Getting Started with Oracle Exadata Database Service on Exascale Infrastructure Deployment
After completing the preparation tasks in Preparing for Oracle Exadata Database Service on Exascale Infrastructure, get started with deploying your Oracle Exadata Database Service on Exascale Infrastructure system following these procedures.
- Regional Availability for Exadata Database Service on Exascale Infrastructure
Learn what OCI regions support Oracle Exadata Database Service on Exascale Infrastructure (ExaDB-XS). - Tagging Oracle Exadata Database Service on Exascale Infrastructure Resources
Tagging is a powerful foundational service for Oracle Cloud Infrastructure (OCI) that enables users to search, control access, and do bulk actions on a set of resources based on the tag. - Restarting a VM for Planned Maintenance
To facilitate maintenance of Oracle Exadata Database Service on Exascale Infrastructure virtual machines (VM), Oracle notifies you of planned VM restarts. - Connecting to an Oracle Exadata Database Service on Exascale Infrastructure VM
Learn how to connect to an Oracle Exadata Database Service on Exascale Infrastructure virtual machine (VM) using SSH or SQL Developer. - Capacity Limits for Exadata Database Service on Exascale Infrastructure
To understand the scalability features and resource capacity of the ExaDB-XS service, review these tables and lists. - Best Practices for Oracle Exadata Database Service on Exascale Infrastructure VMs
Oracle recommends that you follow these best practice guidelines to ensure the manageability of your Oracle Exadata Database Service on Exascale Infrastructure virtual machines (VMs).
Regional Availability for Exadata Database Service on Exascale Infrastructure
Learn what OCI regions support Oracle Exadata Database Service on Exascale Infrastructure (ExaDB-XS).
In the tables in this topic, you can find which Oracle Cloud Infrastructure (OCI) regions offer Exadata Database Service on Exascale Infrastructure.
Where the region supports multiple availability domains (AD), only a single availability domain is supported with Oracle Exadata Database Service on Exascale Infrastructure.
Asia Pacific (APAC)
| Region Name | Region Key | Region Location |
|---|---|---|
|
Australia East |
SYD |
Sydney, Australia |
|
Australia Southeast |
MEL |
Melbourne, Australia |
|
India South |
HYD |
Hyderabad, India |
|
India West |
BOM |
Mumbai, India |
|
Japan Central |
KIX |
Osaka, Japan |
|
Japan East |
NRT |
Tokyo, Japan |
|
Singapore |
SIN |
Singapore, Singapore |
|
Singapore West |
XSP |
Singapore, Singapore |
|
South Korea Central |
ICN |
Seoul, South Korea |
|
South Korea North |
YNY |
Chuncheon, South Korea |
Europe, Middle East, Africa (EMEA)
| Region Name | Region Key | Region Location |
|---|---|---|
|
France Central |
CDG |
Paris, France |
|
France South |
MRS |
Marseille, France |
|
Germany Central |
FRA |
Frankfurt, Germany |
|
Saudi Arabia West |
JED |
Jeddah, Saudi Arabia |
|
South Africa Central |
JNB |
Johannesburg, South Africa |
|
Switzerland North |
ZRH |
Zurich, Switzerland |
|
UAE Central |
AUH |
Abu Dhabi, UAE |
|
UK South |
LHR |
London, United Kingdom |
|
UK West |
CWL |
Newport, United Kingdom |
|
Switzerland North |
ZRH |
Zurich, Switzerland |
Latin America (LATAM)
| Region Name | Region Key | Region Location |
|---|---|---|
|
Brazil East |
GRU |
Sao Paulo, Brazil |
|
Brazil Southeast |
VCP |
Vinhedo, Brazil |
|
Chile Central |
SCL |
Santiago, Chile |
|
Columbia Central |
BOG |
Bogata, Colombia |
North America (NA)
| Region Name | Region Key | Region Location |
|---|---|---|
|
Canada Southeast |
YYZ |
Toronto, Canada |
|
Canada Southeast |
YUL |
Montreal, Canada |
|
US East (Ashburn) |
IAD |
Ashburn, VA |
|
US West |
PHX |
Phoenix, AZ |
|
US West |
SJC |
San Jose, CA |
To provision Exadata Database Service on Exascale resources in a supported region, your OCI tenancy must be subscribed to that region. For example, to provision resources for Exadata Database on Exascale Infrastructure in the East US region, your OCI tenancy must be subscribed to US East (Ashburn). See Managing Regions and Subscribing to an Infrastructure Region for more information.
Tagging Oracle Exadata Database Service on Exascale Infrastructure Resources
Tagging is a powerful foundational service for Oracle Cloud Infrastructure (OCI) that enables users to search, control access, and do bulk actions on a set of resources based on the tag.
Importance of Tagging
Using the Oracle Cloud Infrastructure (OCI) tagging system, you can tag resources in accordance with your organizational scheme, which enables you to group resources, manage costs, and give insights into usage. Tags also help you to build a governance model around security and Maximum Availability Architecture (MAA). As your organization expands its cloud footprint, it can become challenging to keep track of the deployment architectures, security best practices, MAA, application tier, and so on. Using metadata tags to identify workload attributes can help keep up with the security and availability of your tenancy without cost overruns.
To enable customers to manage OCI resources securely and
cost-effectively, Oracle provides a set of predefined tags in line with best
practices for tagging resources. These tags are grouped into two namespaces, the
oracleStandard namespace, and the
OracleApplicationName namespace. You can think of a tag
namespace as a container for your tag keys.
Consider a scenario where your organization has multiple cloud resources such as Exadata Infrastructure, VM Cluster, DB Home, Oracle Database and VM Cluster Networks across multiple compartments in your tenancy. Suppose you want to track these cloud resources for specific purposes, report on them, or take bulk actions. In that case, you will need a system that lets you group these resources based on different criteria such as environment, criticality, target users, application, and so on. You can achieve this by applying appropriate tags to these resources.
For example, you can tag all resources in your development stack with
Oracle-Standard.Environment=Dev or for a business-critical
application stack set Oracle-Standard.Criticality=High or
Extreme. In the event of service disruptions due to various
reasons, you would then be able to quickly identify all OCI resources associated
with an application or business function, or be able to separate critical and
non-critical workloads.
Tagging can also help you to deploy optimized configurations based on
workload attributes identified via tags. For example, database deployments for the
PeopleSoft application require a specific configuration. Setting the
ApplicationName and AppMajorVersion tags while
deploying an Oracle Database can ensure that the database is configured and ready
for the particular application (in this case, PeopleSoft) out of the box.
Moreover, integration with the Cloud Advisor OCI service can provide you with direct, deep insight into how well your cloud services adhere to the corporate guidelines and help your management govern with a vision. See Cloud Advisor Overview for more details.
Adding Tags
You can tag resources using the Oracle Cloud Infrastructure (OCI) console, command-line interface, or SDK.
There are many cloud resources that can be tagged in an Oracle Exadata Database Service on Exascale Infrastructure deployment. Exadata Infrastructure, VM Cluster, DB Home, Oracle Database, Autonomous Exadata VM Cluster, Autonomous Container Database, Autonomous Database, and VM Cluster Networks are some of them. Tags can either be applied while creating the resources or modified later. For example, you can apply tags to an Autonomous Container Database (ACD) while provisioning the ACD or add them later from its Details page.
See How Tagging Works for more details on using tags. Tagging integrates with Oracle Cloud Infrastructure authorization system. You can use IAM policy controls to enable delegation or restriction of tag manipulation. See Authentication and Authorization to learn about the permissions required to work with defined and free-form tags. (Required) Enter introductory text here, including the definition and purpose of the concept.
Tip:
For a "try it out" tutorial that demonstrates implementing tags in Oracle Autonomous Database, refer to Lab 14: Oracle Standard Tags in Oracle Autonomous Database Dedicated for Fleet Administrators Workshop on Oracle LiveLabs.Your tenancies come with a library of standard defined tags that can apply to most resources, which are available from the Namespace field list. These tags are currently available as a set of Tag Namespaces that your governance administrators can deploy. OCI best practices recommend applying these tags to all resources a standard tag can be applied to. Besides reporting and governance, OCI service automation can deliver workload-specific optimizations based on standard tag values. You can also create freeform tags with your own key names in the Key field, and your own values in the Value field. When you have provided your settings, click Add tag to add the tag.
Figure 4-1 Tagging Example
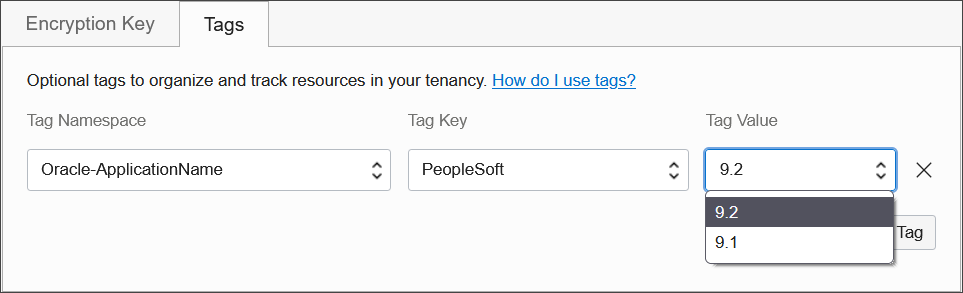
Oracle Standard Tags
Your tenancy governance administrators can deploy the standard defined
tags at the tenancy level. Your administrators can also mark certain tags as
required, thereby enforcing tags on resources in those compartments. The following
are the standard tags defined in the namespace called
OracleStandard. For more information about importing standard
tags, see To import standard tags under the Managing Tag Namespaces section.
Table 4-1 Oracle Standard Defined Tags
| Tag Key | Tag Value Options | Description |
|---|---|---|
|
|
|
Enables tiering of resources in line with corporate application classification standards. Customer governance can use this tag for reporting and ensuring resources are configured as per the guideline for the tier they belong to. For example, a database resource with
|
|
|
|
Denotes a resource lifecycle. In the case of databases, it helps determine consolidation density, database distribution across containers, set maintenance plans, and manage clones. |
|
|
|
An application or database classification tag.
|
|
|
Refer to List of Compliance Regulations for values. |
Denotes one or more compliance regulations that a resource must adhere to. Tag administrators may add values to the list from the OCI Governance and Administration console. Refer to Using Predefined Values for more details. |
|
|
|
Denotes the end users of a resource. Another form of resource classification that helps determine target users and allows governance teams to set corporate standards based on user or application type. |
|
|
|
An approximate count of end-users. This tag helps determine the number of users impacted or the blast radius during an availability or security event. This also helps prioritize recovery efforts in the event of major outages affecting a large number of cloud resources. |
|
|
Free form tag. For example john.smith@example.com or app_support_grp@example.com |
Denotes the email address of the resource owner. |
|
|
|
Identifies the customer's line of business or department that owns or uses the resource. This may help with cost aggregation reports and determining usage across business units.Tag administrators may add relevant values to the list from the OCI Governance and Administration console. Refer to Using Predefined Values for more details. |
|
|
|
Freeform field for cost center. |
|
|
0-10080 |
Time in minutes. Denotes the maximum time within which the resource is required to recover from a failure. |
|
|
0-1440 |
Time in minutes. Maximum data loss tolerance for a data store resource such as a database or a storage device. |
Related Topics
Restarting a VM for Planned Maintenance
To facilitate maintenance of Oracle Exadata Database Service on Exascale Infrastructure virtual machines (VM), Oracle notifies you of planned VM restarts.
When Oracle schedules a restart of your VM, other VMs in that VM Cluster will not be affected by the planned maintenance. The other nodes in your cluster continue to stay available as part of your high availability (HA) strategy.
Connecting to an Oracle Exadata Database Service on Exascale Infrastructure VM
Learn how to connect to an Oracle Exadata Database Service on Exascale Infrastructure virtual machine (VM) using SSH or SQL Developer.
How you connect depends on how your cloud network is set up. You can find information on various networking scenarios in Networking Overview, but for specific recommendations on how you should connect to a database in the cloud, contact your network security administrator.
Oracle Exadata Database Service on Exascale Infrastructure servers cannot be joined to Active Directory domains, and the service does not support the use of Active Directory for user authentication and authorization.
- Prerequisites for Accessing Oracle Exadata Database Service on Exascale Infrastructure
To use SSH to access a compute node in an Oracle Exadata Database Service on Exascale Infrastructure (ExaDB-XS) instance, you need this information. - SCAN Listener Port Setting
When creating a cloud VM cluster, you can optionally designate a different SCAN listener port number. - Connecting to a Virtual Machine with SSH
You can connect to the virtual machines in an Oracle Exadata Database Service on Exascale Infrastructure system by using a Secure Shell (SSH) connection. - Using Oracle Net Services to Connect to a Database
Oracle Database Oracle Exadata Database Service on Exascale Infrastructure supports remote database access by using Oracle Net Services. - Connect to the Oracle Exadata Database Service on Exascale Infrastructure Service
Learn how to connect to an Oracle Exadata Database Service on Exascale Infrastructure system using SSH, and how to connect to an Oracle Exadata Database Service on Exascale Infrastructure database using Oracle Net Services (SQL*Net).
Prerequisites for Accessing Oracle Exadata Database Service on Exascale Infrastructure
To use SSH to access a compute node in an Oracle Exadata Database Service on Exascale Infrastructure (ExaDB-XS) instance, you need this information.
Before you can access ExaDB-XS, you must have configured Exadata Database service on Exascale Infrastructure.
-
The full path to the file that contains the private key associated with the public key used when the system was launched.
-
The public or private IP address of the Oracle Exadata Database Service on Exascale Infrastructure instance.
Use the private IP address to connect to the system from your on-premises network, or from within the virtual cloud network (VCN). This includes connecting from a host located on-premises connecting through a VPN or FastConnect to your VCN, or from another host in the same VCN. Use the public IP address to connect to the system from outside the cloud (with no VPN). You can find the IP addresses in the Oracle Cloud Infrastructure Console. On the Exadata VM Cluster Details page, click Virtual Machines in the Resources list.
The values are displayed in the Public IP Address and Private IP Address & DNS Name columns of the table displaying the Virtual Machines or Nodes of the Oracle Exadata Database Service on Exascale Infrastructure instance.
SCAN Listener Port Setting
When creating a cloud VM cluster, you can optionally designate a different SCAN listener port number.
The default SCAN listener port for cloud VM clusters is 1521. With the console, you have the option to designate a different SCAN listener port number at VM Cluster provisioning. In the OCI Console, this option appears under Advanced Options when creating the cluster.
Manually changing the SCAN listener port of a VM cluster after provisioning using the backend software is not supported. This change can cause Data Guard provisioning to fail.
Connecting to a Virtual Machine with SSH
You can connect to the virtual machines in an Oracle Exadata Database Service on Exascale Infrastructure system by using a Secure Shell (SSH) connection.
Most Unix-style systems (including Linux, Oracle Solaris, and macOS) include an SSH client. For Microsoft Windows systems, you can download a free SSH client called PuTTY from the following site: "http://www.putty.org".
- Connecting from a Unix-Style System
To access a virtual machine on an Oracle ExaDB-XS system from a Unix-style system using SSH, use this procedure. - Connecting to a Virtual Machine from a Microsoft Windows System Using PuTTY
Learn how to access a virtual machine from a Microsoft Windows system using PuTTY. - Accessing a Database After You Connect to the Virtual Machine
After you connect to a virtual machine, you can use the following series of commands to identify a database and connect to it.
Related Topics
Connecting from a Unix-Style System
To access a virtual machine on an Oracle ExaDB-XS system from a Unix-style system using SSH, use this procedure.
Parent topic: Connecting to a Virtual Machine with SSH
Connecting to a Virtual Machine from a Microsoft Windows System Using PuTTY
Learn how to access a virtual machine from a Microsoft Windows system using PuTTY.
- The IP address of the virtual machine
- The SSH private key file that matches the public key associated
with the deployment. This private key file must be in the PuTTY
.ppkformat. If the private key file was originally created on the Linux platform, you can use the PuTTYgen program to convert it to the.ppkformat.
Before you begin
To connect to a virtual machine using the PuTTY program on Windows:
Parent topic: Connecting to a Virtual Machine with SSH
Accessing a Database After You Connect to the Virtual Machine
After you connect to a virtual machine, you can use the following series of commands to identify a database and connect to it.
-
Access the VM using SSH as the
opcuser. -
Log in as the Oracle user. For example:
sudo su oracle -
Use the
srvctlutility located under the Oracle Grid Infrastructure home directory to list the databases on the system. For example:/u01/app/12.2.0.1/grid/bin/srvctl config database -v nc122 /u02/app/oracle/product/12.2.0/dbhome_6 12.2.0.1.0 s12c /u02/app/oracle/product/12.2.0/dbhome_2 12.2.0.1.0 -
Identify the database instances for the database that you want to access. For example:
/u01/app/12.2.0.1/grid/bin/srvctl status database -d s12c Instance s12c1 is running on node node01 Instance s12c2 is running on node node02 -
Configure the environment settings for the database that you want to access. For example:
. oraenv ORACLE_SID = [oracle] ? s12c The Oracle base has been set to /u02/app/oracleexport ORACLE_SID=s12c1 -
You can use the
svrctlcommand to display more detailed information about the database. For example:srvctl config database -d s12c Database unique name: s12c Database name: Oracle home: /u02/app/oracle/product/12.2.0/dbhome_2 Oracle user: oracle Spfile: +DATAC4/s12c/spfiles12c.ora Password file: +DATAC4/s12c/PASSWORD/passwd Domain: example.com Start options: open Stop options: immediate Database role: PRIMARY Management policy: AUTOMATIC Server pools: Disk Groups: DATAC4 Mount point paths: Services: Type: RAC Start concurrency: Stop concurrency: OSDBA group: dba OSOPER group: racoper Database instances: s12c1,s12c2 Configured nodes: node01,node02 CSS critical: no CPU count: 0 Memory target: 0 Maximum memory: 0 Default network number for database services: Database is administrator managed -
You can access the database by using SQL*Plus. For example:
sqlplus / as sysdba SQL*Plus: Release 12.2.0.1.0 Production ... Copyright (c) 1982, 2016, Oracle. All rights reserved. Connected to: Oracle Database 12c EE Extreme Perf Release 12.2.0.1.0 - 64bit Production
Parent topic: Connecting to a Virtual Machine with SSH
Using Oracle Net Services to Connect to a Database
Oracle Database Oracle Exadata Database Service on Exascale Infrastructure supports remote database access by using Oracle Net Services.
Because Oracle Exadata Database Service on Exascale Infrastructure uses Oracle Grid Infrastructure, you can make Oracle Net Services connections by using Single Client Access Name (SCAN) connections. SCAN is a feature that provides a consistent mechanism for clients to access the Oracle Database instances running in a cluster.
By default, the SCAN is associated with three virtual IP addresses (VIPs). Each SCAN VIP is also associated with a SCAN listener that provides a connection endpoint for Oracle Database connections using Oracle Net Services. To maximize availability, Oracle Grid Infrastructure distributes the SCAN VIPs and SCAN listeners across the available cluster nodes. In addition, if there is a node shutdown or failure, then the SCAN VIPs and SCAN listeners are automatically migrated to a surviving node. By using SCAN connections, you enhance the ability of Oracle Database clients to have a reliable set of connection endpoints that can service all of the databases running in the cluster.
The SCAN listeners are in addition to the Oracle Net Listeners that run on every node in the cluster, which are also known as the node listeners. When an Oracle Net Services connection comes through a SCAN connection, the SCAN listener routes the connection to one of the node listeners, and plays no further part in the connection. A combination of factors, including listener availability, database instance placement, and workload distribution, determines which node listener receives each connection.
This documentation provides basic requirements for connecting to your Oracle Exadata Database Service on Exascale Infrastructure databases by using Oracle Net Services.
- Prerequisites for Connecting to a Database with Oracle Net Services
Review the prerequisites to connect to an Oracle Database instance on Oracle Oracle Exadata Database Service on Exascale Infrastructure using Oracle Net Services. - Connecting to a Database with SQL Developer
You can connect to a database with SQL Developer by using one of the following methods: - Connecting to a Database Using SCAN
To create an Oracle Net Services connection by using the SCAN listeners, you can choose between two approaches. - Connecting to a Database Using a Node Listener
To connect to an Oracle Database instance on Oracle Exadata Database Service on Exascale Infrastructure with a connect descriptor that bypasses the SCAN listeners, use this procedure to route your connection directly to a node listener.
Prerequisites for Connecting to a Database with Oracle Net Services
Review the prerequisites to connect to an Oracle Database instance on Oracle Oracle Exadata Database Service on Exascale Infrastructure using Oracle Net Services.
To connect to an Oracle Database on Oracle Exadata Database Service on Exascale Infrastructure with Oracle Net Services, you need the following:
- The IP addresses for your SCAN VIPs, or the hostname or IP address for a virtual machine that hosts the database that you want to access.
- The database identifier. This can be either the database system identifier (SID), or a service name.
Parent topic: Using Oracle Net Services to Connect to a Database
Connecting to a Database with SQL Developer
You can connect to a database with SQL Developer by using one of the following methods:
- Create a temporary SSH tunnel from your computer to the database. This method provides access only for the duration of the tunnel. (When you are done using the database, be sure to close the SSH tunnel by exiting the SSH session.)
- Open the port used as the Oracle SCAN listener by updating the security list used for the cloud VM cluster resource in the Exadata Cloud Service instance. The default SCAN listener port is 1521. This method provides more durable access to the database. For more information, see Updating the Security List.
After you've created an SSH tunnel or opened the SCAN listener port as described above, you can connect to an Oracle Exadata Database Service on Exascale Infrastructure instance using SCAN IP addresses or public IP addresses, depending on how your network is set up and where you are connecting from. You can find the IP addresses in the Console, in the Database details page.
- To connect using SCAN IP addresses
You can connect to the database using the SCAN IP addresses if your client is on-premises and you are connecting using a FastConnect or Site-to-Site VPN connection. - To connect using public IP addresses
You can use the node's public IP address to connect to the database if the client and database are in different VCNs, or if the database is on a VCN that has an internet gateway.
Parent topic: Using Oracle Net Services to Connect to a Database
To connect using SCAN IP addresses
You can connect to the database using the SCAN IP addresses if your client is on-premises and you are connecting using a FastConnect or Site-to-Site VPN connection.
-
Use the private SCAN IP addresses, as shown in the following
tnsnames.oraexample:testdb= (DESCRIPTION = (ADDRESS_LIST= (ADDRESS = (PROTOCOL = TCP)(HOST = <scanIP1>)(PORT = 1521)) (ADDRESS = (PROTOCOL = TCP)(HOST = <scanIP2>)(PORT = 1521))) (CONNECT_DATA = (SERVER = DEDICATED) (SERVICE_NAME = <dbservice.subnetname.dbvcn.oraclevcn.com>) ) ) -
Define an external SCAN name in your on-premises DNS server. Your application can resolve this external SCAN name to the VM cluster's private SCAN IP addresses, and then the application can use a connection string that includes the external SCAN name. In the following
tnsnames.oraexample,extscanname.example.comis defined in the on-premises DNS server.testdb = (DESCRIPTION = (ADDRESS = (PROTOCOL = TCP)(HOST = <extscanname.example.com>)(PORT = 1521)) (CONNECT_DATA = (SERVER = DEDICATED) (SERVICE_NAME = <dbservice.subnetname.dbvcn.oraclevcn.com>) ) )
Parent topic: Connecting to a Database with SQL Developer
To connect using public IP addresses
You can use the node's public IP address to connect to the database if the client and database are in different VCNs, or if the database is on a VCN that has an internet gateway.
However, there are important implications to consider:
- When the client uses the public IP address, the client bypasses the SCAN listener and reaches the node listener, so server side load balancing is not available.
- When the client uses the public IP address, it cannot take advantage of the VIP failover feature. If a node becomes unavailable, new connection attempts to the node will hang until a TCP/IP timeout occurs. You can set client side sqlnet parameters to limit the TCP/IP timeout.
The following tnsnames.ora example shows a connection string that
includes the CONNECT_TIMEOUT parameter to avoid TCP/IP timeouts.
test=
(DESCRIPTION =
(CONNECT_TIMEOUT=60)
(ADDRESS_LIST=
(ADDRESS = (PROTOCOL = TCP)(HOST = <publicIP1>)(PORT = 1521))
(ADDRESS = (PROTOCOL = TCP)(HOST = <publicIP2>)(PORT = 1521))
)
(CONNECT_DATA =
(SERVER = DEDICATED)
(SERVICE_NAME = <dbservice.subnetname.dbvcn.oraclevcn.com>)
)
)Parent topic: Connecting to a Database with SQL Developer
Connecting to a Database Using SCAN
To create an Oracle Net Services connection by using the SCAN listeners, you can choose between two approaches.
- Connecting to a Database Using a Connect Descriptor that References All of the SCAN VIPs
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using multiple SCAN listeners. - Connecting to a Database Use a Connect Descriptor that References a Custom SCAN Name
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using a custom SCAN name.
Parent topic: Using Oracle Net Services to Connect to a Database
Connecting to a Database Using a Connect Descriptor that References All of the SCAN VIPs
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using multiple SCAN listeners.
This approach requires you to supply all of the single client access name (SCAN) virtual IP (VIP) addresses, and enables Oracle Net Services to connect to an available SCAN listener.
Parent topic: Connecting to a Database Using SCAN
Connecting to a Database Use a Connect Descriptor that References a Custom SCAN Name
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using a custom SCAN name.
Using this approach, you define a custom single client access name (SCAN) name in your domain name server (DNS), which resolves to the three SCAN virtual IP addresses (VIPs).
Parent topic: Connecting to a Database Using SCAN
Connecting to a Database Using a Node Listener
To connect to an Oracle Database instance on Oracle Exadata Database Service on Exascale Infrastructure with a connect descriptor that bypasses the SCAN listeners, use this procedure to route your connection directly to a node listener.
By using this method, you give up the high-availability and load-balancing provided by SCAN. However, this method may be desirable if you want to direct connections to a specific node or network interface. For example, you might want to ensure that connections from a program that performs bulk data loading use the backup network.
Using this approach, you direct your connection using the hostname or IP address of the node.
Example 4-1 Defining a Net Service Alias That Directly References the Node
alias-name = (DESCRIPTION=
(CONNECT_TIMEOUT=timeout)
(ADDRESS_LIST=(ADDRESS=(PROTOCOL=tcp)(HOST=node)(PORT=1521)))
(CONNECT_DATA=(sid-or-service-entry)))Where:
alias-name
is the name you use to identify the alias.
timeout
specifies a timeout period (in seconds), which enables you to
terminate a connection attempt without having to wait for a TCP
timeout. The (CONNECT_TIMEOUT=timeout) parameter is
optional.
node is the
hostname or IP address for the virtual machine that you want to
use.
sid-or-service-entry identifies the
database SID or service name using one of the following formats:
SID=sid-name. For example,SID=S12C1.SERVICE_NAME=service-name. For example,SERVICE_NAME=PDB1.example.oraclecloudatcust.com.
node:1521/sid-or-service-entryexa1node01.example.com:1521/S12C1exa1node01.example.com:1521/PDB1.example.oraclecloudatcust.comParent topic: Using Oracle Net Services to Connect to a Database
Connect to the Oracle Exadata Database Service on Exascale Infrastructure Service
Learn how to connect to an Oracle Exadata Database Service on Exascale Infrastructure system using SSH, and how to connect to an Oracle Exadata Database Service on Exascale Infrastructure database using Oracle Net Services (SQL*Net).
- Connecting to a Database with SQL Developer
You can connect to a database with SQL Developer by using one of the following methods: - Connecting to a Database with Oracle Net Services
You can connect to the virtual machines in an Oracle Exadata Database Service on Exascale Infrastructure system using Oracle Net Services.
Connecting to a Database with SQL Developer
You can connect to a database with SQL Developer by using one of the following methods:
- Create a temporary SSH tunnel from your computer to the database. This method provides access only for the duration of the tunnel. (When you are done using the database, be sure to close the SSH tunnel by exiting the SSH session.)
- Open the port used as the Oracle SCAN listener by updating the security list used for the cloud VM cluster resource in the Exadata Cloud Service instance. The default SCAN listener port is 1521. This method provides more durable access to the database. For more information, see Updating the Security List.
After you've created an SSH tunnel or opened the SCAN listener port as described above, you can connect to an Oracle Exadata Database Service on Exascale Infrastructure instance using SCAN IP addresses or public IP addresses, depending on how your network is set up and where you are connecting from. You can find the IP addresses in the Console, in the Database details page.
Connecting to a Database with Oracle Net Services
You can connect to the virtual machines in an Oracle Exadata Database Service on Exascale Infrastructure system using Oracle Net Services.
- Using Oracle Net Services to Connect to a Database
Oracle Database Oracle Exadata Database Service on Exascale Infrastructure supports remote database access by using Oracle Net Services. - Prerequisites for Connecting to a Database with Oracle Net Services
Review the prerequisites to connect to an Oracle Database instance on Oracle Oracle Exadata Database Service on Exascale Infrastructure using Oracle Net Services. - Connecting to a Database Using SCAN
To create an Oracle Net Services connection by using the SCAN listeners, you can choose between two approaches. - Connecting to a Database Using a Node Listener
To connect to an Oracle Database instance on Oracle Exadata Database Service on Exascale Infrastructure with a connect descriptor that bypasses the SCAN listeners, use this procedure to route your connection directly to a node listener.
Using Oracle Net Services to Connect to a Database
Oracle Database Oracle Exadata Database Service on Exascale Infrastructure supports remote database access by using Oracle Net Services.
Because Oracle Exadata Database Service on Exascale Infrastructure uses Oracle Grid Infrastructure, you can make Oracle Net Services connections by using Single Client Access Name (SCAN) connections. SCAN is a feature that provides a consistent mechanism for clients to access the Oracle Database instances running in a cluster.
By default, the SCAN is associated with three virtual IP addresses (VIPs). Each SCAN VIP is also associated with a SCAN listener that provides a connection endpoint for Oracle Database connections using Oracle Net Services. To maximize availability, Oracle Grid Infrastructure distributes the SCAN VIPs and SCAN listeners across the available cluster nodes. In addition, if there is a node shutdown or failure, then the SCAN VIPs and SCAN listeners are automatically migrated to a surviving node. By using SCAN connections, you enhance the ability of Oracle Database clients to have a reliable set of connection endpoints that can service all of the databases running in the cluster.
The SCAN listeners are in addition to the Oracle Net Listeners that run on every node in the cluster, which are also known as the node listeners. When an Oracle Net Services connection comes through a SCAN connection, the SCAN listener routes the connection to one of the node listeners, and plays no further part in the connection. A combination of factors, including listener availability, database instance placement, and workload distribution, determines which node listener receives each connection.
This documentation provides basic requirements for connecting to your Oracle Exadata Database Service on Exascale Infrastructure databases by using Oracle Net Services.
Parent topic: Connecting to a Database with Oracle Net Services
Prerequisites for Connecting to a Database with Oracle Net Services
Review the prerequisites to connect to an Oracle Database instance on Oracle Oracle Exadata Database Service on Exascale Infrastructure using Oracle Net Services.
To connect to an Oracle Database on Oracle Exadata Database Service on Exascale Infrastructure with Oracle Net Services, you need the following:
- The IP addresses for your SCAN VIPs, or the hostname or IP address for a virtual machine that hosts the database that you want to access.
- The database identifier. This can be either the database system identifier (SID), or a service name.
Parent topic: Connecting to a Database with Oracle Net Services
Connecting to a Database Using SCAN
To create an Oracle Net Services connection by using the SCAN listeners, you can choose between two approaches.
- Identifying IP Addresses Using the SDK or CLI
You can use the SDK or the OCI CLI to identify the IP addresses of Oracle Exadata Database Service on Exascale Infrastructure compute nodes. You can then use the IP addresses to connect to your system. - Connecting to a Database Using a Connect Descriptor that References All of the SCAN VIPs
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using multiple SCAN listeners. - Connecting to a Database Use a Connect Descriptor that References a Custom SCAN Name
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using a custom SCAN name.
Parent topic: Connecting to a Database with Oracle Net Services
Identifying IP Addresses Using the SDK or CLI
You can use the SDK or the OCI CLI to identify the IP addresses of Oracle Exadata Database Service on Exascale Infrastructure compute nodes. You can then use the IP addresses to connect to your system.
- Use the
GetDbNodeAPI to return the details of the Oracle Exadata Database Service on Exascale InfrastructuredbNode. Note the OCIDs returned for thehostIpIdandbackupIpIdparameters of the dbNode. - With the OCIDs found in the
hostIpIdandbackupIpIdparameters, you can use the GetPrivateIp API to get the private IP addresses used by the client and backup subnets. For public subnet IP addresses, use the GetPublicIpByPrivateIpId API.
Parent topic: Connecting to a Database Using SCAN
Connecting to a Database Using a Connect Descriptor that References All of the SCAN VIPs
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using multiple SCAN listeners.
This approach requires you to supply all of the single client access name (SCAN) virtual IP (VIP) addresses, and enables Oracle Net Services to connect to an available SCAN listener.
Parent topic: Connecting to a Database Using SCAN
Connecting to a Database Use a Connect Descriptor that References a Custom SCAN Name
You can set up a connect descriptor for Oracle Exadata Database Service on Exascale Infrastructure System using a custom SCAN name.
Using this approach, you define a custom single client access name (SCAN) name in your domain name server (DNS), which resolves to the three SCAN virtual IP addresses (VIPs).
Parent topic: Connecting to a Database Using SCAN
Connecting to a Database Using a Node Listener
To connect to an Oracle Database instance on Oracle Exadata Database Service on Exascale Infrastructure with a connect descriptor that bypasses the SCAN listeners, use this procedure to route your connection directly to a node listener.
By using this method, you give up the high-availability and load-balancing provided by SCAN. However, this method may be desirable if you want to direct connections to a specific node or network interface. For example, you might want to ensure that connections from a program that performs bulk data loading use the backup network.
Using this approach, you direct your connection using the hostname or IP address of the node.
Example 4-2 Defining a Net Service Alias That Directly References the Node
alias-name = (DESCRIPTION=
(CONNECT_TIMEOUT=timeout)
(ADDRESS_LIST=(ADDRESS=(PROTOCOL=tcp)(HOST=node)(PORT=1521)))
(CONNECT_DATA=(sid-or-service-entry)))Where:
alias-name
is the name you use to identify the alias.
timeout
specifies a timeout period (in seconds), which enables you to
terminate a connection attempt without having to wait for a TCP
timeout. The (CONNECT_TIMEOUT=timeout) parameter is
optional.
node is the
hostname or IP address for the virtual machine that you want to
use.
sid-or-service-entry identifies the
database SID or service name using one of the following formats:
SID=sid-name. For example,SID=S12C1.SERVICE_NAME=service-name. For example,SERVICE_NAME=PDB1.example.oraclecloudatcust.com.
node:1521/sid-or-service-entryexa1node01.example.com:1521/S12C1exa1node01.example.com:1521/PDB1.example.oraclecloudatcust.comParent topic: Connecting to a Database with Oracle Net Services
Capacity Limits for Exadata Database Service on Exascale Infrastructure
To understand the scalability features and resource capacity of the ExaDB-XS service, review these tables and lists.
Minimum VM Cluster Size
- Single-node VM cluster
- 8 total ECPUs per VM
- 220 GB (for 26ai) and 260 GB (for 19c) file system storage per VM
- 300 GB Exascale Vault database storage per VM cluster
VM Scalability Options
VM clusters can be scaled quickly and easily to meet your demands:
- It is possible to enable a subset of the total ECPUs assigned to the VM.
- When you enable more of your reserved ECPUs for the VM, you can scale the ECPUs without restarting the VM.
- You can scale memory in 2.75 GB increments per total ECPU.
- You can perform hot additions or removals of VMs
- You can scale VM storage (however, scaling VM storage requires a restart).
- You can perform live, online scaling of Exascale database storage
Maximum VM Cluster Size
The following list provides maximum VM cluster configuration options
- Number of VMs in the VM Cluster: 10 VMs.
- ECPUs per VM: 200 ECPUs
- File system storage per VM: 2 TB
- Exascale Vault storage per VM cluster: 100 TB
Database Storage Vault Minimum Capacity
The total minimum capacity billed for ExaDB-XS vaults is 300 GB. Images are stored in Oracle Advanced Cluster File System (ACFS). The remaining space is available for the first database, as shown in the following table:
Table 4-2 ExaDB-XS Minimum Database Storage Vault Capacity for Systems and Database Use
| Purpose | Minimum Capacity |
|---|---|
| System use (images stored in ACFS) | 50 GB |
| Database use (provisioning a first database) | 250 GB |
VM File System Storage Minimum Capacity
The total minimum capacity billed for virtual machine (VM) storage is 220 GB (for 26ai) and 260 GB (for 19c). File system minimum capacities are listed in the following table.
Table 4-3 ExaDB-XS VM File System Storage Minimum Billed Capacity
| File System | Minimum Total Capacity (GB) for 26ai ExaDB-XS VM Cluster | Minimum Total Capacity (GB) for 19c ExaDB-XS VM Cluster |
|---|---|---|
|
|
15 |
15 |
|
|
15 |
15 |
|
|
4 |
4 |
|
|
5 | 5 |
|
|
5 |
5 |
|
|
18 |
18 |
|
|
3 |
3 |
|
|
10 |
10 |
|
|
62 |
62 |
|
|
42 |
82 |
|
Internal file systems |
41 |
41 |
|
Total File system size per VM (GB) |
220 |
260 |
Best Practices for Oracle Exadata Database Service on Exascale Infrastructure VMs
Oracle recommends that you follow these best practice guidelines to ensure the manageability of your Oracle Exadata Database Service on Exascale Infrastructure virtual machines (VMs).
When followed, best practice guidelines can prevent problems that can affect the manageability and performance of yourOracle Exadata Database Service on Exascale Infrastructure VMs:
- Wherever possible, use the Oracle-supplied cloud interfaces such as the Oracle
Cloud Infrastructure Console, API, or CLI, or cloud-specific tools
such as
dbaasclito perform lifecycle management and administrative operations on your Oracle Exadata Database Service on Exascale Infrastructure VM. For example, use the OCI console, API, CLI, ordbaasclito apply Oracle Database patches instead of manually runningopatch. In addition, if an operation can be performed by using the Console as well as a command-line utility, Oracle recommends that you use the Console. For example, use the Console instead of usingdbaasclito create databases. - Do not change the Guest OS users or manually manipulate SSH key settings.
- Apply only patches that are available through the Database service. Do not apply patches from any other source unless you are directed to do so by Oracle Support.
- Apply the quarterly patches regularly, every quarter if possible.
- Do not change the ports for Oracle Net Listener.