Integrating Custom Applications with IAM
Learn how to use the SCIM interface to integrate custom applications with an identity domain.
Integrating with Custom Applications
Let's say that you want to integrate your applications with an identity domain. Your applications are homegrown or aren't listed in the App Catalog, and an AD Bridge or Provisioning Bridge can't be used as a link between your applications and an identity domain, but they do support the SCIM standard.
By integrating your custom applications which support the SCIM standard with an identity domain, you can provide provisioning capabilities for your applications, and synchronize your users between the applications and IAM.
SCIM
In the past, it was common that applications used to have their own user management APIs. Because the APIs for each application behave in a certain way, the developer had to understand the APIs specific to each application to build integrations for the applications.
To integrate your custom applications with identity domains, Oracle recommends that you use the System for Cross-domain Identity Management (SCIM). SCIM provides developers with an abstraction layer. If APIs for the applications are exposed through SCIM, then developers don't have to learn the APIs associated with each application because the JSON format of the APIs is common across all applications.
In addition to SCIM being an open specification that standardizes user and group management across applications, it allows for the automation of user and group provisioning. You can provision and synchronize data for your users and groups across multiple applications.
With SCIM, you can define HTTP endpoints to create, read, update, and delete resources for entities such as users and groups. You can also use SCIM to extend the schemas for your company's users and groups. The SCIM specification defines a minimum set of attributes for the user schema, but this schema can be extended.
For example, suppose you need to provision the Employee ID custom
attribute from the identity domain user schema to your custom application. You can
extend the default user schema, add this attribute, and map it between the identify
domain and your application. The user schema in the identity domain can now adhere to
the attributes associated with your custom application's identity store.
The SCIM specification also defines security for any request that you make using HTTP endpoints. Security is defined by using a secure (HTTPS) protocol to establish communication between the endpoints and the applications with which you're integrating, and requiring an authorization token that's used to access the request and perform the operations associated with it.
Use the following table to learn more about the SCIM specification:
| Item | URL |
|---|---|
| Core schema | https://tools.ietf.org/html/rfc7643 |
| Protocol | https://tools.ietf.org/html/rfc7644 |
| Definitions, overview, concepts, and requirements | https://tools.ietf.org/html/rfc7642 |
If you look at how integrations used to be built, developers had to understand the APIs exposed for each application. There was no consistency regarding how to represent an identity in these applications.
By using SCIM, there's now a common standard of how you represent an identity in every application. Because all applications comply with the SCIM format, there's a harmonious flow in terms of how these identities are represented. This makes it easier for an identity management cloud service such as IAM to integrate with these applications.
Having a common standard for representing identities in applications improves developers' work efficiency and productivity because developers don't have to spend time to learn the APIs for each application. From a corporate standpoint, the time it takes to develop an integration from an identity system to the application will be reduced significantly. You can now run automations for the integration because there's a standard in terms of how you represent an identity and how you integrate with that identity.
By exposing your custom application's identity store with a SCIM-based interface, you avoid having to develop a custom connector between your application and IAM. This can be time-consuming, costly, and can lead to heavy maintenance in a future upgrade.
SCIM automates the user identity lifecycle management process and increases the security of data associated with your company's users and groups.
As your company grows, your users and groups increase. Through the day-to-day operations of your company, you might experience situations such as employee turnover or the memberships that your users have with your company's groups might change. Your company's user accounts, groups, and group memberships increase significantly.
Because SCIM is a standard, your company's user and group data is stored in a consistent way and can be communicated as such across different apps (including your custom apps). You can automate the provisioning and deprovisioning process and have IAM function as a single point to manage permissions and group memberships. By transferring your company's user and group data automatically, you mitigate the risk of inadvertent errors.
By implementing SCIM, you improve your company's security. Through SSO, your company's employees no longer have to sign in to each of their accounts individually. You can ensure security policy compliance for your users and their access to your company's applications.
Generic SCIM App Templates
The App Catalog contains thousands of applications that integrate with IAM. You might have your applications running on your premises or in the cloud, or you might be building your applications in different infrastructure systems such as Amazon Web Services or Oracle Cloud Infrastructure.
IAM has to provide not only integrations with the applications that are listed in the App Catalog, but also tools so that you can build integrations for your custom applications without developing code.
With the Generic SCIM App Template, you can configure your custom applications so that the SCIM APIs are exposed, and you don't have to develop a single line of code. All that's required is to go to the App Catalog and search for a SCIM-managed app template. To use this template, you only have to provide your endpoint URL and the details that IAM requires to connect to your application. Then map the attributes between your application and an identity domain.
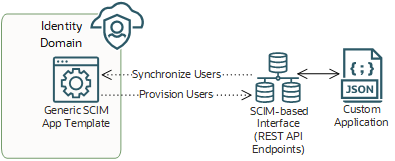
With the Generic SCIM App Template, you can provision or synchronize users between your custom applications and identity domains.
In this diagram, the Generic SCIM App Template has been configured to enable IAM to communicate with a custom application that has a SCIM-based interface. This interface uses REST API endpoints to provision and synchronize users between Identity Domains and the custom application.
Does Your Custom Application Have a SCIM-based Interface?
Learn what to do, based on whether your custom application has a SCIM-based interface.
If your custom application has this interface, then you can configure the Generic SCIM App Template to provision users with your application. See Configure the Generic SCIM App Template.
If your custom application doesn't have this interface, then you can develop a custom SCIM gateway to act as the interface between IAM and your custom application. See How Do You Develop a Custom SCIM Gateway?