Enable Autonomous AI Databases & Full Feature Support
Ops Insights allows you to perform advanced and basic collections on your Autonomous AI Databases via a private endpoint or through secure access from anywhere. These connection methods allows Ops Insights to connect to the database directly and enable Full Features collection, which includes SQL Explorer and ADDM Spotlight.
Before you Begin
Exadata Database Service on Dedicated Infrastructure Autonomous AI Databases (ADB-D), and Exadata Database Service Serverless (ADB-S) are supported using private endpoints. Exadata Cloud@Customer Autonomous AI Databases (ADB@ExaCC) are supported using Management Agents.
To enable one or more Autonomous AI Databases (including Autonomous Exadata Cloud@Customer databases) for Ops Insights, log in to OCI and do the following:
Once enabled the data may take up to 24 hours to appear.
- Open the navigation menu and click Observability and Management. Under Ops Insights, click Administration and then Database Fleet.The Database Fleet Administration page displays.
- Click Add Databases. The Add Databases to Ops Insights dialog displays.
- Under Telemetry click on Cloud Infrastructure. Under cloud database type select Oracle Autonomous AI Databases.
- Select the Compartment that contains the database that you want to enable for Ops Insights. Optionally, if there are many databases and you know which ones you want to enable, you can filter the returned results based on database type.
- Select one or more Autonomous AI Databases to enable. In this step you can also
setup the collection type for your Autonomous AI Database, by default the
check mark option under Full features set is selected. This
allows for Full Features collection, deselecting this will limit to Basic
Features (Capacity Planning).
Note
For Exadata Cloud @Customer Autonomous AI Databases full features are checked by default and cannot be unchecked. The basic feature set is not available for these databases.Set connection properties to setup the Full Feature connection. This opens the Set credentials window. Depending on the Autonomous AI Database type, you will see the following connection options:- For an IAM credential (ADB-D and ADB-S): Ensure the IAM
connection prerequisites mentioned above have been completed and
follow these steps:
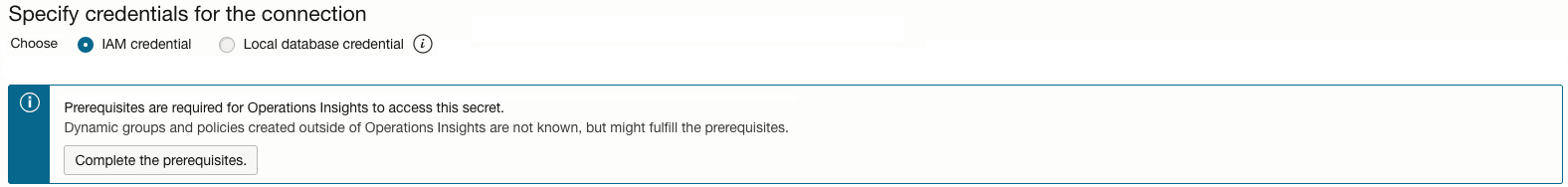
- Select the IAM Credential radio button
- Optional, if prompted complete the missing prerequisite policies
- Enter the connection string for IAM
- Click on Save changes
- Ensure that the Prerequisites field shows Complete for all Autonomous AI Databases to be added
- For a Local credential follow these steps (ADB-D and
ADB-S):
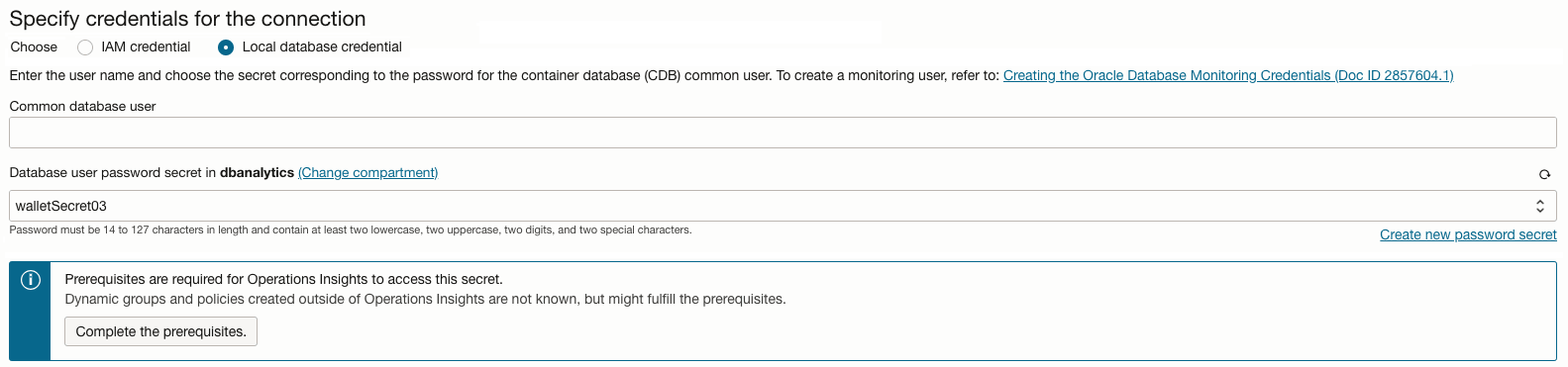
- Select the Local Credential radio button
- Enter the Database user name
- Enter the Database user password secret and
verify the compartment chosen
Note
If you wish to enter a new password secret click on Create password Secret and enter the name, description, compartment, vault, encryption key, and user password. Once entered click onCreate password secret. - Enter the Connection string
- Click on Save changes
- Ensure that the Prerequisites field shows Complete for all Autonomous AI Databases to be added
- For Exadata Cloud @Customer Autonomous AI Databases:
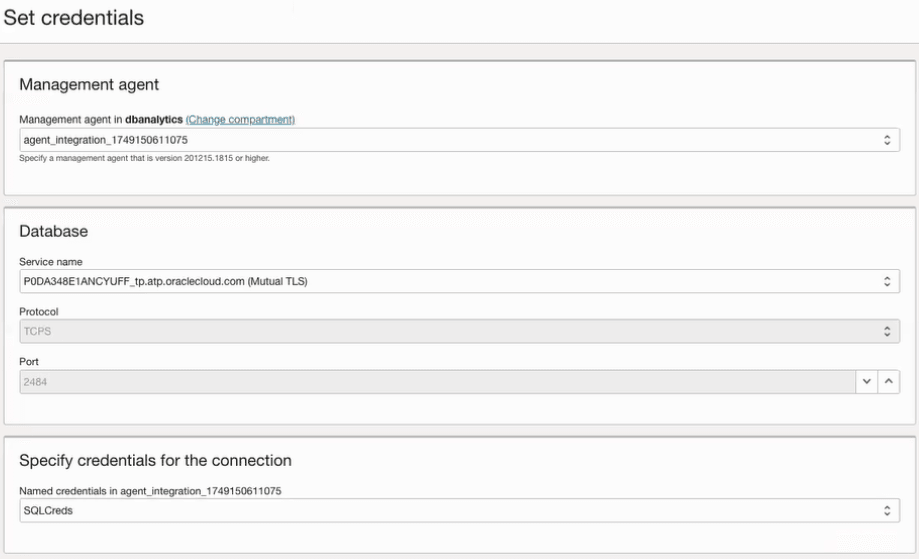
- Select the Management agent
- Select the Database service name connection string. The Protocol and Port will be automatically filled.
- Specify the named credentials to be used for
the connection, these credentials are created by the Agent
and do not reside within Ops Insights.
- For TLS connections, create a credential of type Database credential. This type of credential will not use the wallet to connect.
- For Mutual TLS (TCPS), create an Database Credential for Autonomous AI Database (with mTLS) credential. This type of credential needs access to the database password in the vault as well as the Autonomous AI Database wallet.
NoteIf you do not have the Management Agent Credentials (MACS) set, you can set them in this step by following these substeps:
The type of credential you create must directly relate to the service name you choose when enabling the database.- Determine the credential type to use (TLS or MTLS), and then click on Create Named Credential, this action will take you from Ops Insights into the Agent details page.
- In the Agent details page, click on the More Actions drop down, and then click on Managed Named Credentials.
- To add a new credential click on Add new Named Credential, enter the Credential Name, Description and Credential Type (Database Credential or Database Credentials for Autonomous AI Database with JKS encryption) and click Save.
For more information see: Management Agent Source Credentials.
- For an IAM credential (ADB-D and ADB-S): Ensure the IAM
connection prerequisites mentioned above have been completed and
follow these steps:
- Once you have selected the Autonomous AI Databases, and configured the feature type (basic or full) and the connection type for Full Features, click Add Databases. This will bring you to the main Database Fleet page where you can monitor the progress for the newly added databases. Once the state shows as Active the process has successfully completed.
Upgrade an Existing Autonomous AI Database to Full Features Collection
- Log into OCI, navigate to Observability and Management, then Ops Insights and click on Administration.
- Under Administration select Database Fleet. This will show you the Database Fleet Administration table where all your databases that have an enabled Ops Insights state are displayed. Autonomous AI Databases with an Active state and a Basic Feature Set are eligible for Full Feature enabling.
- Select an Autonomous AI Database you wish to enable the advanced features for and click on the three dots menu located at the right end of the table. From the menu select Enable Full Feature Set.
- In the Enable Full Feature Set window
select either IAM or Local credentials.
Note
Databases configured with ACL restricted or private endpoint access, and ADB-D require private endpoint connections.The connect string information is automatically filled out by the service.
If you have not previously created the policies to generate Autonomous AI Database wallets click on Complete the prerequisites, and then click on Apply.
Click Enable.Note
ADB-D databases require new private endpoints that have DNS proxy enabled selected. If this parameter is not selected, you will not see existing private endpoints in the drop down menu for these types of databases. - In the Database Fleet Administration table, the Autonomous AI Database under the Ops Insights State row will now show Full, advanced features are now being collected.