Resource Discovery and Promotion
To monitor resources using Stack Monitoring, they must first be discovered or promoted. Promotion pre-populates information related to the resource. Be sure to validate this information and make sure that it is correct. The prerequisites and input parameters for promotion are the same as those for user-initiated discovery.
See Resource Prerequisites for direct access to prerequisites for a specific resource type.
The following table lists resource types and corresponding links to discovery/promotion instructions.
For detailed information about supported resource types and environments, see MOS Note: 2925632.1.
| Resource Type | Discovery/Promotion |
|---|---|
| E-Business Suite | E-Business Suite |
Host (Linux, Solaris, Windows)
|
|
|
Oracle Database Including:
|
Oracle Database |
| Pluggable Database | Pluggable Database |
| PeopleSoft | PeopleSoft |
| Tomcat | Apache Tomcat |
| Microsoft SQL Server | Microsoft SQL Server |
| WebLogic Server | Oracle WebLogic Domain |
| Oracle Service-Oriented Architecture (SOA) | Oracle WebLogic Domain SOA is automatically discovered as part of the WebLogic Domain discovery. Note
If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover SOA. Both SOA and WebLogic must be monitored by the same agent. For SOA discovery, the WebLogic user needs to have Administrator privileges. |
| Oracle HTTP Server (OHS) | Oracle HTTP Server (OHS)
Collocated OHS is automatically discovered as part of the Oracle WebLogic Domain discovery, and must be installed in an existing Oracle home, collocated with a WebLogic Server domain. Note
If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover OHS. Both OHS and WebLogic must be monitored by the same agent. |
| Oracle Identity Manager (OIM) | Oracle WebLogic Domain OIM is automatically discovered as part of the WebLogic Domain discovery. Note
If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover OIM. Both OIM and WebLogic must be monitored by the same agent. |
| Oracle Access Manager (OAM) | Oracle WebLogic Domain OAM is automatically discovered as part of the WebLogic Domain discovery. Note
If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover OAM. Both OAM and WebLogic must be monitored by the same agent. |
| Oracle Service Bus (OSB) | Oracle WebLogic Domain OSB is automatically discovered as part of the WebLogic Domain discovery. Note
If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover OSB. Both OSB and WebLogic must be monitored by the same agent. |
| Oracle Weblogic Node Manager | Oracle WebLogic Domain Oracle Weblogic Node Manager is automatically discovered as part of the WebLogic Domain discovery. Note
If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover Oracle Weblogic Node Manager. Both Oracle Weblogic Node Manager and WebLogic must be monitored by the same agent. |
| Oracle Managed File Transfer (Oracle MFT) | Managed File Transfer (MFT) |
| Apache HTTP Server | Apache HTTP Server |
| Oracle Unified Directory | Oracle Unified Directory |
| GoldenGate | Oracle GoldenGate |
| Oracle JVM Runtime | Oracle JVM Runtime |
| NGINX | NGINX |
Resource Prerequisites
Before you add resources to monitoring in Stack Monitoring, you'll need to make sure any prerequisites are met. Prerequisites differ according to resource type.
The following table lists resource types supported by Stack Monitoring along with direct links to sections detailing any prerequisites for adding that resource type to Stack Monitoring.
| Resource Type | Prerequisites |
|---|---|
| E-Business Suite | Prerequisites for discovering E-Business Suite |
| Host (Linux, Solaris, Windows) | |
| Oracle Database / Pluggable Database | Oracle Database Prerequisites |
| PeopleSoft | PeopleSoft |
| Tomcat | Prerequisites for discovering Tomcat |
| Microsoft SQL Server | Prerequisites for discovering Microsoft SQL Server |
| WebLogic Server | Prerequisites for discovering or promoting WebLogic Server |
| Managed File Transfer (MFT) | Prerequisites for discovering or promoting Managed File Transfer (MFT) |
| Oracle HTTP Server (OHS) | Prerequisites for discovering or promoting Oracle HTTP Server (OHS) |
| Apache HTTP Server | Prerequisites for discovering or promoting Apache HTTP Server |
| Oracle Unified Directory | Prerequisites for discovering or promoting Oracle Unified Directory |
| GoldenGate | Prerequisites for discovering or promoting GoldenGate |
| Microsoft IIS | Prerequisites for discovering Microsoft IIS |
Monitoring Host Servers
Prerequisites
OCI Compute Instances
Promoting OCI compute instances enables richer monitoring of the compute instance and visibility into resources that are running on the compute instance. After promotion, the resource type of the compute instance is a host.
-
Promoting OCI compute instances enables richer monitoring of the compute instance and visibility into resources that are running on the compute instance. After promotion, the resource type of the compute instance is a host. For more information, see Deploy Management Agents on Compute Instances.
On-premises hosts
Discovery of an on-premises host enables monitoring and provides visibility into resources that are running on the host.
Hosts running within another cloud provider are monitored using the same process as an on-premises host.
- The on-premises Management Agent monitoring the host must be deployed locally on the host and the necessary prerequisites completed. For more information see Perform Prerequisites for Deploying Management Agents.
-
To prevent the need for updating host-name post-discovery, it's advised to make sure the host name, as detected on the host itself, to be a fully qualified domain name. The value of the host name is pulled from local DNS.
Example:
For Linux, the value of the host name is pulled from DNS and can be overridden using
/etc/hosts. To check the host name use the following command on the host's command line:hostname -f
GPU hosts
GPU monitoring is only supported on linux.
- Create the following additional viewer and admin policies for GPU running on OCI compute.
Create Policies for View Operations
The following is the policy to add for the users that can only view the resources. The users that belong to the
StackMonitoringViewerGrpgroup.Policy Description ALLOW GROUP StackMonitoringViewerGrp TO {COMPUTE_CAPACITY_TOPOLOGY_READ,COMPUTE_BARE_METAL_HOST_INSPECT, COMPUTE_BARE_METAL_HOST_READ,COMPUTE_HPC_ISLAND_READ,COMPUTE_NETWORK_BLOCK_READ,COMPUTE_LOCAL_BLOCK_READ} IN COMPARTMENT <compartment_name>Allow the users in the StackMonitoringViewerGrp group to view the status of the GPU compute Create Policies for Administrative Operations
The following is the policy for users that can perform administration operations. The users that belong to the
StackMonitoringAdminGrpgroup.Policy Description ALLOW GROUP StackMonitoringAdminGrp TO {COMPUTE_CAPACITY_TOPOLOGY_INSPECT,COMPUTE_CAPACITY_TOPOLOGY_READ,COMPUTE_BARE_METAL_HOST_INSPECT, COMPUTE_BARE_METAL_HOST_READ,COMPUTE_HPC_ISLAND_READ,COMPUTE_NETWORK_BLOCK_READ,COMPUTE_LOCAL_BLOCK_READ} IN COMPARTMENT <compartment_name>Allow the users in the StackMonitoringAdminGrpgroup to retrieve the topology and details of the GPU compute - Enable Management Agent within the Oracle Cloud Agent. For more information, see Step 3: Install Management Agents
- Make the nvidia-smi tool available to the
mgmt_agentuser by installing the NVIDIA proprietary drivers on the host, if not already pre-installed. For more information, see NVIDIA drivers instalation. - Optional, for RDMA data to be displayed in the host homepage, enable monitoring for compute instance metrics. For more information, see Enabling Monitoring for Compute Instances.
Upon completion of all steps and prerequisites, the discovery of a host resource will also include each GPU installed in the host. Additionally, each GPU resource will be created, and the host resource will have a CONTAINS relation with each GPU resource.
Promotion
Host monitoring is enabled through a promotion job and configured to be performed either automatically or manually within a compartment.
Automatic Promotion
GPU hosts cannot be discovered as part of host auto-promotion.
Once a Management Agent registers, in a compartment for which automatic promotion has been enabled, the host where the agent is locally installed will be automatically promoted to full monitoring.
Once an OCI Compute instance is created, in a compartment for which automatic promotion has been enabled, the management agent plugin inside oracle cloud agent on that instance will be activated and the agent will be automatically promoted to full monitoring.
Prerequisites:
The following policies are required to allow automatic promotion of Management Agents and OCI Compute Instances to full host monitoring:
| Policy | Description |
|---|---|
ALLOW SERVICE appmgmt TO {STACK_MONITORING_DISCOVERY_JOB_CREATE,STACK_MONITORING_WORK_REQUEST_READ,STACK_MONITORING_CONFIG_INSPECT} IN COMPARTMENT <compartment_name> |
Allow Stack Monitoring to promote agents/hosts in compartment |
ALLOW SERVICE appmgmt TO {MGMT_AGENT_DEPLOY_PLUGIN_CREATE, MGMT_AGENT_INSPECT, MGMT_AGENT_READ} IN COMPARTMENT <compartment_name> |
Allow Stack Monitoring to manage agents in compartment |
ALLOW resource stackmonitoringconfig 'AutoPromoteHost' TO {APPMGMT_MONITORED_INSTANCE_ACTIVATE} IN COMPARTMENT <compartment_name> |
Allow Stack Monitoring to activate management agent plugin in compartment |
ALLOW resource stackmonitoringconfig 'AutoPromoteHost' TO {INSTANCE_UPDATE, INSTANCE_READ, INSTANCE_AGENT_PLUGIN_INSPECT} IN COMPARTMENT <compartment_name> |
Allow Stack Monitoring to update compute instance configuration in compartment, in order to activate management agent plugin |
Automatic Promotion using the UI:
To enable host auto promotion using the UI, navigate to the Promote to Full Monitoring page, click Enable host auto promotion, then click Confirm.
This will enable both the configuration setting for auto promote when a management agent is registered, as well as the configuration setting for Compute auto activate plugin when a compute instance is launched. When, using the CLI, only one configuration is enabled, the UI will not indicate host auto promotion as enabled and will offer an option to enable the missing configuration.
Host Auto Promotion and Compute Auto Activation can also be enabled/disabled from Config Manager, on the Onboard configuration dashboard.
Promotion using the OCI-CLI:
Execute the following OCI-CLI commands to enable automatic promotion for a compartment; where <compartment_OCID> is the OCID of the compartment:
oci stack-monitoring config create-auto-promote-config --resource-type HOST --is-enabled true --compartment-id <compartment_OCID>oci stack-monitoring config create-compute-auto-activate-plugin-config --is-enabled true --compartment-id <compartment_OCID>Both configurations need to be created and set to enabled, for automatic promotion to work for compute instances. When only compute-auto-activate-plugin-config is enabled, the management agent plugin will be enabled but, similar to a manually installed management agent, the agent will not be promoted to full monitoring.
Manual Promotion
Once the Management Agent has been installed, promotion can be performed by going to the Promote to full monitoring page, identifying the OCI compute instance or on-premises host in the list of promotable resources, and clicking the Promote button. Review the values and click Promote Resource to start the promotion process.
For non-OCI GPU hosts, you will need to manually select the GPU license.
Alternatively, you can go to the Resource discovery page and click Discover New Resource to enter the appropriate values manually.
| Input Field | Description |
|---|---|
| Resource Name | FQDN of the OCI compute instance |
| Management Agent | The management agent running on the OCI compute instance you wish to promote. |
Disable automatic promotion
To disable automatic promotion for a compartment, execute the following CLI commands:
-
Search for the configuration
IDs <config_id>:oci stack-monitoring config list --type AUTO_PROMOTE --lifecycle-state ACTIVE --compartment-id <compartment-id>oci stack-monitoring config list --type COMPUTE_AUTO_ACTIVATE_PLUGIN --lifecycle-state ACTIVE --compartment-id <compartment-id> -
Disable host auto promotion:
oci stack-monitoring config update-auto-promote-config --config-id <config_id> --is-enabled falseoci stack-monitoring config update-compute-auto-activate-plugin-config --config-id <config_id> --is-enabled false
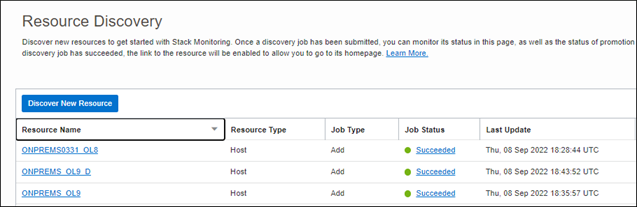
Checking the Status of the Discovery Job
The job's status and logs can be viewed within Stack Monitoring under the Resource Discovery page. From the Resource Discovery page search for the submitted job with a Resource Name matching the name of the host, a Resource Type of “Host”, and with a job type of “Add”. Once the Job Status is “Succeeded” click the name of the host under Resource Name to navigate to the host’s homepage.
Post-discovery Steps
Once the host has been promoted, verify the host name is the expected FQDN. If the host does not have the expected FQDN and is still listed as available to promote from the Promote to Full Monitoring page, the host name must be updated using the following CLI commands:
To view the name of the host execute the following CLI command:
oci stack-monitoring resource get --resource-id ocid1.stackmonitoringresource.<Host_Resource_OCID>To correct the hostname execute the following CLI command:
oci stack-monitoring resource update --resource-id ocid1.stackmonitoringresource.<Host_Resource_OCID> --host-name fully.qualified.domain.nameOnce the host has been promoted, the next step is to discover the resources running on the host, such as WebLogic Server or Oracle Database.
After discovering the resources, you will need to create the associations between the host and these resources. Refer to Associating Resources with a Host under Updating Application Topology for details.
Promote to Full Monitoring of Auto-discovered Resources
Some resources types can be automatically discovered if you have enabled the Resource Discovery and Monitoring features of OS Management Hub. After discovery, basic monitoring for these resources automatically starts. To enable full monitoring of these resources, you need to take it through the promote to full monitoring process.
Promotion to full monitoring involves specifying additional identifying parameters and monitoring credentials in order to complete the discovery and fully monitor the resource.
Promotion to full monitoring is supported for the following resource types:
- Oracle Database
- WebLogic Server
- Host
Promotion to full monitoring is currently not supported for these other types:
- Listener
- Oracle HTTP Server
- Apache Server
- Tomcat
The prerequisites and input parameters for promotion are the same as the user initiated discovery.
Promotion, unlike discovery, pre-populates information related to the resource. Be sure to validate this information and make sure that it is correct.
User-initiated Discovery
You can initiate resource discovery from the Stack Monitoring UI. To access Stack Monitoring, sign in to the Oracle Cloud Infrastructure Console and then access Stack Monitoring via the Oracle Cloud Infrastructure Console main menu. Open the navigation menu, click Observability & Management. Under Application Performance Monitoring, click Stack Monitoring.
- From the left pane, under Resources, click Resource Discovery. The Resource Discovery page displays.
- Click Discover New Resource. The Resource Discovery region displays.
- Select a resource type from the Resource Type drop-down menu.
You can select from the following resource types:
- Enter the resource type discovery details.
- Click Discover New Resource. A new resource discovery job is created and is shown in the table.
Oracle Database
You can discover external databases (outside OCI), both single-instance Oracle Databases and Oracle RAC instances, including the DB System using the Stack Monitoring service. The entire db system is discovered as part of an Oracle Database discovery.
- DB System including its components (Listener, ASM, etc) is discovered as part of an Oracle Database discovery.
- DB System discovery & monitoring is supported only in LINUX environments.
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
- Hostname Prerequisites
- Agent Prerequisites
- Policy Prerequisites
- Monitoring Credentials Prerequisite
- If your Oracle Database is using TCPS (Optional)
- If your Oracle Database is using older password versions
Hostname Prerequisites
Ensure the hostname -d command returns the domain name, or the hostname -a command returns the correct shortname, as first alias. The shortname appears in the HOST_NAME column of the v$instances table of the database to discover. This can be done by updating the /etc/hosts file to return the correct alias as above to be the first alias.
Agent Prerequisites
- Each node of the Oracle Database cluster must have a locally installed Management Agent.
-
Ensure that the
mgmt_agentororacle-cloud-agentuser, based on type of agent installed, is included in the Oracle Inventory Group (typically,oinstall) taken from/etc/oraInst.loc, to be able to execute thelsnrctl,srvctl, andcrsctlcommands.Use the following instruction to grant
oinstallprivileges to themgmt_agentororacle-cloud-agentuser , based on type of agent installed:- Host with Oracle Cloud Agent:
usermod -aG oinstall oracle-cloud-agent - Host with stand-alone agent:
usermod -aG oinstall mgmt_agent
- Host with Oracle Cloud Agent:
-
The group must have execute privilege on Oracle install directory.
Example of adding group execute permission to the directory:
chmod g+x /u01/app/oracle
After granting the OS privileges, use the following instructions to restart the agent. Use the appropriate instructions for your agent and OS, respectively:
- Oracle Cloud Agent:
sudo systemctl stop oracle-cloud-agentThen start the agent using the start command.
- Stand-alone agent:
sudo systemctl stop mgmt_agentThen start the agent using the start command.
Policy Prerequisites
| Policy | Description |
|---|---|
ALLOW DYNAMIC-GROUP Management_Agent_Dynamic_Group TO USE METRICS IN COMPARTMENT <compartment_name> where target.metrics.namespace = 'oracle_oci_database_cluster' |
Allow the agent to upload metrics to Telemetry into 'oracle_oci_database_cluster' namespace. Here, Management_Agent_Dynamic_Group is a dynamic group of management agents in a compartment.
|
allow group <Stack Monitoring Admin Users> to manage dbmgmt-family in tenancy |
Allow the users in the specified group to manage database management resources in a tenancy. |
Monitoring Credentials Prerequisite
Prior to discovering a database within Stack Monitoring, ensure you have access to the monitoring user. You can either use DBSNMP user that is built-in with the Oracle Database and has the privileges required to monitor the database OR create a custom user with only the necessary privileges . Steps to create a database monitoring user can be found in CMOS note KB57458.
For ASM:
- You need to use an ASMSNMP user profile or its privileges.
- User should have secret password for ASM. To get started with creating a secret, see Managing Secrets.
TCPS-enabled Oracle Database Prerequisite
Stack Monitoring supports both TCP and TCPS connectivity protocols for Oracle databases. TCPS protocol enables an Oracle application on a client to communicate with remote databases through TCP/IP and SSL, which provides higher security than TCP alone. This new listener can be used to talk to database via a secure channel. To discover a database with TCPS, the prerequisite would be to add a TCPS listener to the Oracle database and access to the wallet location as shown in the following four steps.
Stack Monitoring supports both the use of Java KeyStore (JKS) and Truststore (PKCS).
Step 1: Configuring the Oracle Database and listener to support TCPS, see Configuring Transport Layer Security Authentication.
Step 2: Import KeyStore/TrustStore into Management Agent and update its permissions.
- Identify and export the Oracle Database wallet location according to the KeyStore type used (PKCS or JKS)..
PKCS
export WALLET_LOCATION=<database_wallet_location>/dbwalletsJKS
export WALLET_LOCATION=<database_wallet_location>/jkswallets - Copy the wallet to a secure, readable directory on the agent host.
cp -r $WALLET_LOCATION <secure_readable_dir>/ - Update the wallet permission.
On OCI Compute
PKCS
sudo chown -R oracle-cloud-agent:oracle-cloud-agent <secure_readable_dir>/dbwalletsJKS
sudo chown -R oracle-cloud-agent:oracle-cloud-agent <secure_readable_dir>/jkswalletsOn on-premises Compute:
PKCS
sudo chown -R mgmt_agent:mgmt_agent <secure_readable_dir>/dbwalletsJKS
sudo chown -R mgmt_agent:mgmt_agent <secure_readable_dir>/jkswallets
Step 3: Create an OCI Secret.
To get started with creating a secret, see Managing Secrets.
Secret Examples:
PKCS
{
"sslTrustStoreType": "PKCS12",
"sslTrustStoreLocation": "/<secure_readable_dir>/dbwallets/cwallets/ewallet.p12",
"sslTrustStorePassword": "<truststore_password>",
"sslKeyStoreType": "PKCS12",
"sslKeyStoreLocation": "/<secure_readable_dir>/dbwallets/swallets/ewallet.p12",
"sslKeyStorePassword": "<truststore_password>",
"sslServerCertDn": "C=US,O=MyCorp,CN=sslclient"
}
JKS
{
"sslTrustStoreType": "JKS",
"sslTrustStoreLocation": "/<secure_readable_dir>/jkswallets/truststore.jks",
"sslTrustStorePassword": "<truststore_password>",
"sslKeyStoreType": "JKS",
"sslKeyStoreLocation": "/<secure_readable_dir>/jkswallets/keystore.jks",
"sslKeyStorePassword": "<truststore_password>",
"sslServerCertDn": "C=US,O=MyCorp,CN=sslclient"
}
Step 4: Validate Policies
In addition to the creation of a secret, the Stack Monitoring admin group must be granted the ability to read the vault where the secret is kept. Please see Create required policies for more information on granting read permission on a secret-family within a specified compartment.
If your Oracle Database is using older password versions
For databases that are configured to use password version less than 12 (SQLNET.ALLOWED_LOGON_VERSION < 12 ), such as certain E-Business Suite databases, follow these additional steps to configure the Management Agent to communicate with the database using older password versions by setting an appropriate SQLNET.ALLOWED_LOGON_VERSION value in the agent configuration.
These instructions apply to the agent running on-premises:
- Modify this file
/opt/oracle/mgmt_agent/agent_inst/config/emd.propertiesto add the property:dbaas.ALLOWED_LOGON_VERSION = 8Values can be 8 / 10 / 11 /12 / 12a depending on the allowed login version you require.
- Restart the agent.
sudo systemctl restart mgmt_agent
These instructions apply to the agent running on OCI Compute:
- Modify the file
/var/lib/oracle-cloud-agent/plugins/oci-managementagent/polaris/agent_inst/config/emd.propertiesto add this property:dbaas.ALLOWED_LOGON_VERSION = 8Values can be 8 / 10 / 11 /12 / 12a depending on the allowed login version you require.
- Restart the agent.
sudo systemctl restart oracle-cloud-agent
Oracle Database Discovery Instructions
- DB System including its components (Listener, ASM, etc) is discovered as part of an Oracle Database discovery.
- DB System discovery & monitoring is supported only in LINUX environments.
Discovering DB System if Oracle Database has already been discovered
- UI Discovery for the first DB System of the cluster :
From the Resource Discovery page, complete the fill-in-the-blank Oracle Database discovery.
For more information regarding UI discovery inputs, see the UI Discovery Input table.
-
CLI Discovery for the remaining DB System resources:
Note
For an Oracle Database that has already been discovered, complete the following steps to discover the related DB System.- Navigate to the Configuration tab within the newly create Oracle Database homepage. Copy the following fields from the General OCI Properties table into a notepad:
Property Name CLI Variable Name Notes OCID <Database_Resource_OCID> compartmentId <Compartment_OCID> managementAgentId <Additional_Agent#_OCID> This is the OCID of the agent used during the CLI discovery. - Copy the name of the Oracle Database resource from the top of the Stack Monitoring Oracle Database homepage.
- Obtain the Management Agent OCID of the other nodes in the cluster:
-
Navigate to Observability & Management, go to Management Agents, and click Agents.
- For each additional agent in the DB System cluster, select the action menu.
- Select Copy OCID to clipboard.
Agent OCID CLI Variable Name 1st additional node in cluster <Additional_Agent1_OCID> 2nd additional node in cluster (etc) <Additional_Agent2_OCID>
-
- Update the
JSON_INPUT_FILEwith the values obtained, and use the following syntax to discover an Oracle DB System:oci stack-monitoring discovery-job create --compartment-id "<Compartment_ID>" --from-json file://<JSON_INPUT_FILE>
For more information regarding CLI discovery inputs, see the CLI Discovery Input table.
The following is a JSON payload examples to discover the remaining DB System resources:
{ "discoveryType": "REFRESH", "discoveryClient": "APPMGMT", "compartmentId": "<COMPARTMENT_OCID>", "discoveryDetails": { "agentId": "<OCID of the Management agent>", "resourceType": "ORACLE_DATABASE", "resourceName": "<Resource name to display in Stackmonitoring UI>", "properties": { "propertiesMap": { "resource_id":"<DATABASE_OCID>", "asm_host":"<ASM HOSTNAME>", "asm_service_name":"+ASM", "is_asm_discovery":"true", "asm_port":"1521", "additional_agent_1":"ADDITIONAL_AGENT1_OCID", "additional_agent_2":"ADDITIONAL_AGENT2_OCID" } }, "credentials": { "items": [ { "credentialName" : "QVNNUGFzc3dvcmRJblZhdWx0", "credentialType" : "U1NMX1NFQ1JFVF9JRA==", "properties": { "propertiesMap": { "ASMUserName": "<ASM user name in base64 encoded format>", "PasswordSecretId": "<Encoded ASM user secret ocid in BASE64 encoded format>", "ASMRole":"<ASM user role in base64 encoded format>" } } } ] } } } - Navigate to the Configuration tab within the newly create Oracle Database homepage. Copy the following fields from the General OCI Properties table into a notepad:
For more information regarding refreshing your Oracle DB System, see Oracle Database System Components Refresh.
Oracle Database
Discover an Oracle Database including database system using the UI: From the Resource Discovery page, complete the fill-in-the-blank UI to discover an Oracle Database including database system and its components.
To include multiple agents when discovering a database system for multi-node RAC, complete the following steps:
Discovery Input
-
UI Discovery Input
Input field Description Resource Name Name of the database DNS hostname or SCAN Name Domain Name System (DNS), or Single Client Access Name (SCAN) for the database Port Port used by the database outside of Oracle Cloud Infrastructure for database connections Service Name Service name for the database outside of Oracle Cloud Infrastructure that will be used by the connection Protocol Protocol used for the Oracle Database. Select either TCP or TCPS protocol Database user password secret in <compartment_name> compartment Select the secret that contains the database user password from the drop-down list. This field is only displayed if TCPS is selected in the Protocol field. See below. Management Agents Management Agents monitoring the host on which the database is installed Note
For database systems that span multiple hosts, select all Management Agents deployed on all hosts of the database system.Database Credentials for Monitoring
. - Username
Username of the Oracle Database monitoring credentials - Password
Password in base 64 encoded format, of the Oracle Database monitoring credentials - Role
Database role in base 64 encoded format, of the database monitoring user (Normal or SYSDBA) ASM Information Management Agent Management Agent monitoring the host on which the database is installed. For discovering cluster and listener agent should be installed on the database host. Automatic Storage Manager Enable or Disable. Enabled by default. DNS hostname or Scan name The default dns or SCAN name where the ASM instance lives. Port The port used by ASM. Default value: 1521 Service Name The ASM service name ASM Credentials for Monitoring Username ASM user name in base 64 encoded format ASM user password secret in the current compartment Password secret in base 64 encoded format as defined in OCI Vault service Role Role in base 64 encoded format. SYSMAN by default. Possible values: SYSASM, SYSDBA, SYSOPER Discover In Stack Monitoring and Log Analytics (recommended) Discovery results will be sent to Stack Monitoring and Log Analytics. Stack Monitoring only Discovery results will be sent to Stack Monitoring only. Log Analytics only Discovery results will be sent to Log Analytics only. License Enterprise Edition The resource will be assigned an Enterprise Edition license. Standard Edition The resource will be assigned an Standard Edition license. Tags (under Show advanced options) Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags.
Tag Namespace
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator.
Tag Key
Specify the name you use to refer to the tag.
Tag Value
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging.
-
CLI Discovery Input
CLI Input Variable Description <Additional_Agent1_OCID> 1st additional node in cluster <Additional_Agent2_OCID> (etc) 2nd additional node in cluster (continue for each additional node in the cluster) Agent_OCID Agent of the initial discovery OCID Compartment_OCID The compartment OCID where the Oracle Database System will be monitored
Pluggable Database
Prerequisites:
-
Management Agent is required for discovery. For more information, see Step 3: Install Management Agents.
- Before discovering a PDB, you must first discover the CDB.
From the Resource Discovery page, complete the fill-in-the-blank UI to discover the PDB.
| Input field | Description |
|---|---|
| Resource Name | Name of the database. |
| Select CDB | Container DB that contains the Pluggable DB. |
| DNS hostname or SCAN Name | Domain Name System (DNS), or Single Client Access Name (SCAN) for the database. |
| Port | Port used by the database outside of Oracle Cloud Infrastructure for database connections. |
| Service Name | Service name for the database outside of Oracle Cloud Infrastructure that will be used by the connection. |
| Protocol | Protocol used for the Oracle Database. Select either TCP or TCPS protocol. |
| Database user password secret in <compartment_name> compartment | Select the secret that contains the database user password from the drop-down list. This field is only displayed if TCPS is selected in the Protocol field. See below. |
| Management Agent | Management Agent monitoring the host on which the database is installed. |
|
Database Credentials for Monitoring |
. |
|
Username of the Oracle Database monitoring credentials. |
|
Password of the Oracle Database monitoring credentials. |
|
Database role of the database monitoring user (Normal or SYSDBA). |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Oracle WebLogic Domain
Stack Monitoring supports the discovery and monitoring of both static and dynamic WebLogic Servers and Clusters. A configuration property on the resource home page indicates whether the resource is static or dynamic.
When discovering WebLogic, Oracle Access Manager (OAM), Oracle Identity Manager (OIM), Oracle HTTP Server (OHS), Oracle Service-Oriented Architecture (SOA), Oracle Service Bus (OSB) and Oracle Weblogic Node Manager are also automatically discovered. If your WebLogic domain has already been discovered, use the steps in Weblogic Domain Refresh to discover OAM, OIM, OHS, SOA, OSB and Oracle Weblogic Node Manager.
Oracle Weblogic Node Manager is used to manage, especially to start, the WebLogic server from the Admin Console, which can be accessed remotely.
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
-
For OSB, ensure that the monitoring is service bus monitoring is enabled.
- Login to FMW control:
http:/<host>:<port>/em - On service-bus home page, go to Operations tab.
- Check Monitoring check box.
- Login to FMW control:
-
For SOA discovery, the WebLogic user needs to have
Administratorprivileges. - For Oracle WebLogic Node Manager, to ensure computation of the
MonitoringStatusmetric for the Oracle WebLogic Node Manager resource, set thelistenAddressas All Local Addresses, a valid IP address, or a resolvable DNS name. Do not set thelistenAddressproperty tolocalhostornull. IflistenAddressmust be set tolocalhost, ensure that a local management agent is used for discovery to compute the status accurately.
If you are not using SSL, the following prerequisites do not apply.
If you have enabled the Oracle WebLogic Server with SSL, export the certificate from its keystore and import it in the Management Agent KeyStore. For more information about configuring SSL in WebLogic Server, see Configuring SSL.
Import TrustStore to the Management Agent
-
Designate a persistent subdirectory on the management agent's filesystem to hold the Stack Monitoring truststores and keystores. Export the certificate from the WLS instance JMX SSL keystore to the Stack Monitoring Truststore. For example, on a UNIX host:
keytool -exportcert -alias <alias of WLS SSL key> -file <Exported Cert Name> -keystore <path to the WLS SSL Keystore>.keystore -storepass <WLS SSL Keystore password> -rfc -
Import the WLS instance JMX SSL keystore to the Stack Monitoring Truststore on the management agent's filesystem.:
keytool -importcert -noprompt -alias <alias agent's truststore key> -file <Exported Cert Name>.cer -keystore AgentTrust.jks -storepass <Agent truststore password, default is "welcome"> -
Copy Stack Monitoring Truststore file and update its permissions.
Identify Management Agent readable secure location on the agent host.
cp <path_to_truststore_file/AgentTrust.jks <secure_readable_dir>/On OCI Compute:
sudo chown oracle-cloud-agent:oracle-cloud-agent <secure_readable_dir>/AgentTrust.jksOn on-premises Compute:
sudo chown mgmt_agent:mgmt_agent <secure_readable_dir>/AgentTrust.jks - Use the full Truststore path, e.g.
<secure_readable_dir>/AgentTrust.jksin the "TrustStore Path" of Resource Discovery if WebLogic Domain with T3S and "JKS" as the "Truststore Type".
Configure MBeans on Oracle WebLogic Servers
To collect the JVM performance metrics from platform MBeans, the MBeans must be made accessible through the runtime MBeanServer. Activate MBeans by logging in to your Oracle WebLogic Server and verify the activation by running the WLST script:
- Activate MBeans on Oracle WebLogic Servers
Activate MBeans by accessing each Oracle WebLogic Server by logging into it or from the WebLogic console as follows:
- Log in to your Oracle WebLogic Server:
Follow the user actions in the WebLogic Scripting Tool session demostration at Activating Platform MBeans on WebLogic Server 9.x to 10.3.2 versions in Enterprise Manager Cloud Control Middleware Management Guide.
- Access your WebLogic console:
Navigate to Domain > Configuration > General page > Advanced options. Select the Platform MBean Server Used check box.
If MBeans are not registered after you’ve followed the above steps, then start the Oracle WebLogic Servers with the following system property:
-Djavax.management.builder.initial=weblogic.management.jmx.mbeanserver.WLSMBeanServerBuilder - Log in to your Oracle WebLogic Server:
- Verify the Activation of MBeans
To verify if MBeans is successfully activated, run the WLST script that’s available at Using the Platform MBean Server in Fusion Middleware Developing Custom Management Utilities With JMX for Oracle WebLogic Server. The WLST script demonstrates how to use the Platform MXBeans to monitor the resources of a running Oracle WebLogic Server domain.
Ensure that MBeans are registered under
java.lang.
Ensure connectivity between management agent and all servers in WebLogic
During the discovery the Stack Monitoring Agent communicates with AdminServer for discovering the domain topology. Post discovery monitoring is done by communicating with managed servers directly. For this to happen, verify the following:
- Management Agent is able to communicate with all managed servers in the domain.
- The host and ports of the managed servers are accessible to the agent.
- If filters are configured to block incoming traffic on managed servers, adjust the filters for the agent to communicate with the managed servers.
WebLogic Scenario-Specific Discovery Outcomes
-
WebLogic domain has two Servers and one of them is down.
Discovery Result: The WebLogic domain will get discovered with only the one Server which is in a running state, ignoring the one not in a running state.
-
A WebLogic domain has a Cluster with two Servers and one of them is down.
Discovery Result: WebLogic Cluster will get discovered with only the one Server which is in a running state.
-
A WebLogic domain has a Cluster that contains only one Server which is not in running state.
Discovery Result: Neither the Cluster, nor the Server will be discovered
WebLogic Discovery Input
| Input field | Description |
|---|---|
| Resource Name | Name of the WebLogic Domain. |
| Administration Server Host | The fully-qualified host name where the WebLogic Administration Server is installed. |
| Administration Server Port | The port used for WebLogic Administration Server (Console). |
| Protocol | Protocol used for the WebLogic Server. The possible values are t3 and t3s. If you select t3s, TrustStore Path and TrustStore Type fields appear under WebLogic User for Monitoring. |
| Management Agent | Management Agent installed on the host where the WebLogic Administration Server is installed. |
|
WebLogic User for Monitoring |
. |
|
WebLogic Server username.
|
|
WebLogic Server user password. |
|
Fully qualified path - on the management agent's filesystem - of the Truststore file used to store the certificates of the trusted servers. |
|
Type of the TrustStore used for CA certificate management when establishing an SSL connection. Specify either: JKS or PKCS12. If the TrustStore type is not specified, the default TrustStore type, JKS, is used. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
E-Business Suite
When discovering E-Business Suite application (EBS) version 12.2, Weblogic Domain discovery is optional.
If Weblogic is included in the discovery and it fails, the discovery job status will be Partially Succeeded and only EBS resources will be monitored. If Weblogic is not included in the discovery, it can be discovered later on through refresh operation from EBS instance resource homepage.
The monitoring options for EBS 12.2 flexible discovery are available as follows:
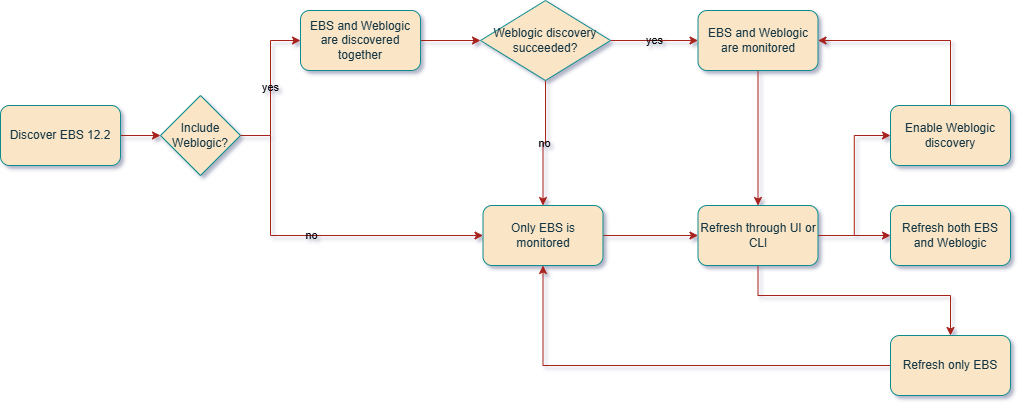
In EBS environments with more than a single node, only the Application Listener in the node where the agent is installed will be monitored.
For more information, see EBS Refresh.
EBS Topology
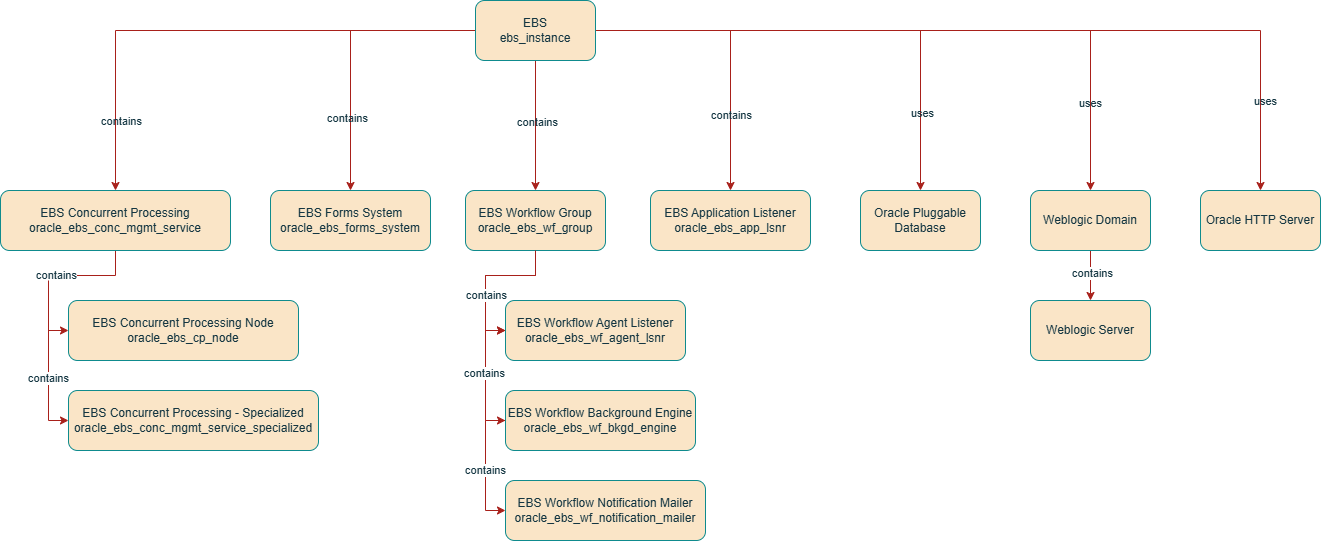
When an E-Business Suite instance is discovered, both EBS and WebLogic resources are discovered. OHS and Database discovery has to be done separately.
To monitor Oracle HTTP Server collocated in EBS, refer to "OHS Discovery". Once the OHS is discovered independently, an association can be created between EBS resource and OHS resource.
To monitor the EBS database, if the database is discovered first and then EBS is discovered later, the association of type uses will be automatically created between the EBS resource and the database resource at the end of EBS discovery. Here, EBS resource refers to a Stack Monitoring resource type ebs_instance and database resource refers to Stack Monitoring resource type oci_oracle_db or oci_oracle_pdb.
If the EBS is discovered prior to database discovery, the topology can be updated in two ways.
- Create Association Between EBS Instance and Database Resources
- Refreshing EBS topology
Create Associations:
Composite EBS resources cannot be associated with a host directly. However, EBS children resources can be associated as follows:
- EBS Concurrent Manager uses Host
- EBS CP Node uses Host
The following is the OCI CLI command syntax to create an association between two resources.
oci stack-monitoring resource associate --association-type uses --compartment-id "<Compartment_OCID>" --source-resource-id "<Resource_OCID>" --destination-resource-id "<Database_Resource_OCID>"For example:
oci stack-monitoring resource associate --association-type uses --<Compartment_OCID>
ocid1.compartment.oc1..unique_ID --<Source_Resource_OCID>
ocid1.stackmonitoringresource.oc1.iad.unique_ID --<Destination_Resource_OCID>
ocid1.stackmonitoringresource.oc1.iad.unique_IDIn the case of EBS, the above command can be used to create an association between EBS and database resources by specifying <Source_Resource_OCID> as EBS resource ID and <Destination_Resource_OCID> as database resource ID.
An EBS discovery, associated with its underlying resources, is represented in Stack Monitoring as seen in the following diagram:
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
- Configure MBeans on Oracle WebLogic Servers
- Verify Collection of Forms Sessions Data
- Set Up DNS in an Oracle E-Business Suite Environment
- Add the Database used by the E-Business Suite application.
If you haven't already done so, add the database that will be used for the E-Business Suite application. Refer to Oracle Database (Discovery)
- Agent permissions for Application Listener monitoring
- E-Business Suite Database Monitoring Requirements for Stack Monitoring
Verify Collection of Forms Sessions Data
Verify the collection of forms sessions data to view it later in the Forms System resource metrics by performing the following task. This is in addition to the steps performed in Oracle WebLogic Domain (Configure MBeans on Oracle WebLogic Servers). If this step is not configured, some of the Forms System metrics will not be collected.
When you log in to Oracle E-Business Suite, the system creates a user session in the database identified by a unique session ID (SID) by using the APPS schema credential. Each database session is associated with an Oracle E-Business Suite application user. This enables linking the database session with the application user for troubleshooting purposes. Using a Forms session, you can determine how the Oracle E-Business Suite user opened a database session.
- Log in to your Oracle E-Business Suite.
- From the user interface, navigate to System Administrator, click Profile, and then System.
- Ensure that the value of Sign-On: Audit Level is set to FORM. Set this at the site level.
- Ensure that the value of AuditTrail: Activate is set to YES.
Save the changes.
Set Up DNS in an Oracle E-Business Suite Environment
The Oracle E-Business Suite hosts must be able to detect one another on the network. For example, in the UNIX environment, the DNS servers are configured in the file /etc/resolv.conf on each host.
To verify that the DNS servers are configured correctly, run the command:
nslookup any_publicDomain_hostnameSubstitute <any_publicDomain_hostname> with the hostname of any other host of the EBS environment other than the localhost.
Here is an example of a successful output validating the DNS server is correctly configured:
$ nslookup node02.examplehost.com
Server: 937.486.274.354
Address: 937.486.274.354
Non-authoritative answer:
Name: node02.examplehost.com
Address: 135.756.247.46Agent permissions for Application Listener monitoring
Agent must be installed in the same host as EBS to monitor EBS Application Listener. Otherwise, the resource will always show as DOWN.
Ensure that the mgmt_agent or oracle-cloud-agent user, based on type of agent installed, is included in the Oracle Inventory Group (typically, oinstall) taken from /etc/oraInst.loc, to be able to execute the lsnrctl, srvctl, and crsctl commands.
Use the following instruction to grant oinstall privileges to the mgmt_agent or oracle-cloud-agent user , based on type of agent installed:
- Host with Oracle Cloud Agent:
usermod -aG oinstall oracle-cloud-agent - Host with stand-alone agent:
usermod -aG oinstall mgmt_agent
The group must have execute and read privileges on EBS-APPS install directory.
Example of adding group execute permission to the directory:
chmod -R g+x+r /u01/install/APPSAfter granting the OS privileges, use the following instructions to restart the agent. Use the appropriate instructions for your agent and OS, respectively:
- Stop the Agent
- For Oracle Linux 6:
- Oracle Cloud Agent:
sudo /sbin/initctl stop oracle-cloud-agent - Stand-alone agent:
sudo /sbin/initctl stop mgmt_agent
- Oracle Cloud Agent:
- For Oracle Linux 7
- Oracle Cloud Agent:
sudo systemctl stop oracle-cloud-agent - Stand-alone agent:
sudo systemctl stop mgmt_agent
- Oracle Cloud Agent:
- For Oracle Linux 6:
- Start the agent using the start command.
E-Business Suite Database Monitoring Requirements for Stack Monitoring
The Oracle database used to monitor the E-Business Suite (EBS) database should be discovered before discovering the EBS application. If the database is discovered first, it will be automatically associated with the EBS application once the EBS application discovery completes. If the EBS application discovery is performed before the database has been discovered, the association will need to be created manually.
Monitoring E-Business Suite requires specific privileges to access the EBS schema. The setup differs depending on type of database (Non-Container DB versus Container DB and Pluggable DB) used as your EBS datastore. Stack Monitoring supports the use of the EBS schema owner, typically APPS, as the database credentials when discovering EBS. It is preferred to create a monitoring user with only the privileges necessary to monitor an EBS application. You can use the same database user to monitor both the Oracle database containing the EBS schema and the EBS application. Steps to create a database monitoring user can be found in MOS Note: 2857604.1.
Database Grants
Once the EBS monitoring user has already been created with the required privileges, apply the necessary EBS application grants to the monitoring user. The specific privileges are defined in the code below, assuming that the EBS schema name is APPS. If the schema name is different in your setup, then replace APPSwith the actual schema name in the following code. Replace <your_monitoring_user> with the database monitoring user created using MOS Note: 2857604.1.
GRANT SELECT ON APPS.FND_OAM_CONTEXT_FILES TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_PRODUCT_GROUPS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONC_PROG_ONSITE_INFO TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_PROGRAMS_VL TO <your_monitoring_user>;
GRANT EXECUTE ON APPS.FND_OAM_EM TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_REQUESTS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_APPLICATION_VL TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_QUEUES TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_LOOKUPS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_WORKER_REQUESTS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_QUEUES_VL TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_OAM_FNDUSER_VL TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_FORM_SESSIONS_V TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CP_SERVICES TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_PROCESSES TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_SVC_COMPONENTS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_LOG_MESSAGES TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONCURRENT_PROGRAMS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_CONFLICTS_DOMAIN TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_ORACLE_USERID TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_APP_SERVERS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_NODES TO <your_monitoring_user>;
GRANT SELECT ON APPS.ICX_SESSIONS TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_USER TO <your_monitoring_user>;
GRANT SELECT ON APPS.FND_RESPONSIBILITY TO <your_monitoring_user>;
GRANT EXECUTE ON APPS.FND_PROFILE TO <your_monitoring_user>;
GRANT SELECT ON APPS.WF_DEFERRED TO <your_monitoring_user>;
GRANT SELECT ON APPS.WF_NOTIFICATION_IN TO <your_monitoring_user>;
GRANT SELECT ON APPS.WF_NOTIFICATION_OUT TO <your_monitoring_user>;These grants can be applied by executing ebs_apply_grants.sh (included in EBS Scripts) as follows:
- Login to the EBS database host
- Source the EBS environment
- Run script as:
sh ebs_apply_grants.sh <monitoring user> <SYSTEM_password> <APPS_password>
Example:
sh ebs_apply_grants.sh MONCS manager appsIf the EBS instance is running against a Pluggable Database (PDB), grant an additional privilege to the EBS monitoring user:
GRANT INHERIT PRIVILEGES ON USER <monitoring user> TO APPS;After applying the grants, execute ebs_validate_grants.sql (included in EBS Scripts) as follows to verify they are in place:
- Login to the EBS database host
- Login to the EBS database as the EBS monitoring user
- Run the validation script as:
@ebs_validate_grants.sql
The expected output of the script when all grants are in place is like this:
TABLE_NAME PRIVILE STATUS
------------------------------ ------- -------
FND_OAM_EM EXECUTE GRANTED
FND_PROFILE EXECUTE GRANTED
FND_APPLICATION_VL SELECT GRANTED
FND_APP_SERVERS SELECT GRANTED
FND_CONCURRENT_PROCESSES SELECT GRANTED
FND_CONCURRENT_PROGRAMS SELECT GRANTED
FND_CONCURRENT_PROGRAMS_VL SELECT GRANTED
FND_CONCURRENT_QUEUES SELECT GRANTED
FND_CONCURRENT_QUEUES_VL SELECT GRANTED
FND_CONCURRENT_REQUESTS SELECT GRANTED
FND_CONCURRENT_WORKER_REQUESTS SELECT GRANTED
TABLE_NAME PRIVILE STATUS
------------------------------ ------- -------
FND_CONC_PROG_ONSITE_INFO SELECT GRANTED
FND_CONFLICTS_DOMAIN SELECT GRANTED
FND_CP_SERVICES SELECT GRANTED
FND_FORM_SESSIONS_V SELECT GRANTED
FND_LOG_MESSAGES SELECT GRANTED
FND_LOOKUPS SELECT GRANTED
FND_NODES SELECT GRANTED
FND_OAM_CONTEXT_FILES SELECT GRANTED
FND_OAM_FNDUSER_VL SELECT GRANTED
FND_ORACLE_USERID SELECT GRANTED
FND_PRODUCT_GROUPS SELECT GRANTED
TABLE_NAME PRIVILE STATUS
------------------------------ ------- -------
FND_RESPONSIBILITY SELECT GRANTED
FND_SVC_COMPONENTS SELECT GRANTED
FND_USER SELECT GRANTED
ICX_SESSIONS SELECT GRANTED
WF_DEFERRED SELECT GRANTED
WF_NOTIFICATION_IN SELECT GRANTED
WF_NOTIFICATION_OUT SELECT GRANTED
INHERIT_PRIVILEGES_STATUS
--------------------------
INHERIT PRIVILEGES GRANTEDIf any of the grants are missing, the impact is described as follows:
| Table/View | Privilege | Resources involved | Mandatory/Optional | Impact if missing |
|---|---|---|---|---|
| FND_OAM_CONTEXT_FILES | SELECT | Discovery | Mandatory | Discovery will not proceed |
| ICX_SESSIONS | SELECT | EBS instance | Optional | Discovery proceeds but metric collection is impacted for the involved resources. |
| FND_USER | SELECT | |||
| FND_RESPONSIBILITY | SELECT | |||
| FND_PROFILE | EXECUTE | |||
| FND_APPLICATION_VL | SELECT |
EBS instance EBS Forms System |
||
| FND_CONCURRENT_REQUESTS | SELECT |
EBS instance EBS Concurrent Processing EBS Workflow Agent Listener |
||
| FND_CONCURRENT_PROGRAMS_VL | SELECT | |||
| FND_CONCURRENT_PROGRAMS | SELECT | |||
| FND_CONCURRENT_QUEUES_VL | SELECT |
EBS Concurrent Processing EBS Concurrent Processing - Specialized EBS Workflow Notification Mailer |
||
| FND_NODES | SELECT |
EBS Concurrent Processing EBS Concurrent Processing - Specialized |
||
| FND_ORACLE_USERID | SELECT | EBS Concurrent Processing | ||
| FND_CONFLICTS_DOMAIN | SELECT | |||
| FND_OAM_EM | EXECUTE | |||
| FND_LOOKUPS | SELECT | |||
| FND_OAM_FNDUSER_VL | SELECT | |||
| FND_CONCURRENT_WORKER_REQUESTS | SELECT |
EBS Concurrent Processing EBS Workflow Notification Mailer |
||
| FND_FORM_SESSIONS_V | SELECT | EBS Forms System | ||
| WF_DEFERRED | SELECT | EBS Workflow Notification Mailer | ||
| WF_NOTIFICATION_IN | SELECT | |||
| WF_NOTIFICATION_OUT | SELECT |
E-Business Discovery Input
| Input field | Description |
|---|---|
| Resource Name | Name of the E-Business Suite instance. |
| Version | Version of E-Business Suite (12.1 or 12.2). If 12.2 is selected, E-Business Suite WebLogic Server and WebLogic Administration Server Credentials regions are displayed. |
| E-Business Suite Database | . |
|
Host on which the external database is installed |
|
Port used by the database for database connections. |
|
Server name of the database used for database connections. |
|
Protocol used for the Oracle Database. Select either TCP or TCPS protocol. |
|
Select the secret that contains the database user password from the drop-down list. This field is only displayed if TCPS is selected in the Protocol field. Correct configuration for TCPS can be found in the following documentation, see TCPS-enabled Oracle Database Prerequisite. |
| Database Credentials |
. |
|
Database user who has the necessary privileges on the underlying views (e.g. APPS).
|
|
Database user password. |
|
Role of the database user (NORMAL or SYSDBA) |
| E-Business Suite WebLogic Server (E-Business Suite 12.2) | . |
|
Name of the host where the WebLogic Administration Server is installed. |
|
Port used for WebLogic Administration Server (Console). |
|
Remote Method Invocation (RMI) protocol: t3 or t3s. If you select t3s, the TrustStore Path and TrustStore Type fields appear under WebLogic User for Monitoring. |
| WebLogic Administration Server Credentials (E-Business Suite 12.2) | . |
|
WebLogic Administration Server user.
|
|
WebLogic Administration Server user password. |
|
Path to the TrustStore file used to store public keys of trusted servers. |
|
Type of the TrustStore used for CA certificate management when establishing an SSL connection. If the TrustStore type is not specified, the default TrustStore type, JKS, is used. |
| Management Agent | Management Agent monitoring the host where E-Business Suite is installed. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
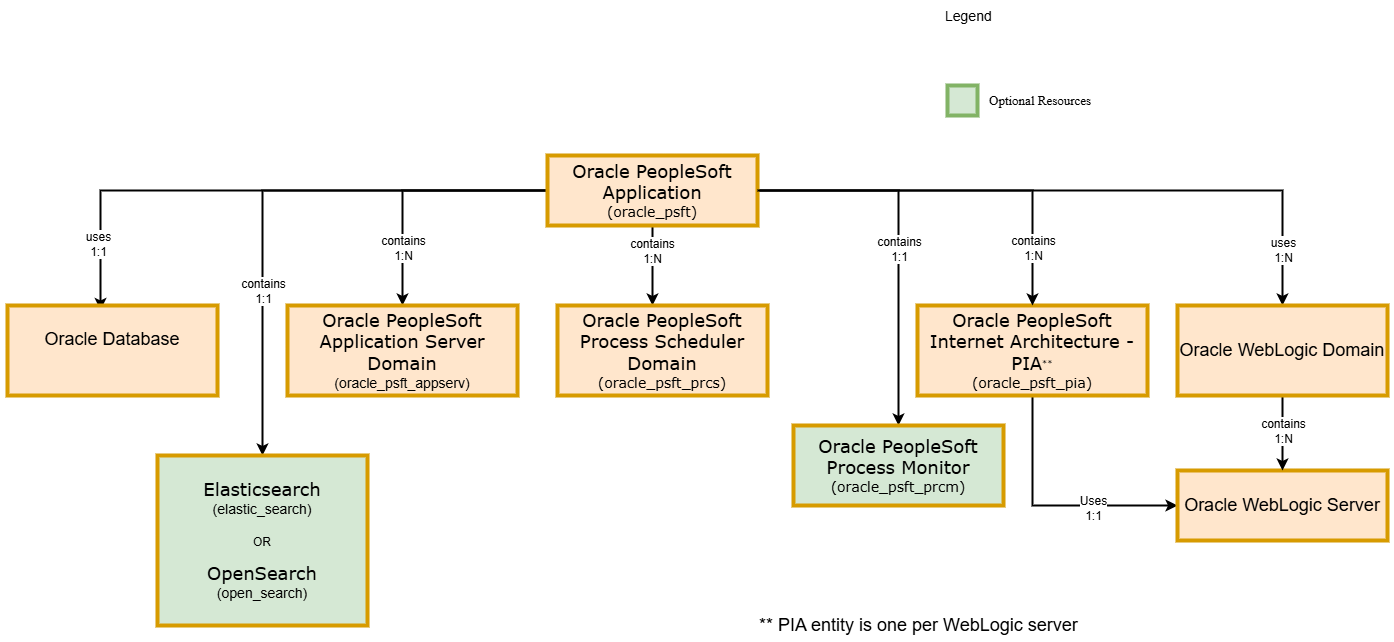
PeopleSoft
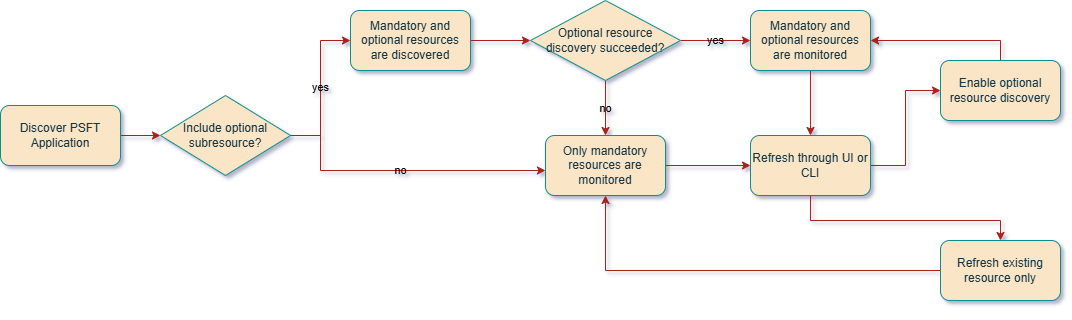
When discovering PSFT Application, some of its subresources are mandatory for the discovery job to succeed and some others are optional.
Mandatory resources: resources that are always included in discovery and cannot be deselected by the user.
- Application Server Domain
- PIA
Optional resources:
- Process Scheduler
- Process Monitor
- Search Engine
During discovery, if any of the resources fail, the discovery job status will be marked as Partial Success, while if all the mandatory resources fail, then the discovery job status will be marked as Failed. If optional resources are not included in the discovery, they can be discovered later on through refresh operation from PSFT resource homepage.
The monitoring options for PSFT flexible discovery are available as follows:
Each resource family may include one or more resources such as Application Server Domain, Process Scheduler Domain, and PeopleSoft Internet Architecture (PIA) with its underlying Weblogic domain(s) which may span across several servers.
Composite PeopleSoft resources cannot be associated with a host directly. However, PeopleSoft children resources can be associated as follows:
- Application Server Domain uses Host
- Process Scheduler Domain uses Host
- PIA uses Host
- Process Monitor uses Host
During PeopleSoft discovery resources will be validated in each family with one common credential set for that family. That means that all of the Application Server Domains will be validated using a single credential set, all of the Process Scheduler Domains will be validated using a single credential set, and so on. The successfully validated resources will be discovered and the resources failing validation will be ignored.
The ignored resources can be found in the Job report with the line The following resources could not be discovered: After rectifying the problem, the user can execute the REFRESH job to discover those resources.
A PeopleSoft deployment at the end of a successful discovery is represented in Stack Monitoring as seen in the following diagram:
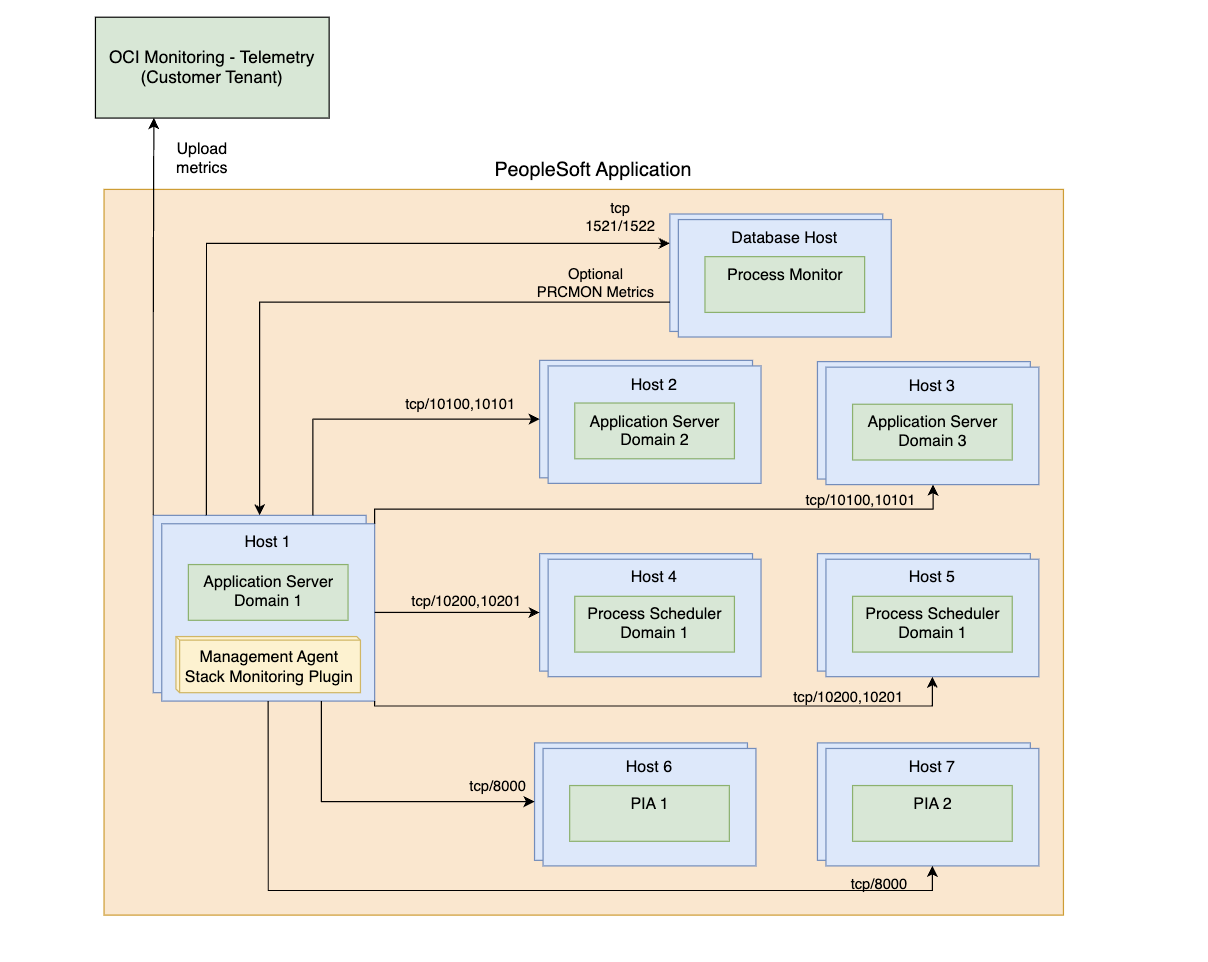
The port access that is needed from the monitoring agent host to the hosts and services that are part of the PeopleSoft deployment is described in the following diagrams. The diagrams indicate two scenarios:
- Management Agent is located on one of the PeopleSoft hosts itself:
- Management Agent is located on a remote host:
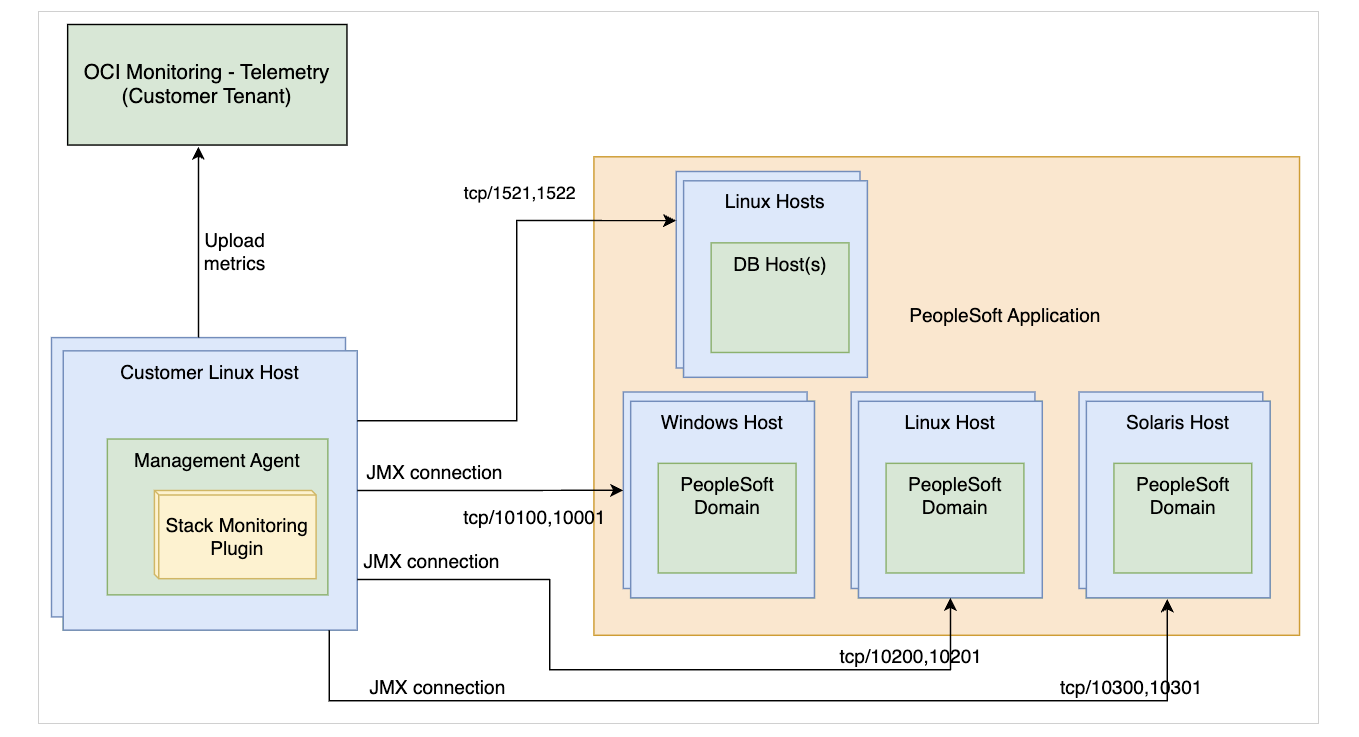
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
- Discover PeopleSoft Database
- DB Grant Privileges for PeopleSoft Monitoring
- Enable PeopleSoft Performance Monitor for Pure Internet Architecture (PIA)
- Prerequisites for Application Server and Process Scheduler Domains
- Identify Domains to be Discovered
- Adding domains manually
- Enable Search Engine discovery in PeopleSoft
- Enable Process Monitor discovery for PeopleSoft
Discover PeopleSoft Database
The Oracle Database containing the PeopleSoft (PSFT) schema should be discovered before discovering the PeopleSoft application. If the database is discovered first, the database will be automatically associated with PeopleSoft application once PeopleSoft resource discovery completes
If PeopleSoft application discovery is performed before the database has been discovered, the association will need to be created manually. See Application Topology for more information.
To Discover the Oracle Database, see Oracle Database.
DB Grant Privileges for PeopleSoft Monitoring
Monitoring PeopleSoft (PSFT) requires specific privileges to access the PSFT database schema. The setup differs depending on type of database (Non-Container DB versus Container DB and Pluggable DB) used as your PSFT datastore. Stack Monitoring supports the use of the PSFT schema owner, typically SYSADM, as the database credentials when discovering PSFT. It is preferred to create a monitoring user with only the privileges necessary to monitor a PSFT application. You can use the same database user to monitor both the Oracle database containing the PeopleSoft schema and the PeopleSoft application. Steps to create a database monitoring user can be found in MOS Note: 2857604.1.
To verify the monitoring user has the necessary grants, and apply any missing grants:
- Ensure that your monitoring user is not expired:
- Check the monitoring user status by running the following:
select username, account_status from dba_users where username='<your_monitoring_user>' - If your monitoring user shows EXPIRED, reset its password.
- Check the monitoring user status by running the following:
- Execute the following PeopleSoft Scripts.
To understand the specific grants to be applied, or to manually apply the apply the grants, see the list of commands below to be executed.
Database Privileges
The example code below uses:
- SYSADM as the schema name. If the schema name is different in your setup, then replace SYSADM with it accordingly in the following code.
-
<your_monitoring_user>as reference to the database monitoring user.<your_monitoring_user>is typically DBSNMP or MONUSER.
-
PeopleSoft Application Grants
GRANT SELECT ON SYSADM.PSSTATUS TO <your_monitoring_user>; GRANT SELECT ON SYSADM.PSRELEASE TO <your_monitoring_user>; GRANT SELECT ON SYSADM.PSPMAGENT TO <your_monitoring_user>; -
PeopleSoft Application Synonyms
CREATE OR REPLACE SYNONYM <your_monitoring_user>.PSSTATUS FOR SYSADM.PSSTATUS; CREATE OR REPLACE SYNONYM <your_monitoring_user>.PSRELEASE FOR SYSADM.PSRELEASE; CREATE OR REPLACE SYNONYM <your_monitoring_user>.PSPMAGENT FOR SYSADM.PSPMAGENT; -
Search Engine Grants
Note
Search Engine supports both Elasticsearch and OpenSearch.GRANT SELECT ON SYSADM.PS_PTSF_SRCH_ENGN TO <your_monitoring_user>; -
Search Engine Synonyms
Note
Search Engine supports both Elasticsearch and OpenSearch.CREATE OR REPLACE SYNONYM <your_monitoring_user>.PS_PTSF_SRCH_ENGN FOR SYSADM.PS_PTSF_SRCH_ENGN -
Process Monitor Grants
GRANT SELECT ON SYSADM.PSPRCSRQST TO <your_monitoring_user>; GRANT SELECT ON SYSADM.PSXLATITEM TO <your_monitoring_user>; -
Process Monitor Synonyms
CREATE OR REPLACE SYNONYM <your_monitoring_user>.PSPRCSRQST FOR SYSADM.PSPRCSRQST; CREATE OR REPLACE SYNONYM <your_monitoring_user>.PSXLATITEM FOR SYSADM.PSXLATITEM;
Enable PeopleSoft Performance Monitor for Pure Internet Architecture (PIA)
Enabling PPM agent (Enable PPM agent =1 ) is optional and is only required for PSFT discovery and Refresh. However, for regular monitoring and metric collection, PPM agent is not needed.
If the user chooses NOT to enable PPM agent for any reasons, Please follow any one of the alternatives listed below
1. Enable PPM agent until the discovery or refresh is finished, then disable it and restart domains.
2. Manually INSERT/DELETE all PSFT domain information . This will eliminate the need to enable “Enable PPM agent”.
To add the domains proceed to Adding domains manually, and to remove stale domains follow the steps in Identify Domains to be Discovered.
- Navigate to PeopleTools, go to Web Profile, click Web Profile Configuration, and search for the profile in use, for example, PROD.
- If not checked already, check the Enable PPM Agent check box.
- Restart all PIA domains.
All below Prerequisites needs to be performed for each Application Server and Process Scheduler domains.
PeopleSoft discovery assumes that the Remote Administration UserId/pwd for JMX access is the same for all application server domains, and also for all process scheduler domains.
Prerequisites for Application Server and Process Scheduler Domains
Enable the PeopleSoft Performance Monitor Agent
- Using
PSADMINcommand-line interface, select Application Server (Option 1) or Process Scheduler (Option 2) > Administer a domain (Option 1) > select domain > Edit configuration/log files menu(option 6) > Edit domain configuration file (Option 1) , this will open up the domain configuration files in edit mode -
under the PSTOOLS section, check the value for EnablePPM Agent. To Enable PPM Agents, set the value to 1, and save the file.
Enable JMX Agents
This prerequisite enables Stack Monitoring to collect availability and performance data for a PeopleSoft application.
-
Using
PSADMINcommand-line interface, select Application Server (Option 1) or Process Scheduler (Option 2) > Administer a domain (Option 1) > select domain > Edit configuration/log files menu(option 6) > Edit domain configuration file (Option 1) , this will open up the domain configuration files in edit mode -
Locate settings for PSTOOLS section and set below values
-
Ensure that the Remote Administration Port you intend to use is not being utilized by any other process on the host.
UserID-
UserIdshould be in text format. -
The same
UserIdand password should be used for all application server domains and process scheduler domains.
-
- Use the PSCipher utility to encrypt the password.
- Restart the Application server and Process Scheduler domains after configuring the Performance Collator property change below.
-
-
-
For PSFT version 8.59 and earlier only Remote Administration Port needs to be set. RMI port value will be set automatically based on the Remote Administration Port value incremented by
1. For example, if the Remote Administration Port is10100, then port10101will be used for PHC's RMI server. When you plan the port usage, this needs to be taken into account. Since 10101 is picked automatically in the above example, if that port is not free PSFT automatically picks any other random free port. Please ensure to review the domain configuration file after the configuration has been successfully saved and use these ports to connect in discovery.Example:
Enable Remote Administration=1 Remote Administration Port=10100 Remote Administration UserId=<the userid you have defined in step 2b> Remote Administration Password={V2.1}<encrypted password> -
For PSFT version 8.60 onwards, RMI port is controlled by one additional parameter in the config file. Ensure the value is set explicitly. Restart the Application server and Process Scheduler domains after configuring the Performance Collator property.
Example:
Enable Remote Administration=1 Remote Administration Port=10100 Remote Administration RMI Server Port=10101 Remote Administration UserId=<the userid you have defined in step 2b> Remote Administration Password={V2.1}<encrypted password>
Note
Please ensure that the above saved setting shows correctly in the configuration file after the changes are saved. -
Enable the Performance Collator Property
You can check the current value of Perf Collator in domain template files psprcsrv.ubx (Process scheduler) and psappsrv.ubx (Application Server) located under $PS_CFG_HOME
If the Perf Collator is enabled , you will see entry as below.
{PPM} Do you want Performance Collators configured (PSPPMSRV) (y/n)? [y]:If the Perf Collator is disabled , You would see entry as below.
{PPM} Do you want Performance Collators configured (PSPPMSRV) (y/n)? [n]:If the Performance Collator is already enabled, and changes were implemented to EnablePPM Agent or JMX values: Restart all domains.
If the Performance Collator is not already enabled proceed with the following steps:
- Using
PSADMINcommand-line interface, select Application Server (Option 1) or Process Scheduler (Option 2) > Administer a domain (Option 1) > select domain > Configure this domain (Option 4) - Enter
yfor the question:Do you want to continue (y/n). This option will shutdown the domain -
Check value of Perf Collator property.
- If the value set to
Yes, Collator is already enabled, no action is required. Then select Load config as shown (Option 14 for Application Server or Option 7 for Process Scheduler) -
If the value set to
No, enter10for Application server or Option 3 for Process scheduler to toggle the value toYes -
After confirming Perf Collator set to
Yes, select Load config as shown (Option 14 for Application scheduler or Option 7 for Process scheduler ) -
Finally select Boot this domain Option 1 to start the domain
Identify Domains to be Discovered
Stack Monitoring leverages the information stored within the Oracle Database to identify domains to be discovered or refreshed. To validate the list of current domains, execute the following query.
SELECT * FROM PSPMAGENT;Any domains returned by the query that no longer exist should be removed prior to discovering/refreshing the PeopleSoft Application.
To add a domain that is not listed, see Adding domains manually.
To remove the stale domains execute the following SQL as SYSADM or equivalent user. Repeat steps until all Stale domains removed.
- Backup the PSPMAGENT table prior to making changes. Ensure to replace <DATE> with the current timestamp.
create table PSPMAGENT_BKP_<DATE> as select * from PSPMAGENT; - Verify the backup table created has same content as parent table.
select * from PSPMAGENT MINUS select * from PSPMAGENT_BKP_<DATE>;
If the count of rows from PSPMAGENT match PSPMAGENT_BKP_<DATE>, proceed with the removal of stale domains.
delete from PSPMAGENT WHERE PM_AGENTID='&enter_agent_id_of_stale_domain';
Commit;Adding domains manually
Finally, check whether all valid domains are visible from the PSPMAGENT table. If any valid domains are not showing up for any reason, follow the instructions below:
The agent host should be able to reach the other hosts using the host name stored in PSPMAGENT table (typically the short host name). This can be achieved by fixing the DNS settings or by adding an entry for each host in /etc/hosts file
It is recommended to perform a backup of the PSPMAGENT table before proceeding. Steps to create the backup are provided.
Create a backup:
-
As system administrator or equivalent user take a backup of the table prior to making changes. Ensure to replace
<DATE>with the current time stamp:create table PSPMAGENT_BKP_<DATE> as select * from PSPMAGENT; -
Verify the backup table created has same content as parent table. The rows count from
PSPMAGENTshould match the rows count fromPSPMAGENT_BKP_<DATE>:select * from PSPMAGENT MINUS select * from PSPMAGENT_BKP_<DATE>;
Add a Process Scheduler Domain
INSERT INTO PSPMAGENT values
('&AGENT_ID','&PM_JMX_RMI_PORT','PSMONITORSRV','&DOMAIN_NAME','04','&DOMAIN_DIR','Y','&HOST_PORT:','1','1','N');Example:
SQL> INSERT INTO PSPMAGENT values
('&AGENT_ID','&PM_JMX_RMI_PORT','PSMONITORSRV','&DOMAIN_NAME','04','&DOMAIN_DIR','Y','&HOST_PORT:','1','1','N'); 2
Enter value for unique_agent_id: 1000
Enter value for pm_jmx_rmi_port: 10500
Enter value for domain_name: PRCSDOM02
Enter value for domain_dir: /u01/app/oracle/product/psfthcm-midtierlinux-2/ps_cfg_home/appserv/prcs/PRCSDOM02
Enter value for host_name: psfthcm-midtierlinux-2
old 2: ('&unique_agent_id','&PM_JMX_RMI_PORT','PSMONITORSRV','&DOMAIN_NAME','04','&domain_dir','Y','&host_name:','1','1','N')
new 2: ('1000','10500','PSMONITORSRV','PRCSDOM02','04','/u01/app/oracle/product/psfthcm-midtierlinux-2/ps_cfg_home/appserv/prcs/PRCSDOM02','Y','psfthcm-midtierlinux-2:','1','1','N')
1 row created.Add an Application Server Domain
INSERT INTO PSPMAGENT values
('&unique_agent_id','&JMX_RMI_PORT','PSMONITORSRV','&DOMAIN_NAME','01','&DOMAIN_DIR','Y','&host_name:&jolt_port','1','1','N');Example:
SQL> INSERT INTO PSPMAGENT values
('&unique_agent_id','&JMX_RMI_PORT','PSMONITORSRV','&DOMAIN_NAME','01','&DOMAIN_DIR','Y','&host_name:&jolt_port','1','1','N'); 2
Enter value for unique_agent_id: 1003
Enter value for jmx_rmi_port: 10500
Enter value for domain_name: APPDOM4
Enter value for domain_dir: /u01/app/oracle/product/psfthcm-midtierlinux-3/ps_cfg_home/appserv/APPDOM04
Enter value for host_name: psfthcm-midtierlinux-3
Enter value for jolt_port: 9033
old 2: ('&unique_agent_id','&JMX_RMI_PORT','PSMONITORSRV','&DOMAIN_NAME','01','&DOMAIN_DIR','Y','&host_name:&jolt_port','1','1','N')
new 2: ('1003','10500','PSMONITORSRV','APPDOM4','01','/u01/app/oracle/product/psfthcm-midtierlinux-3/ps_cfg_home/appserv/APPDOM04','Y','psfthcm-midtierlinux-3:9033','1','1','N')Add a PIA Server
INSERT INTO PSPMAGENT values
('&unique_agent_id','-1','WEBRESOURCE','&DOMAIN_NAME','02','&DOMAIN_DIR','Y','&host_name:&http_port:&https_port','1','1','N');Example:
INSERT INTO PSPMAGENT values
('&unique_agent_id','-1','WEBRESOURCE','&DOMAIN_NAME','02','&DOMAIN_DIR','Y','&host_name:&http_port:&https_port','1','1','N');
Enter value for unique_agent_id: 19
Enter value for domain_name: peoplesoft03
Enter value for domain_dir: /u01/app/oracle/product/psfthcm-midtierlinux-3/ps_cfg_home/webserv/WEBSERVER/peoplesoft03
Enter value for host_name: psfthcm-midtierlinux-3
Enter value for http_port: 9000
Enter value for https_port: 9001
old 2: ('&unique_agent_id','-1','WEBRESOURCE','&DOMAIN_NAME','02','&DOMAIN_DIR','Y','&host_name:&http_port:&https_port','1','1','N')
new 2: ('19','-1','WEBRESOURCE','peoplesoft03','02','/u01/app/oracle/product/psfthcm-midtierlinux-3/ps_cfg_home/webserv/WEBSERVER/peoplesoft03','Y','psfthcm-midtierlinux-3:9000:9001','1','1','N')
1 row created.Enable Search Engine discovery in PeopleSoft
Search Engine discovery is optional, and supports both Elasticsearch and OpenSearch. If Search Engine is already integrated then you can include it in the initial discovery. To integrate Search Engine in the future, use the PeopleSoft CLI refresh command, and add the Search Engine DB grants to the monitoring user. For more information regarding grants, see DB Grant Privileges for PeopleSoft Monitoring, and for more information regarding CLI refresh commands, see PeopleSoft Refresh.
Regardless where agent is present(local/remote), truststore needs to be created using the Java version used by agent. Agent Java version/path can be found from agent_inst/config/emd.properties.
Example:
grep JAVA_HOME emd.properties
JAVA_HOME=/var/lib/oracle-cloud-agent/plugins/oci-managementagent/polaris/jdk1.8.0_371-b11These prerequisites enable Search Engine Integration in PeopleSoft:
- Stack Monitoring only supports monitoring Search Engine configured with SSL. Its endpoint must be HTTPS. For more information on the setup, see Configuring SSL for Elasticsearch or Configuring SSL for OpenSearch, respectively.
-
Before discovering Search Engine, create a JKS truststore, as JKS is the only supported type of trust stores, on the monitoring agent host to store the certificate from Search Engine. This truststore's location and password are required parameters in the discovery UI or in the discovery JSON while performing discovery via CLI, while the trust store location has to be accessible on the agent host.
Example:
keytool -keystore truststore.jks -alias <ALIAS> -import -file <SEARCH ENGINE CERTIFICATE>
Enable Process Monitor discovery for PeopleSoft
- Process Monitor is discovered alongside PeopleSoft, and is enabled by default when discovering a PeopleSoft Application. Selecting No under the Discover Process Monitor section will not include Process Monitor in the PeopleSoft discovery.
- Process Monitor discovery is optional. If Process Monitor is enabled already then you can include it in the initial discovery. To integrate Process Monitor in the future, use the PeopleSoft CLI
refreshcommand, and add the Process Monitor DB grants to the monitoring user. For more information regarding grants, see DB Grant Privileges for PeopleSoft Monitoring, and for more information regarding CLI refresh commands, see PeopleSoft Refresh. -
There are no properties required for Process Monitor discovery
-
User-Interface
- Process Monitor discovery is included by default. To opt out, select No under Discover Process Monitor in the Resource discovery panel.
PeopleSoft Discovery Input
| Input field | Description |
|---|---|
| Resource Name | Name of the PeopleSoft application |
| Management Agent | The Management Agent that will monitor the PeopleSoft Application |
| Process Monitor | |
|
Yes / No |
| PeopleSoft Database | . |
|
Host (FQDN) on which the database is installed |
|
Port used by the database for database connections |
|
Service name of the database used for database connections |
|
Protocol used for the Oracle Database. Select either TCP or TCPS protocol. |
|
Select the secret that contains the database user password from the drop-down list. This field is only displayed if TCPS is selected in the Protocol field. |
| Database Credentials | . |
|
Database user who has the necessary privileges on the underlying PeopleSoft views (e.g. SYSADM, EMDBO) |
|
Database user password |
|
Role of the database user (NORMAL or SYSDBA) |
| Application Server Domain Credentials | . |
|
Remote administration userID |
|
Remote Administration Password (Unencrypted) |
| Process Scheduler Domain Credentials | . |
|
Remote administration userID |
|
Remote Administration Password (Unencrypted) |
| PIA / WebLogic Credentials | . |
|
PIA/Username of the WebLogic monitoring user. For example, the username you would use to log into the WebLogic Console. |
|
PIA/Password of the WebLogic monitoring user' |
| PeopleSoft Search Engine | . |
|
User to access Search Engine endpoint |
|
Search Engine endpoint password |
|
Location of the trust store containing the certificate |
|
Trust store containing the certificate password |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Apache Tomcat
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
- Enable JMX monitoring. See Enabling JMX
Remote.
Note
Tomcat monitoring does not support SSL. SSL will be disabled by default when following Tomcat documentation.
Apache Tomcat Discovery Input
| Input Field | Description |
|---|---|
| Resource Name | Name of the Apache Tomcat resource. |
| Server Host | Host on which the Apache Tomcat is installed. |
| JMX Port | The port used for JMX monitoring. |
| Management Agent | Management Agent monitoring the host where Apache Tomcat is installed. |
| Authorization | Authorization mode for JMX monitoring (Enabled or Disabled). If Enabled is selected, Username and Password are required. |
| Username | JMX monitoring username. |
| Password | JMX monitoring password. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
For more information regarding input parameters, see JSON Input Parameters
Microsoft SQL Server
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
Database connection using SSL encryption is not supported.
Create a Custom Database User
To enable monitoring for a Microsoft SQL Server Database, you can create a special database user as follows.
Create a user (for example, monstk) and map the new user to the master and msdb databases. Then, give this user the following minimum privileges.
CREATE LOGIN monstk
WITH PASSWORD = 'monstk1;123';
GO
CREATE USER monstk FOR LOGIN monstk;
GOMap the user to all system and user databases:
USE master;
CREATE USER monstk FOR LOGIN monstk;
GRANT VIEW ANY DATABASE TO monstk;
GRANT VIEW ANY definition TO monstk;
GRANT VIEW server STATE TO monstk;
GRANT EXECUTE ON sp_helplogins TO monstk;
GRANT EXECUTE ON sp_readErrorLog TO monstk;
GRANT EXECUTE ON dbo.xp_regread TO monstk;
GRANT CREATE FUNCTION TO [monstk];
GRANT CONTROL TO [monstk];
GRANT CREATE TABLE TO [monstk];
GRANT SELECT ON [sys].[sysaltfiles] TO [monstk];
USE msdb;
GRANT SELECT ON dbo.sysjobsteps TO monstk;
GRANT SELECT ON dbo.sysjobs TO monstk;
GRANT SELECT ON dbo.sysjobhistory TO monstk;MS SQL Server Discovery Input
| Input Field | Description |
|---|---|
| Resource Name | Name of the MS SQL Server resource. |
| SQL Server DNS Name | Domain Name System (DNS) for the database. |
| SQL Server Network Port | The database port used for client connections. |
| Management Agent | The Management Agent responsible for monitoring the SQL Server. |
| Username | Username of the database monitoring user. |
| Password | Password of the database monitoring user. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Managed File Transfer (MFT)
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
WebLogic needs to be discovered prior to discovering Managed File Transfer (MFT). When discovering MFT, on the discovery UI, select the corresponding WebLogic from the drop down list.
Database Monitoring Requirements for Stack Monitoring
The Oracle database should be discovered before discovering the MFT application. If the database is discovered first, it will be automatically associated with the MFT application once the MFT application discovery completes. If the MFT application discovery is performed before the database has been discovered, the association will need to be created manually. See Updating Application Topology for more information.
Monitoring a Managed File Transfer application requires specific privileges to access the MFT schema. Stack Monitoring supports the use of the MFT schema owner, typically DEV_MFT, as the database credentials when discovering MFT. It is preferred to create a monitoring user with only the privileges necessary to monitor a MFT application. You can use the same database user to monitor both the Oracle database containing the MFT schema and the MFT application. Steps to create a database monitoring user can be found in MOS Note: 2857604.1.
The specific privileges are defined in the code below. It assumes the MFT schema name of DEV_MFT. If the schema name is different in your setup, then replace DEV_MFT with the actual schema name in the following code. Replace <user> with the database monitoring user created using the script. Ensure the grants are applied to the monitoring user created where the DEV_MFT schema resides.
Database permissions:
GRANT SELECT ON DEV_MFT.MV_MFT_SOURCE_MESSAGE TO <your_monitoring_user>;
GRANT SELECT ON DEV_MFT.MV_MFT_TARGET_INFO TO <your_monitoring_user>;
GRANT SELECT ON DEV_MFT.MV_MFT_TRANSFER_COUNT_INFO TO <your_monitoring_user>;
GRANT SELECT ON DEV_MFT.MV_MFT_SOURCE_INFO TO <your_monitoring_user>;
GRANT SELECT ON DEV_MFT.MV_MFT_TRANSFER TO <your_monitoring_user>;Discovery Input
| Input field | Description |
|---|---|
| Resource Name | Name of the MFT resource. |
|
WebLogic Credentials |
. |
|
Select the WebLogic Domain |
|
Protocol used for the WebLogic Server. The possible values are t3 and t3s. If you select t3s, TrustStore Path and TrustStore Type fields appear under WebLogic User for Monitoring. |
|
WebLogic Server username.
|
|
WebLogic Server user password. |
| Database Credential | |
|
Name of the host where the WebLogic Administration Server is installed. |
|
Port used for WebLogic Administration Server (Console). |
|
Server name of the database used for database connections. |
|
Username of the Oracle Database monitoring credentials |
|
Password of the Oracle Database monitoring credentials |
|
Role of the database user (NORMAL or SYSDBA) |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Oracle HTTP Server (OHS)
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
Collocated OHS
Collocated OHS Discovery is part of Weblogic Domain Discovery and all of its prerequisites apply.
Oracle HTTP Server must be installed in an existing Oracle home, collocated with a WebLogic Server domain.
For more information about installing collocated OHS, see About the Oracle HTTP Server Installation.
Standalone OHS
Supported versions:
-
version 11.x - local monitoring only, Linux host, OPMN tool used for metric collection.
-
version 12.x - local monitoring only, Linux host, WLST tool used for metric collection
Prerequisites:
-
The Management Agent should be installed on the same host as the standalone Oracle HTTP Server.
-
The OHS configuration file (httpd.conf) should be accessible and readable by the Management Agent install user (
mgmt_agentfor standalone agent andoracle-cloud-agentfor Oracle Cloud Agent).
OHS version 11.x:
Version 11.x OHS collects metrics using the OPMN tool.
-
If the agent user and the installation user are the same user:
The OPMN tool should be executable and readable by the Management Agent install user (
mgmt_agentfor standalone agent andoracle-cloud-agentfor Oracle Cloud Agent). -
If the agent user is different from the installation user:
Optional credentials for the installation user (owner user) must be provided during discovery. The installation user must have access to read and execute the OPMN tool. Root user can't be used.
OHS version 12.x:
- Read permissions for the Agent user on
httpd.conffile at:<PATH>/user_projects/domains/<domain_name>/config/fmwconfig/components/OHS/<COMP_NAME>/httpd.confExample :
<PATH>/user_projects/domains/ohs_domain/config/fmwconfig/components/OHS/ohs1Execute the following command to provide read access:
sudo chmod 640 <PATH>/user_projects/domains/<domain_name>/config/fmwconfig/components/OHS/<COMP_NAME>/httpd.conf - Read permissions for the Agent user on OHS Java keystore file at:
<ORACLE HOME DIRECTORY>/wlserver/server/lib/DemoTrust.jks( Custom jks file in case the use of Custom certificates)Example:
sudo chmod 640 <absolute path to <Oracle Home directory>/wlserver/server/lib/DemoTrust.jks - Read and Execute permissions on
<ORACLE HOME DIRECTORY>/oracle_common/common/bin/wlst.sh
OHS version 11.x Discovery Input
| Input Field | Description |
|---|---|
| Absolute path to configuration file (httpd.conf) | Absolute path to httpd.conf configuration file for Oracle HTTP Server |
| Absolute path to instance home | Absolute path to instance home directory |
| Component name | component name of the Oracle HTTP Server |
| Hostname | hostname used to connect to Oracle HTTP Server |
| Listen port | port used to connect to Oracle HTTP Server |
| Management agent | Management Agent monitoring the host where Oracle HTTP Server is installed |
| Version | Version of the Oracle HTTP Server |
| *Optionally, the user can specify the installation owner user credentials if the installation owner is a different user than the management agent user. | |
| Installation owner username | Username of a user who is the Oracle HTTP Server installation owner. |
| Installation owner password | Password of a user who is the Oracle HTTP Server installation owner. |
OHS version 12.x Discovery Input
| Input Field | Description |
|---|---|
| Hostname | hostname used to connect to Oracle HTTP Server |
| Listen port | port used to connect to Oracle HTTP Server |
| Absolute path to configuration file (httpd.conf) | Absolute path to httpd.conf configuration file for Oracle HTTP Server |
| Absolute path to oracle home | Absolute path to oracle home directory |
| Component name | component name of the Oracle HTTP Server |
| Management agent | Management Agent monitoring the host where Oracle HTTP Server is installed |
| Version | Version of the Oracle HTTP Server |
| Node manager username | Username for node manager configured with this Oracle HTTP Server |
| Node manager password | Password for node manager configured with this Oracle HTTP Server |
Apache HTTP Server
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
- The Management Agent should be installed on the same host as Apache HTTP Server.
- Enable
mod_statusApache module (https://httpd.apache.org/docs/2.4/mod/mod_status.html). Configure/server-statuslocation directive for the specified Hostname and Port.Example:
http(s)://<hostname>:<port>/server-status - Turn ON the ExtendedStatus directive (https://httpd.apache.org/docs/2.4/mod/core.html#extendedstatus).
- If applicable, provide access control to the configured
/server-statuslocation directive so that HTTP/HTTPS requests can be successfully made from the host on which the Agent is installed. The Agent only supports Basic Authentication with an HTTPS connection if required. For more information regarding configuring additional access control, see Apache Documentation, Authentication and Authorization. -
The Apache binary files should be accessible and executable by the Management Agent install user:
- The Apache
*.conffile(s) , includinghttpd.conffile, should be accessible and readable by the Management Agent install user (mgmt_agentfor standalone agent andoracle-cloud-agentfor Oracle Cloud Agent). - The Apache binary file (
httpd) should be accessible and executable by the Management Agent install user (mgmt_agentfor standalone agent andoracle-cloud-agentfor Oracle Cloud Agent). - The Apache
pidfile (httpd.pid) should be accessible and readable by the Management Agent install user (mgmt_agentfor standalone agent andoracle-cloud-agentfor Oracle Cloud Agent)..
- The Apache
Here is an example of how to add all the required permissions for the management agent user by creating a dedicated apache administrator user group and adding the management agent user to it:
#Create a user group for apache administration
groupadd apache_admin_grp
#Add management agent user to the apache admin group
#for user installed management agent
usermod -G apache_admin_grp mgmt_agent
#for oracle cloud agent plugin
usermod -G apache_admin_grp oracle-cloud-agent
#Change ownership for apache server root directory and binary file. Example:
chown -R root:apache_admin_grp /etc/httpd
chmod -R 770 /etc/httpd
chown -R root:apache_admin_grp /usr/sbin/httpd
chmod -R 770 /usr/sbin/httpd
#Grant access to httpd.pid file. Example:
chown -R root:apache_admin_grp /run/httpd
#Restart the Agent for the user group assignment to take effect.
#for user installed management agent
systemctl restart mgmt_agent
#for oracle cloud agent plugin
systemctl restart oracle-cloud-agentApache HTTP Server Discovery Input
| Input Field | Description |
|---|---|
| Resource Name | Name of the Apache HTTP Server resource. |
| Server Host | Host where the Apache HTTP Server is installed. |
| Listen Port | Listen port of the Apache HTTP Server. |
| Absolute Path of httpd.conf | The absolute path to the Apache httpd.conf file. |
| Absolute Path of httpd binary | The absolute path to the httpd binary file. |
| Management Agent | Management Agent that monitors the host on which the Apache HTTP Server is installed. |
| Protocol | Protocol used to connect to the Apache HTTP server. |
| Discovery parameter name | *Optionally, the user can specify basic authentication credentials when configuring the HTTPS connection |
| Username | Username to access server-status metrics with basic authentication. |
| Password | Password to access server-status metrics with basic authentication. |
| Discovery parameter name | *Required when using HTTPS |
| Truststore path | Absolute path of the JKS trust store containing the certificate. |
| Truststore password | Trust store password. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Oracle Unified Directory
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
Monitoring OUD resources prerequisites and workflow:
-
Deploy management agent on the host where OUD is running/configured
-
Prerequisite steps to copy the necessary files
-
Setup OUD exporter to collect metrics in Prometheus format
-
Wait for 20 minutes for metrics to start getting collected
-
Import OUD as a resource into stack monitoring
-
Monitor OUD using Stack Monitoring
OUD exporter does not support the Oracle Cloud Agent.
OUD can function in one of the following three modes:
-
As an LDAP directory server instance, used to contain data
-
As an LDAP proxy server instance, where the server acts as an interface between the client and the directory server or servers that contain the data
-
As a replication gateway instance between OUD and Oracle Directory Server Enterprise Edition (ODSEE)
The Stack Monitoring monitoring solution for OUD includes three resource types, one for each of the above installation modes or types.
Setup Exporter
The exporter will collect metrics from OUD and create an endpoint to expose the metrics in Prometheus format. These metrics will then be uploaded by the management agent to telemetry datastore to the <specified name space>.
The exporter needs to be setup for each instance of each installation mode. For example, if there are 3 directories and 2 proxies, the exporter will have to be setup 5 times.
Setup steps overview:
- Ensure Python is installed and also install python-ldap
- Add OUD user's runtime group to the
mgmt_agentuser - Copy the exporter script to a custom location
- Create temporary password files for the OUD exporter
- Create a monitoring user for the OUD instance
- Give filesystem grants to the OUD database to monitor the database sizes
- Setup OUD exporter
- Enable OUD exporter to start after an OS reboot
- Confirm metrics are flowing
Setup steps:
-
Ensure Python is installed and also install python-ldap:
- On RedHat/Oracle Linux 8 and 9:
sudo -n yum install -y libnsl python3-ldap httpd-tools - On RedHat/Oracle Linux 7:
sudo -n yum install -y libnsl python-ldap httpd-tools
- On RedHat/Oracle Linux 8 and 9:
-
Make sure
mgmt_agenthas the right permissions:- Add OUD user's runtime group to the mgmt_agent user:
sudo usermod -G <OUD_USER_GROUP> mgmt_agent - Make sure the
<ORACLE_HOME>directory and it's parent directories have execution permissions:sudo chmod -R 0750 <ORACLE_HOME_PATH>
- Add OUD user's runtime group to the mgmt_agent user:
-
Copy the exporter script to a custom location:
- Create a custom directory from where the OUD exporter will be executed..
- Change the ownership of the new directory, and give read and execute access to the
mgmt_agentuser to this new directory and all the contents in it:sudo chown -R mgmt_agent:mgmt_agent <CUSTOM_EXPORTER_DIRECTORY_PATH>Example:
sudo chown -R mgmt_agent:mgmt_agent /scratch/exporter/oud_exporter - As the management agent user, copy the
manage_exporter.shscript from$AGENT_INST/config/destinations/OCI/services/appmgmt/<Latest_Version>/scripts/oudto the custom directory.
-
Create temporary password files for the OUD exporter:
- For the root directory user, such as
cn=Directory Manager:echo <PASSWORD> | sudo -u mgmt_agent tee <FULL_PATH_OF_THE_DIRECTORY_MANAGER_USER_PASSWORD_FILE>/.pwExample:
echo <password> | sudo -u mgmt_agent tee /scratch/exporter/oud_exporter/.pw - For the monitoring user:
echo <PASSWORD> | sudo -u mgmt_agent tee <FULL_PATH_OF_THE_MONITORING_USER_PASSWORD_FILE>/.mpwExample:
echo <password> | sudo -u mgmt_agent tee /scratch/exporter/oud_exporter/.mpw
- For the root directory user, such as
-
Create a monitoring user for the OUD instance:
- As the
mgmt_agentuser, run:./manage_exporter.sh adduser --port <ADMINISTRATION_PORT_OF_THE_OUD_INSTANCE> --utype admin --dstype oud -j <FULL_PATH_OF_THE_DIRECTORY_MANAGER_USER_PASSWORD_FILE> --mpw <FULL_PATH_OF_THE_MONITORING_USER_PASSWORD_FILE> --javaHome <JAVA_HOME_PATH>Example:
./manage_exporter.sh adduser --port 4444 --utype admin --dstype oud -j /scratch/exporter/oud_exporter/.pw --mpw /scratch/exporter/oud_exporter/.mpw --javaHome /scratch/install/jdk1.8.0_381/ - By default, the name of the Monitoring User is
muser. It can be changed with--muser <name>
- As the
-
Give filesystem grants to the OUD database to monitor the database sizes:
sudo getfacl "<OUD_HOME_DIRECTORY_PATH>/OUD/db"Example:
sudo getfacl "/scratch/oud12c/oud_instance/OUD/db"sudo setfacl -R -m "u:mgmt_agent:rx" "<OUD_HOME_DIRECTORY_PATH>/OUD/db"Example:
sudo setfacl -R -m "u:mgmt_agent:rx" "/scratch/oud12c/oud_instance/OUD/db"
-
Setup OUD exporter:
- As the mgmt_agent user, run the setup command:
./manage_exporter.sh setup --type <PRODUCT_TYPE> --compartment <COMPARTMENT_ID> --name <RESOURCE_NAME> --instName <RESOURCE_NAME> --ldap <LDAP_PORT> --ldaps <LDAPS_PORT> --oracleHome <ORACLE_HOME_PATH> --adminPort <ADMINISTRATION_PORT_OF_THE_OUD_INSTANCE> --metricPort <METRICS_MONITORING_ENDPOINT_PORT> --javaHome <JAVA_HOME_PATH> -D <NAME_OF_THE_MONITORING USER> -j <FULL_PATH_OF_THE_DIRECTORY_MANAGER_USER_PASSWORD_FILE>Example:
./manage_exporter.sh setup --type oud --compartment ocid.compartment1.abcdef1234 --name oud_one --instName oud_one --ldap 0 --ldaps 0 --oracleHome /scratch/oud12c --adminPort 4444 --metricPort 1888 --javaHome /scratch/install/jdk1.8.0_381/ -D muser -j /scratch/exporter/oud_exporter/.pw - Restart management agent:
sudo systemctl restart mgmt_agent - For more options during setup, run the help command:
./manage_exporter.sh help
OUD metrics will be collected in Prometheus format at the Promethus end point, and the management agent will also be uploading the metrics to telemetry.
- As the mgmt_agent user, run the setup command:
-
Enable OUD exporter to start after an OS reboot. This will also allow the
mgmt_agentuser to restart the Management Agent and the Exporter services:sudo ./manage_exporter.sh enable -
Confirm metrics are flowing:
-
To ensure the exporter is collecting OUD metrics properly, call the metric endpoint in the host where the exporter is running. There should be at least 40 metrics:
- On a browser:
https://localhost:<METRICS_MONITORING_ENDPOINT_PORT>/metrics - node_exportercredentials must be provided.Example:
https://localhost:1888/metrics - On terminal:
curl -u "<NODE_EXPORTER_USER>:<NODE_EXPORTER_PASSWORD>" -sk https://127.0.0.1:1888/metrics
- On a browser:
- To ensure the Management Agent is uploading metrics to Telemetry, after 5 minutes since the Exporter started, open the Metrics Explorer in OCI. Select your compartment,
oracle_appmgmtmetric namespace and any of the oud resource groups. Select any metric and verify it is reporting properly.
-
Setup exporter command options:
| Option | Description |
|---|---|
| type | Type of OUD that is being configured: oud, proxy or replgw. |
| compartment | Compartment Id. |
| name | Name that will be given to the monitored resource |
| instName | Name that will be given to the OUD instance (Required if monitoring the database size) |
| ldap | Non-encrypted LDAP port. Default: 1389. Can be set to 0 not monitor that port. |
| ldaps | Encrypted LDAP port. Default: 1888. Can be set to 0 not monitor that port. |
| oracleHome | Oracle Home of the OUD application. |
| adminPort | Administration port of the OUD instance. |
| metricPort | New port to be used to expose metrics in Prometheus format. This port must be available prior setup. |
| D | Monitoring user without "cn=" prefix. |
| j | Path to the the Monitoring user password file |
| proxiuri | If behind a proxy, provide the proxy URI including the port, such as http://localhost:80 |
| Add monitoring user command option | Description |
|---|---|
| port | Administration port of the OUD instances |
| j | Path to the Directoy Manager user password file |
| mpw | Path to the Monitoring user password file |
| muser | Name of the monitoring user. Default value is muser |
OUD Statuses
OUD supports 4 different statuses depending on several factors, which are described below:
- Up
OUD is Up when all the system and metrics are flowing normally.
- Down
OUD is Down when the BindDN is missing, there is a connection issue with the LDAP server or the LDAP server is down.
- Maintenance
Users can put OUD under Maintenance at any point to perform maintenance on the instances or any other purpose.
- Warning
The OUD instance has failed at least one service test and therefore should be investigated.
Managing OUD status
To configure an OUD instance to be under Maintenance or Up, run:
./manage_exporter.sh modstate <STATUS> --port <ADMINISTRATION_PORT_OF_THE_OUD_INSTANCE> --dstype oud -j <FULL_PATH_OF_THE_DIRECTORY_MANAGER_USER_PASSWORD_FILE>| Command option | Description |
|---|---|
| STATUS | UP or MAINT. UP will configure the OUD instance in normal mode and MAINT will put the OUD instance in Maintenance mode.
|
To see the current state of OUD, run:
./manage_exporter.sh showstate --port <ADMINISTRATION_PORT_OF_THE_OUD_INSTANCE> --dstype oud -j <FULL_PATH_OF_THE_DIRECTORY_MANAGER_USER_PASSWORD_FILE>| Command option | Description |
|---|---|
| port | Administration port of the OUD instances |
| j | Path to the Directory Manager user password file |
Import OUD
OUD can be independently imported and monitored as one of the following resource types:
- OUD Directory Server
- OUD Proxy Server
- OUD Replication Gateway
To import OUD to Stack Monitoring, ensure the Management Agent has been uploading OUD metrics to telemetry for at least 20 minutes.
Import OUD resource types with the following command:
oci stack-monitoring resource-task import-telemetry-resources --compartment-id <compartment id> --namespace oracle_appmgmt --source OCI_TELEMETRY_PROMETHEUS --resource-group <resource group>Import each resource type, not each instance. For example, if there are 3 directories and 2 proxies, run the import command 2 times, once for each type.
After the resources are imported, if a new OUD instance is added, execute the import command again for the newly added resource type.
| Option | Description |
|---|---|
| compartment-id | Compartment Id |
| namespace | Namespace where the metrics are stored: oracle_appmgmt |
| source | Source to post metrics: OCI_TELEMETRY_PROMETHEUS |
| resource-group | OUD resource type to be imported: oud_directory, oud_proxy or oud_gateway |
For more information regarding deleting Stack Monitoring resources, see Deleting Resources.
For more information regarding other OUD operations, see Oracle Unified Directory Operations in the Application Topology chapter.
For more information regarding troubleshooting OUD, see Troubleshoot OUD.
Oracle GoldenGate
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
Oracle GoldenGate REST APIs must be accessible from the Management Agent which will monitor the GoldenGate instance.
Only https protocol is supported, so the GoldenGate instance must be configured with required certificates.
Management Agent must have access to the Truststore JKS file which contains the certificate to validate TLS connection.
GoldenGate Discovery Input
| Input Field | Description |
|---|---|
| Resource Name | Name of the Oracle GoldenGate resource |
| Host Name | FQDN of host where Oracle GoldenGate is installed. |
| Service Manager Port | Listen port of Oracle GoldenGate Service Manager. |
| Management Agent | Management Agent that monitors Oracle GoldenGate |
| Username | Username to access Oracle GoldenGate REST URLs with basic authentication |
| Password | Password to access Oracle GoldenGate REST URLs with basic authentication. |
| Truststore path | Absolute path of the JKS trust store containing the certificate |
| Truststore password | Trust store password |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Microsoft Internet Information Services (IIS)
The successful discovery of a Microsoft IIS resources will discover the resource named during discovery and all its children sites. The children sites will have the parent resource given name as prefix.
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
The Management Agent monitoring IIS must be deployed locally on the host where IIS is running, and the necessary prerequisites completed. For more information, see Perform Prerequisites for Deploying Management Agents.
Microsoft IIS and Local Agent are running during discovery.
Microsoft IIS Discovery Input
| Resource Type | Microsoft Internet Information Services |
| Resource Name | Name of the Resource. It should be Unique. |
| Management Agent | Local Agent running on above host |
| License | Select the option |
| Host Name | Name of Host where MS-IIS is running |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags (under Show advanced options) |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
Oracle JVM Runtime
Prerequisites
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
- JMX monitoring has to be enabled. To enable JMX monitoring, see Enabling JMX Remote.
It is recommended the Management Agent be locally installed where the JVM is running.
Oracle JVM Runtime Discovery Input
| Input Field | Description |
|---|---|
| Resource Type | Oracle JVM Runtime |
| Resource Name | Name of the JVM resource. |
| Host Name | Host on which JVM is running |
| Java Management Port | The port used for JMX monitoring. |
| Management Agent | Management Agent from which JMX Connection can be made to JVM |
| Authorization | Authorization mode for JMX monitoring (Enabled or Disabled). If Enabled is selected, Username and Password are displayed. |
| Username | JMX monitoring username. |
| Password | JMX monitoring password. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |
NGINX
To discover any resource type, other than complying with prerequisites, an active Management Agent is required for discovery. Refer to Install Management Agents for on premise installation and to Deploy Management Agents on Compute Instances for OCI instances deployment.
Non-SSL is not supported.
NGINX Discovery Input
| Input Field | Description |
|---|---|
| Resource Name | Name of the resource. |
| NGINX Host | Host on which NGINX is running |
| Listen Port | Port on which NGINX is listening |
| URL to check NGINX status | URL which will be used to check NGINX status |
| Management Agent | Management Agent monitoring the host where NGINX is installed. |
| NGINX credentials | |
| Username | NGINX monitoring Username |
| Password | NGINX monitoring Password |
| TrustStore path | Absolute path of the JKS trust store containing the certificate. |
| TrustStore password | Trust store password. |
| Discover In | |
| Stack Monitoring and Log Analytics (recommended) | Discovery results will be sent to Stack Monitoring and Log Analytics. NoteFor information on Log Analytics, see Quick Start. |
| Stack Monitoring only | Discovery results will be sent to Stack Monitoring only. |
| Log Analytics only | Discovery results will be sent to Log Analytics only. |
| License | |
| Enterprise Edition | The resource will be assigned an Enterprise Edition license. |
| Standard Edition | The resource will be assigned an Standard Edition license. |
| Tags |
Freeform and Defined Tags can be applied to Stack Monitoring resources during discovery. To use Defined Tags first create the Tag namespaces, refer to . Refer to Tags and Tag Namespace Concepts for details on creating and managing the Tag namespaces for Defined Tags. When discovering a resource, any tag assigned will be applied to all the discovered resources. For more information regarding Tag prerequisites and Tag propagation, see Managing Tags. |
|
Tag Namespace |
Select "None" to add a free-form tag. Select a namespace to add a defined tag in the namespace. If you have permissions to create a resource, then you also have permissions to apply free-form tags to that resource. To apply a defined tag, you must have permissions to use the tag namespace. For more information about tagging, see Resource Tags. If you are not sure whether to apply tags, skip this option (you can apply tags later) or ask your administrator. |
|
Tag Key |
Specify the name you use to refer to the tag. |
|
Tag Value |
Specify the tag value. For more details on Tag Key and Tag Value, refer Overview of Tagging. |