Create a Virtual Cloud Network
Use Terraform to create a virtual cloud network (VCN) in your Oracle Cloud Infrastructure tenancy.
Key tasks include how to:
- Set up a basic VCN.
- Define and add the following resources to the network:
- Security lists
- Private and public subnets
For more information, see:
Before You Begin
To successfully perform this tutorial, you must have the following:
- A paid Oracle Cloud Infrastructure account. See Request and Manage Free Oracle Cloud Promotions.
- A MacOS, Linux, or Windows computer.
- Terraform tutorial resources:
- Go through all the steps in:
- Keep the scripts you created in the following directories:
-
$HOME/tf-provider/ -
$HOME/tf-compartment/
-
- Keep the compartment from the Create a Compartment tutorial in your tenancy.
1. Prepare
Prepare your environment for creating a VCN. Also, collect all the information you need to complete the tutorial.
Copy the following information into your notepad.
For steps to collect this information, see the following table.
| Item | Steps to collect item |
|---|---|
| Compartment name | Reference the completed tutorial Create a Compartment. |
| Compartment ID |
|
| Region |
|
If your username is in the Administrators group, then skip this section. Otherwise, ask your administrator to add the following policy to your tenancy:
allow group <a-group-your-username-belongs-to> to manage all-resources in compartment <your-compartment-name>
With this privilege, you can manage all resources in your compartment, giving you administrative rights in that compartment.
- In the Console: Open the navigation menu and select Identity & Security. Under Identity, select Policies.
- Select your compartment.
- Select Create Policy.
- On the Create Policy page, enter the following values:
-
Name:
manage-<your-compartment-name>-resources -
Description:
Allow users to list, create, update, and delete resources in <your-compartment-name>. -
Compartment:
<your-tenancy>(root)
-
Name:
- For Policy Builder, enter the following values:
-
Policy use cases:
Compartment Management -
Common policy templates:
Let compartment admins manage the compartment - Identity domain: <identity-domain>
-
Groups:
<a-group-your-username-belongs-to> -
Location:
<your-compartment-name>
-
Policy use cases:
- Select Create.
Reference: Common Policies
2. Create a Basic Network
Create scripts for authentication, a basic virtual cloud network (VCN) defined by a module, and outputs.
First, set up a directory for your Terraform scripts. Then copy the provider and versions scripts from the Set Up OCI Terraform tutorial so your Oracle Cloud Infrastructure account can authenticate the scripts running from this directory.
Declare a basic network with an Oracle Cloud Infrastructure virtual cloud network (VCN) module, documented in the Terraform Registry. Then, run your scripts and create the network. In the next sections, add components to customize your network.
You can save a stack from the Console workflow for creating a VCN. The stack contains a Terraform configuration that you can use as a reference for the VCN configuration. See Creating a Stack from a Resource Creation Page and Getting a Stack's Terraform Configuration.
About Modules
A module is a container for multiple resources that are used together. Instead of declaring infrastructure resources one by one, start with a module provided by Oracle Cloud Infrastructure. For example, start with a basic VCN module. Then, add the resources that aren't included in the module to your scripts.
Declare a Module Block
- Start the block with the keyword:
module - Add a label for the module's provided name:
- Example:
"vcn"
- Example:
- Inside the code block:
- Add
sourceandversioninformation from the Provision Instructions section of the module documentation. - Provide a value for the required inputs. They don't have a default value. Example:
# Required Inputs compartment_id = "<compartment-ocid>" - Provide values for the optional inputs that you want to override. Otherwise, their default values are used. Example:
# Optional Inputs region = "<region-identifier>" # Changing the following default values vcn_name = "tutorial-vcn" create_internet_gateway = true create_nat_gateway = true create_service_gateway = true - You can comment out the optional inputs and show their default value, so later when you review your code, you know what values were expected. Example:
# Using the following default values # vcn_dns_label = "vcnmodule" # vcn_cidrs = ["10.0.0.0/16"]
- Add
Add output blocks to your code to get information about your virtual cloud network after you run your scripts.
About Module Outputs
Module outputs are the attributes that you can return for that module.
Find Outputs for VCN Module
Go to the vcn page and select Outputs to view a list of attributes that can be output for the VCN module. Review the description of the attributes:
-
ig_route_id
- OCID of the route table that includes the internet gateway
-
nat_gateway_id
- OCID of the NAT gateway
-
nat_route_id
- OCID of the route table that includes the NAT gateway
-
vcn_id
- OCID of the VCN
Declare a Module Output Block
-
- Start the block with the keyword:
output. - Add a label to be printed with the output results:
-
The label can contain letters, digits, underscores (
_), and hyphens (-). The first character must not be a digit. - Example:
"vcn_id"
-
The label can contain letters, digits, underscores (
- Get the attributes from the outputs for the module at Oracle Terraform Modules.
- Inside the code block, enter a value for the module output with the expression:
-
value = module.<module-name>.<output-attribute> - Example:
value = module.vcn.vcn_id
-
- (Optional): Inside the code block, add a description string. Example:
description = "OCID of the internet-route table. This route table has an internet gateway to be used for public subnets"Note
A description string isn't printed in the output, so ensure that the label describes what it outputs. - Create an output block for each output.
- Start the block with the keyword:
Congratulations! You have successfully created a basic virtual network using Terraform, in your Oracle Cloud Infrastructure account. You have a virtual network and you can be done at this point. The next sections show you how to customize a network created from a module.
3. Customize the Network
Create scripts for security lists, private subnets, and public subnets to create the same virtual network as in the Console creation workflow.
At Argument Reference (oci_core_security_list), find all required arguments (first-level bullets):
- compartment_id
- vcn_id
To navigate to Argument Reference (oci_core_security_list):
- Go to Oracle Cloud Infrastructure Provider.
-
In the Filter box on the upper left, enter
security list.Results are returned for both data sources and resources.
- Under Core, go to Resources and select oci_core_security_list.
- Select Argument Reference.
Argument Reference opens.
Declare the security list:
- For compartment_id:
use
compartment_id = "<compartment-ocid>" - For vcn_id, use the OCID of the basic virtual network. To assign the OCID before knowing it, assign an output from the module as input for the security list resource:
- Get the module's output attribute from the module's Outputs page.
- Assign a value to the resource argument with the expression:
-
<resource argument> = module.<module-name>.<output-attribute> - Example:
vcn_id = module.vcn.vcn_id - Both
oci_core_security_list resourceandoracle-terraform-modules/vcnuse the same argument name for the virtual cloud network OCID:vcn_id. - The leftmost
vcn_idis the argument (required input) for the resource. - The rightmost
vcn_idis the OCID of the VCN that you create with the module. - It doesn't matter if you have run the VCN module script and created the VCN or not. Either way, Terraform assigns the VCN OCID to the security list after the VCN module is created.
-
- Stateless: No
- Destination: 0.0.0.0/0
- IP Protocol: All Protocols
The Allows field in the table is automatically generated based on other fields. You don't add an argument for it in your script.
For private-security-list.tf, go to Argument Reference (oci_core_security_list) and find the following arguments:
-
egress_security_rules
- stateless
- destination
- destination_type
- protocol
To navigate to Argument Reference (oci_core_security_list):
- Go to Oracle Cloud Infrastructure Provider.
-
In the Filter box on the upper left, enter
security list.Results are returned for both data sources and resources.
- Under Core, go to Resources and select oci_core_security_list.
- Select Argument Reference.
Argument Reference opens.
Use the equals sign (=) to assign a value to an argument inside the block only.
-
Write:
egress_security_rules { <arguments with assigned values> } -
Don't write:
egress_security_rules = { <arguments with assigned values> }
For attributes for use as outputs in outputs.tf, select Attribute Reference to open Attributes Reference (oci_core_security_list) and find the following attributes:
- display_name
- id
Congratulations! You have successfully created a security list with an egress rule in your virtual cloud network. In the next section, you add ingress rules to this security list.
In this section, you add the following ingress rules to the security list you created in the previous section.
Ingress Rules
- Rule 1:
- Stateless: No
- Source: 10.0.0.0/16
- IP Protocol: TCP
- Source Port Range: All
- Destination Port Range: 22
- Rule 2:
- Stateless: No
- Source: 0.0.0.0/0
- IP Protocol: ICMP
- Type and Code: 3, 4
- Rule 3:
- Stateless: No
- Source: 10.0.0.0/16
- IP Protocol: ICMP
- Type and Code: 3
The Allows field in the table is automatically generated based on other fields. You don't add an argument for it in your script.
Congratulations! You have successfully added three ingress rules to your security list. You use this security list for a private subnet. You create another security list for a public subnet in the next section.
At Argument Reference (oci_core_security_list), find the following arguments:
-
ingress_security_rules
- stateless
- source
- source_type
- protocol
-
icmp_options
- type
- code
-
tcp_options
- min
- max
To navigate to Argument Reference (oci_core_security_list):
- Go to Oracle Cloud Infrastructure Provider.
-
In the Filter box on the upper left, enter
security list.Results are returned for both data sources and resources.
- Under Core, go to Resources and select oci_core_security_list.
- Select Argument Reference.
Argument Reference opens.
- For protocol, see Protocol Numbers:
- TCP: 6
- ICMP: 1
- For icmp_options, see Internet Control Message Protocol (ICMP) Parameters.
- For tcp_options, if you have no port range, such as Destination Range: 22, set the maximum and minimum value to the same number. Example:
- min = 22
- max = 22
Congratulations! You have successfully created another security list in your virtual cloud network.
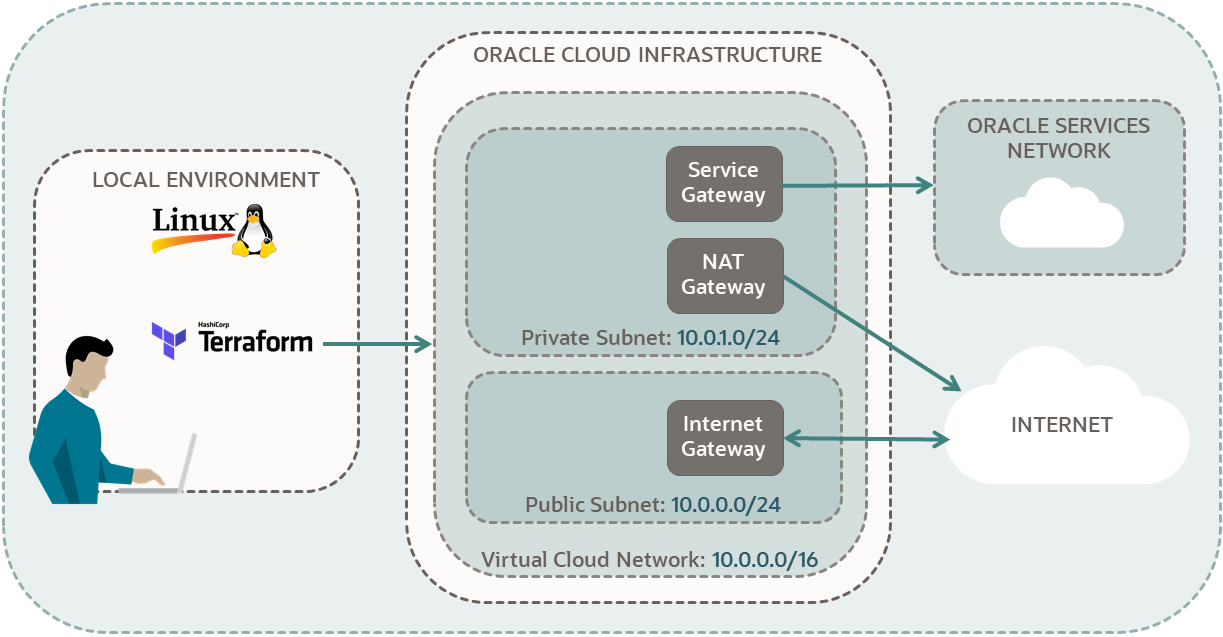
In this section, you create a private subnet in your network and associate the private security list to this subnet. You also add the NAT route table that you made with the VCN module to this subnet. The NAT route table has one NAT gateway and one service gateway and is designed for private subnets. See the first diagram in the tutorial.
Congratulations! You have successfully created a private subnet in your virtual cloud network.
At Argument Reference (oci_core_subnet), find all required arguments:
- compartment_id
- vcn_id
- cidr_block
To navigate to Argument Reference (oci_core_subnet):
- Go to Oracle Cloud Infrastructure Provider.
-
In the Filter box on the upper left, enter
subnet.Results are returned for both data sources and resources.
- Under Core, go to Resources and select oci_core_subnet.
- Select Argument Reference.
Argument Reference opens.
- Override the following optional arguments:
- route_table_id
- security_list_ids
- display_name
- Assign values to the following arguments:
-
cidr_block
- See the first diagram in the tutorial.
-
route_table_id
- The OCID of a route table.
- To see the gateways for this route table, reference the private subnet in the first diagram in the tutorial:
- NAT Gateway
- Service Gateway
- Assign the route table with the NAT gateway that you created with the VCN module. This route table also contains a service gateway.Note
- Use
module.vcn.nat_route_id. -
Don't use
module.vcn.nat_gateway_id, because it returns the OCID of the gateway and not the route table.
- Use
- (Optional): In the Console, review the rules of the route table and compare the Target Type values with the tutorial diagram (Service Gateway, NAT Gateway).
- On the details page for your VCN, select Routing or Route Tables (depending on what you see).
- Select nat-route.
- Select Route Rules.
-
security_list_ids
- Returns a list of strings, each an OCID of a security list.
- Get the OCID of the private security list.
- Use square brackets for this argument. Example:
security_list_ids = ["sec-list-1","sec-list-2","sec-list-3"] - To assign one security list, place it inside the square brackets without any commas.
- To reference the security list created with another resource, use its local name. Example:
security_list_ids = [oci_core_security_list.<local-name>.id] security_list_ids = [oci_core_security_list.private-security-list.id]
-
cidr_block
In this section, you create a public subnet in your network and associate the public security list to this subnet. You also add the internet route table that you made with the VCN module to this subnet. The internet route table has an internet gateway and is designed for public subnets. See the first diagram in the tutorial.
Congratulations! You have successfully created a public subnet in your virtual cloud network.
At Argument Reference (oci_core_subnet), find all required arguments:
- compartment_id
- vcn_id
- cidr_block
To navigate to Argument Reference (oci_core_subnet):
- Go to Oracle Cloud Infrastructure Provider.
-
In the Filter box on the upper left, enter
subnet.Results are returned for both data sources and resources.
- Under Core, go to Resources and select oci_core_subnet.
- Select Argument Reference.
Argument Reference opens.
- Override the following optional arguments:
- route_table_id
- security_list_ids
- display_name
- Assign values to the following arguments:
-
cidr_block
- See the first diagram in the tutorial.
-
route_table_id
- The OCID of a route table.
- To see the gateway for this route table, reference the public subnet in the first diagram in the tutorial:
- Internet Gateway
- Assign the route table with an internet gateway that you created with the VCN module.Note
- Use module.vcn.ig_route_id.
- (Optional): In the Console, review the rules of the route table and compare the Target Type value with the tutorial diagram (Internet Gateway).
- On the details page for your VCN, select Routing or Route Tables (depending on what you see).
- Select internet-route.
- Select Route Rules.
-
security_list_ids
- Returns a list of strings, each an OCID of a security list.
- Get the OCID of the public security list.
- Use square brackets for this argument. Example:
security_list_ids = ["sec-list-1","sec-list-2","sec-list-3"] - To assign one security list, place it inside the square brackets without any commas.
- To reference the security list created with another resource, use its local name. Example:
security_list_ids = [oci_core_security_list.<local-name>.id] security_list_ids = [oci_core_security_list.public-security-list.id]
-
cidr_block
4. Re-create the VCN (Optional)
Destroy your VCN. Then rerun your scripts to create another VCN.
In the previous sections, to check your work, you ran your scripts every time you declared a resource. Now, you run them together. You observe that the scripts are declarative and Terraform resolves the order in which it creates the objects.
Congratulations! You have successfully re-created a virtual cloud network and its components using Terraform, in your Oracle Cloud Infrastructure account.
This virtual cloud network has the same components as a virtual cloud network that's created using Start VCN Wizard in the Console, with the VCN with Internet Connectivity option. You can follow the tutorial steps to set up a network and then compare it with this network.
References:
What's Next
For the next Terraform tutorial, go to:
To explore more information about development with Oracle products, check out these sites: