (IAM) service. Either the default administrator can perform these tasks, or another user that has been granted access to administer IAM.
An identity domain is a container for managing users and roles, federating and provisioning of users, secure application integration through Oracle Single Sign-On (SSO) configuration, and OAuth administration. When you write a policy, you must identify which identity domain the group belongs to.
To find the identity domains in your tenancy:
Open the navigation menu, under Infrastructure, click Identity & Security to expand the menu, and then under Identity, click Domains.
All tenancies include a Default domain. Your tenancy might also include the OracleIdentityCloudService domain, as well as other domains created by your organization.
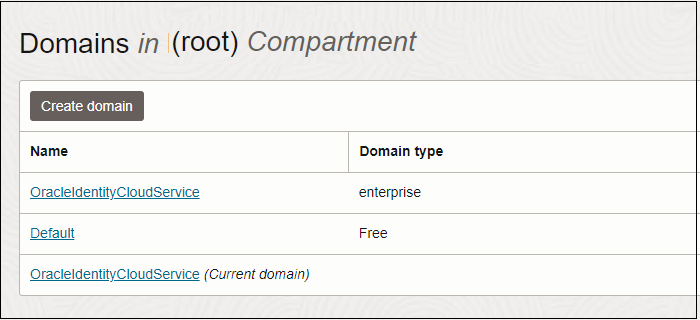
- Navigate to the Groups page of your identity domain: Open the navigation menu, under Infrastructure, click Identity & Security to expand the menu, and then under Identity, click Domains.
- Click the domain where you want to add the group. In this example, we'll add the group to the Default domain.
- Under the list of resources on the left, click Groups.
- Click Create group.
- Enter the following:
- Name: A unique name for the group, for example, Environment-Admins. The name must be unique across all groups in your tenancy. You cannot change this later.
- Description: A friendly description. You can change this later if you want to.
- Advanced options - Tags: Optionally, you can apply tags. If you have permissions to create a resource, you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure if you should apply tags, skip this option (you can apply tags later) or ask your administrator.
- Click Create.
Before you create the policy, you'll need to know the correct value for your application's resource-type. The resource-type is what the policy grants access to. See Applications Services Policy Reference to find the correct resource-type for your application.
-
If you are still on the Groups page from the preceding step, click Domains in the breadcrumb links at the top of the page. On the Domains page, click Policies on the left side of the page.
Otherwise, open the navigation menu, under Infrastructure, click Identity & Security to expand the menu, and then under Identity, click Policies. The list of policies is displayed.
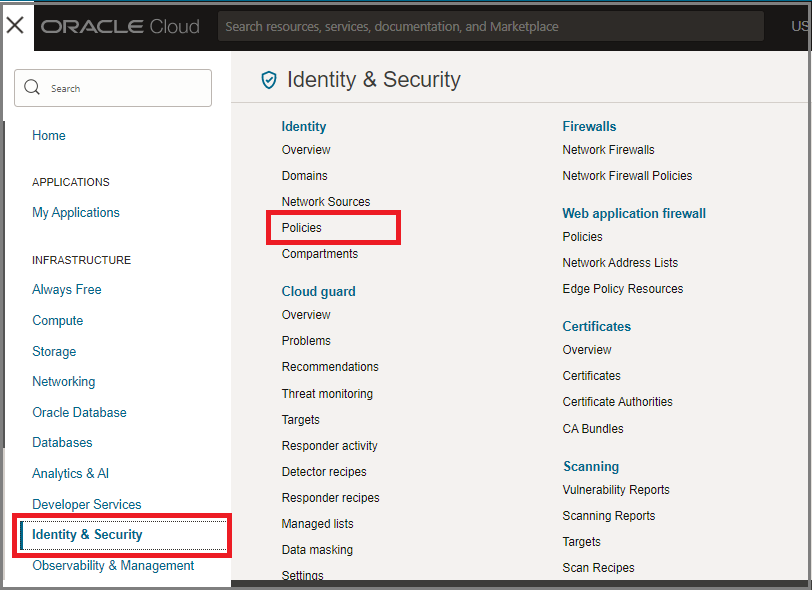
- Click Create Policy.
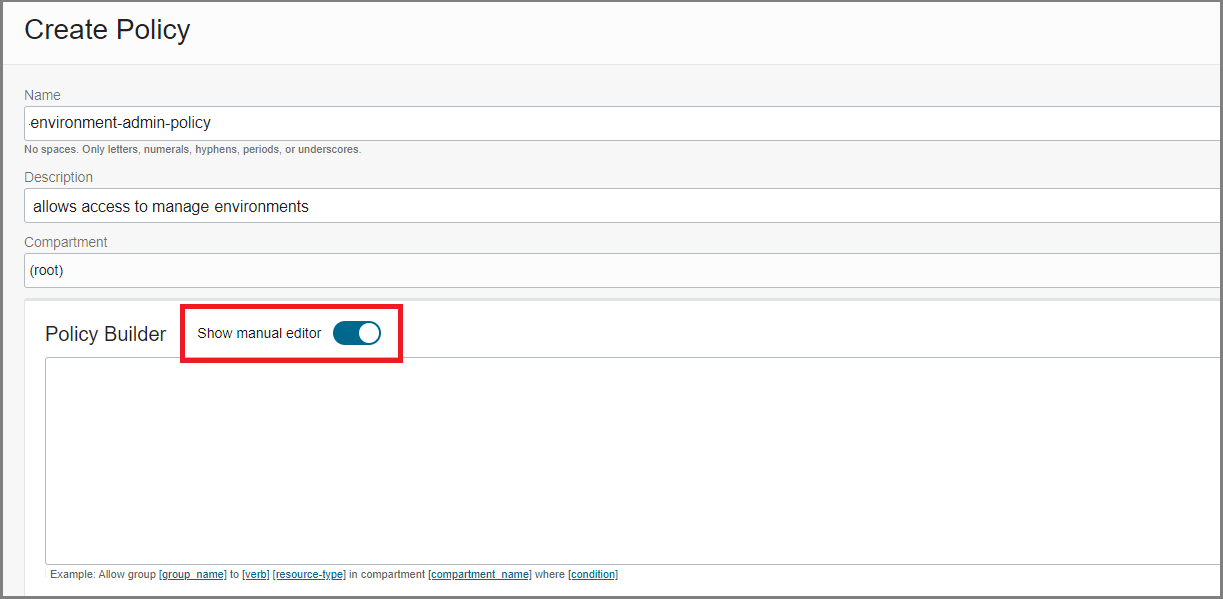
- Enter the following:
- Name: A unique name for the policy. The name must be unique across all policies in your tenancy. You cannot change this later.
- Description: A friendly description. You can change this later if you want to.
- Compartment: Ensure that the tenancy (root compartment) is selected.
- On the Policy Builder, toggle on Show manual editor
to display the text box for free-form text entry.
-
Enter the policy statements to grant access to the required resources.
Policies follow the format:
Allow '<identity_domain_name>'/'<group-name>' to <verb> <resource-type> in <location>where
<identity-domain-name> is the identity domain where the group resides.
<your-group-name> is the group you created in a previous step.
<application-name> is the appropriate IAM resource name for your application. For a list of the resource names, see Applications Services Policy Reference.
<location> can be either a compartment name or "tenancy" to indicate the permission is granted to all compartments in the tenancy.
For example, the statements to create an environment administrator for Maxymiser are:
Allow group 'Default'/'Environment-Admins' to manage maxymiser-environment-family in tenancy Allow group 'Default'/'Environment-Admins' to read organizations-subscriptions in tenancy Allow group 'Default'/'Environment-Admins' to read organizations-assigned-subscriptions in tenancy Allow group 'Default'/'Environment-Admins'' to read organizations-subscription-regions in tenancy Allow group 'Default'/'Environment-Admins' to read app-listing-environments in tenancy Allow group 'Default'/'Environment-Admins' to read metrics in tenancy Allow group 'Default'/'Environment-Admins' to inspect domains in tenancy Allow group 'Default'/'Environment-Admins' to read announcements in tenancyNote
If the group is in the Default identity domain, you can omit specifying the <identity-domain-name> in the policy. You only need to specify the group name. For example:Allow group Environment-Admins to manage maxymiser-environment-family in tenancy - Click Create.
You can use the Copy option in the policy sample shown in the Applications Services Policy Reference to copy the set of policy statements. You can then paste the statements into the Policy Builder text box so that you only need to update the values for <identity-domain-name> and <your-group-name>.
- From the Applications Console home page, under Quick Actions, click Add a user to your tenancy.
- Click Create User.
- Enter the user's First name and Last name.
- To have the user log in with their email address:
- Leave the Use the email address as the username check box selected.
- In the Username / Email field, enter the email address for the user account.
or
To have the user log in with their user name:- Clear the Use the email address as the username check box.
- In the Username field, enter the user name that the user is to use to log in to the Console.
- In the Email field, enter the email address for the user account.
- To assign the user to a group, select the check box for each group that you want to assign to the user account.
- Click Create.
Applications Services Policy Reference
The applications services shown here support self-service environment provisioning and management. For help writing policies for applications services that do not support self-service provisioning, see Adding Oracle Cloud Console Users.
The following sections provide sample policies that you can use to create an environment administrator role and an environment viewer role. To create a user with the access granted through these policies, you can copy and paste the provided policy for your service, substituting your group name. For details, see the Tip in the Create the policy task above.
Permission Level
The permission level is specified by the verb in the statement. To give another user access to interact with your environments in the Oracle Cloud Console, use one of the following verbs in your policy statements:
-
manage- allows the user to perform all management tasks for an environment, including create and delete (when supported). -
use- allows the user to update an existing environment; user can't create or delete an environment. -
read- allows the user to view all information about the environment. -
inspect- allows the user to list the environments only; user can't view the details pages.
For more information on the operations permitted by each of these verbs, see Applications Environment Management IAM Policy Reference.
Required Statements
Both the environment administrator and environment viewer roles require access to the
application environment resources. The administrator requires manage
permissions, while the viewer only needs read permissions. In addition,
both roles require permissions to read applications subscriptions.
Required Statements for Environment Administrator
The environment administrator can perform all tasks required to create and manage environments. The administrator can also view the subscriptions in your tenancy and access metrics data. See Application-Specific Policy Examples for the <application> value for your application.
Allow group '<identity-domain-name>'/'<your-group-name>' to manage <application>-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Details for each policy statement:
| Policy Statement | What It's For |
|---|---|
|
Grants full management permissions for the specified application environments. Includes access to compliance documentation. |
|
Grants permissions to read subscriptions-related information to access your applications subscriptions in the Console. Required for viewing your subscriptions; must be at the tenancy level. |
|
Grants access to metrics charts and metrics data for OCI resources. |
|
Grants access to read announcements. |
|
Grants access to list identity domains. |
Required Statements for Environment Viewer
This user can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also view the subscriptions in your tenancy and access metrics data. See Application-Specific Policy Examples for the <application> value for your application.
Allow group '<identity-domain-name>'/'<your-group-name>' to read <application>-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy
The only difference between this policy and the administrator policy is the
read verb for the environment-family
resource.
Application-Specific Policy Examples
Use the examples in this section to create environment administrator and environment viewer roles for your application.
B2C Service Administrator or Viewer
The B2C Service administrator or viewer can view details and monitor environments in the Oracle Cloud Console. The administrator or viewer can also access metrics data and view the subscriptions and applications environments in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read rnow-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancyCommerce Cloud Environment Administrator
The Commerce Cloud Environment Administrator can perform all tasks required to create and manage Commerce environments. The Commerce Cloud Administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage commercecloud-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Commerce Cloud Environment Viewer
The Commerce Cloud environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read commercecloud-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancyDigital Assistant Platform for SaaS Environment Administrator or Viewer
The Digital Assistant Platform for SaaS Environment Administrator or Viewer can view details and monitor environments in the Oracle Cloud Console. The administrator or viewer can also access metrics data and view the subscriptions and applications environments in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read odanative-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancyEPM Planning Environment Administrator
The EPM Planning Environment Administrator can perform all tasks required to create and manage EPM Planning environments. The EPM Planning Administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage epm-planning-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy EPM Planning Environment Viewer
The EPM Planning environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read epm-planning-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancyField Service Administrator or Viewer
The Field Service administrator or viewer can view details and monitor environments in the Oracle Cloud Console. The administrator or viewer can also access metrics data and view the subscriptions and applications environments in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read fieldservicetoa-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancyFinancial Services Accounting Standards for Banking Cloud Service Administrator
The Financial Services Accounting Standards for Banking Cloud Service administrator can perform all tasks required to create and manage environments. The Financial Services Accounting Standards for Banking Cloud Service administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage FSGBUASCS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Accounting Standards for Banking Cloud Service Viewer
The Financial Services Accounting Standards for Banking Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read FSGBUASCS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Analytical Applications Cloud Service Administrator
The Financial Services Analytical Applications Cloud Service Administrator can perform all tasks required to create and manage environments. The Financial Services Analytical Applications Cloud Service Administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage FSGBUERF-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Analytical Applications Cloud Service Viewer
The Financial Services Analytical Applications Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read FSGBUERF-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Climate Change Analytics Cloud Service Administrator
The Financial Services Climate Change Analytics Cloud Service administrator can perform all tasks required to create and manage environments. The Financial Services Climate Change Analytics Cloud Service administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage FSGBUCCA-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Climate Change Analytics Cloud Service Viewer
The Financial Services Climate Change Analytics Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read FSGBUCCA-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Crime and Compliance Management Anti Money Laundering Cloud Service Administrator
The Financial Services Crime and Compliance Management Anti Money Laundering Cloud Service administrator can perform all tasks required to create and manage environments. The Financial Services Crime and Compliance Management Anti Money Laundering Cloud Service administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage FSGBUFCCMAMLCS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Crime and Compliance Management Anti Money Laundering Cloud Service Viewer
The Financial Services Crime and Compliance Management Anti Money Laundering Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read FSGBUFCCMAMLCS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Insurance Cloud Service Administrator
Financial Services Insurance Cloud Service administrator can perform all tasks required to create and manage environments. The Financial Services Insurance Cloud Service administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage FSGBUINS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Insurance Cloud Service Viewer
The Financial Services Insurance Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read FSGBUINS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Profitability and Balance Sheet Management Cloud Service Administrator
Financial Services Profitability and Balance Sheet Management Cloud Service administrator can perform all tasks required to create and manage environments. The Financial Services Profitability and Balance Sheet Management Cloud Service administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage FSGBUPBSM-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Financial Services Profitability and Balance Sheet Management Cloud Service Viewer
The Financial Services Profitability and Balance Sheet Management Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read FSGBUPBSM-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Integration for Oracle SaaS Environment Administrator or Viewer
The Integration for Oracle SaaS Environment administrator or viewer can view details and monitor environments in the Oracle Cloud Console. The administrator or viewer can also access metrics data and view the subscriptions and applications environments in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read integrationsub-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancyMaxymiser Environment Administrator
The Maxymiser Administrator can perform all tasks required to create and manage environments. The Maxymiser Administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage maxymiser-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Maxymiser Environment Viewer
The Maxymiser environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read maxymiser-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Student Financial Planning Cloud Service Environment Administrator
The Student Financial Planning Cloud Service environment administrator can perform all tasks required to create and manage environments. The administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage OSFPCS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Student Financial Planning Cloud Service Environment Viewer
The Student Financial Planning Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read OSFPCS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Transportation and Global Trade Management Cloud Environment Administrator
The Transportation and Global Trade Management Cloud Administrator can perform all tasks required to create and manage environments. The Transportation and Global Trade Management Cloud Administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage OTMGTM-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Transportation and Global Trade Management Cloud Environment Viewer
The Transportation and Global Trade Management Cloud environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read OTMGTM-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Utilities Work and Asset Cloud Service Environment Administrator
The Utilities Work and Asset Cloud Service environment administrator can perform all tasks required to create and manage environments. The administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage UGBUWACS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Utilities Work and Asset Cloud Service Environment Viewer
The Utilities Work and Asset Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read UGBUWACS-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Warehouse Management Cloud Service Environment Administrator
The Oracle Warehouse Management Cloud Service administrator can perform all tasks required to create and manage environments. The administrator can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to manage LOGFIRE-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy Warehouse Management Cloud Service Environment Viewer
The Warehouse Management Cloud Service environment viewer can view details and monitor the environments in the Oracle Cloud Console. This role can't make any updates. The environment viewer can also access metrics data and view the subscriptions, applications environments, and identity domains in your tenancy.
Example policy to copy and paste:
Allow group '<identity-domain-name>'/'<your-group-name>' to read LOGFIRE-environment-family in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-assigned-subscriptions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read organizations-subscription-regions in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read app-listing-environments in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read metrics in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to inspect domains in tenancy
Allow group '<identity-domain-name>'/'<your-group-name>' to read announcements in tenancy