Configuring Network Access with Access Control Rules (ACLs)
Specifying an access control list blocks all IP addresses that are not in the ACL list from accessing the database. After you specify an access control list, the Autonomous AI Database only accepts connections from addresses on the access control list and the database rejects all other client connections.
- Configure Access Control Lists When You Provision or Clone an Instance
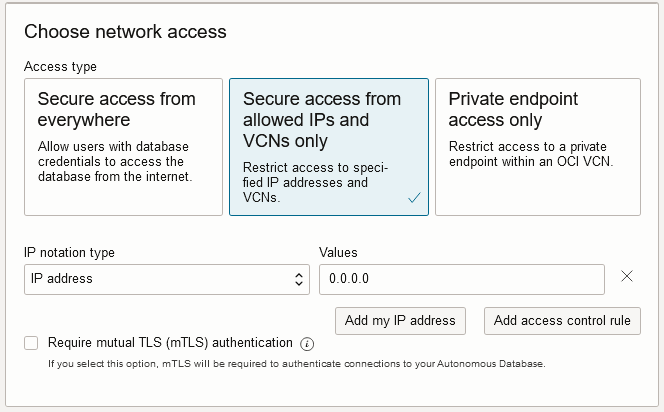
When you provision or clone Autonomous AI Database with the Secure access from allowed IPs and VCNs only option, you can restrict network access by defining Access Control Lists (ACLs). - Configure Access Control Lists for an Existing Autonomous AI Database Instance
You can control and restrict access to your Autonomous AI Database by specifying network access control lists (ACLs). On an existing Autonomous AI Database instance with a public endpoint you can add, change, or remove ACLs. - Change from Private to Public Endpoints with Autonomous AI Database
If your Autonomous AI Database instance is configured to use a private endpoint you can change the configuration to use a public endpoint. - Access Control List Restrictions and Notes
Describes restrictions and notes for access control rules on Autonomous AI Database.
Configure Access Control Lists When You Provision or Clone an Instance
When you provision or clone Autonomous AI Database with the Secure access from allowed IPs and VCNs only option, you can restrict network access by defining Access Control Lists (ACLs).
See Provision an Autonomous AI Database Instance for information on provisioning your Autonomous AI Database.
Configure ACLs as follows:
After provisioning completes, you can update public endpoint ACLs or you can change the Autonomous AI Database configuration to use a private endpoint.
See Configure Access Control Lists for an Existing Autonomous AI Database Instance for information on updating ACLs.
See Change from Public to Private Endpoints with Autonomous AI Database for information on changing to a private endpoint.
Configure Access Control Lists for an Existing Autonomous AI Database Instance
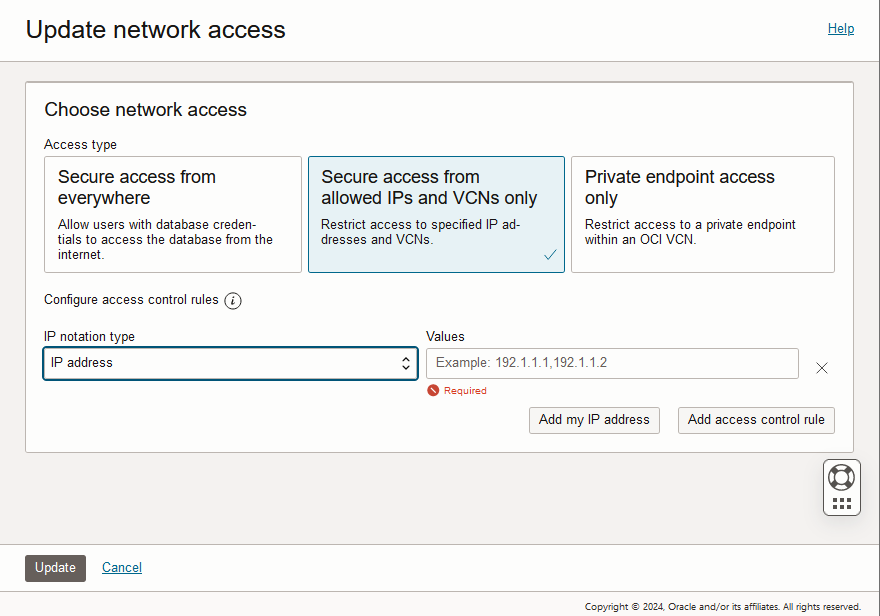
You can control and restrict access to your Autonomous AI Database by specifying network access control lists (ACLs). On an existing Autonomous AI Database instance with a public endpoint you can add, change, or remove ACLs.
Configure ACLs, or add, remove, or update existing ACLs for an Autonomous AI Database instance as follows:
If the Lifecycle state is Available when you click Update the Lifecycle state changes to Updating until the ACL is set. The database is still up and accessible, there is no downtime. When the update is complete the Lifecycle state returns to Available and the network ACLs from the access control list are in effect.
Change from Private to Public Endpoints with Autonomous AI Database
If your Autonomous AI Database instance is configured to use a private endpoint you can change the configuration to use a public endpoint.
-
The Autonomous AI Database instance must be in the available state (Lifecycle state: Available).
-
Before changing the network configuration from a private endpoint to a public endpoint, you must change the configuration to not allow TLS connections. This closes any existing TLS connections. See Update your Autonomous AI Database Instance to Require mTLS and Disallow TLS Authentication for more information.
To specify a public endpoint for your Autonomous AI Database do the following:
The Lifecycle state changes to Updating until the operation completes.
Notes for changing from private endpoint to public endpoint network access:
-
After updating the network access type all database users must obtain a new wallet and use the new wallet to access the database. See Download Client Credentials (Wallets) for more information.
-
After the update completes, you can change or define new access control rules ACLs for the public endpoint. See Configure Access Control Lists for an Existing Autonomous AI Database Instance for more information.
-
The URL for Database Actions and for the Database Tools are different when a database uses a private endpoint compared to using a public endpoint. Click Database Actions on the Oracle Cloud Infrastructure Console to find the updated Database Actions URL and in Database Actions click the appropriate cards to find the updated Database Tools URLs, after changing from a private endpoint to a public endpoint.
Access Control List Restrictions and Notes
Describes restrictions and notes for access control rules on Autonomous AI Database.
-
See IP Address Ranges for information about the public IP address ranges in Oracle Cloud Infrastructure. You must allow traffic to these CIDR blocks to ensure access to an Autonomous AI Database instance on a public endpoint.
-
If you want to only allow connections coming through a service gateway you need to use the IP address of the service gateway in your ACL definition. To do this you need to add an ACL definition with the CIDR source type with the value
240.0.0.0/4. Note that this is not recommended, instead of this you can specify individual VCNs in your ACL definition for the VCNs you want to allow access from.See Access to Oracle Services: Service Gateway for more information.
-
When you restore a database the existing ACLs are not overwritten by the restore.
-
The network ACLs apply to the database connections and Oracle Machine Learning notebooks. If an ACL is defined, if you try to login to Oracle Machine Learning Notebooks from a client whose IP is not specified on the ACL this shows the "login rejected based on access control list set by the administrator" error.
-
The following Autonomous AI Database tools are subject to ACLs. You can use Virtual Cloud Network, Virtual Cloud Network (OCID), IP address, or CIDR block ACLs to control access to these tools:
- Database Actions
- Oracle APEX
- Oracle Graph Studio
- Oracle Machine Learning Notebooks
- Oracle REST Data Services
-
If you have a private subnet in your VCN that is configured to access the public internet through a NAT Gateway, you need to enter the public IP address of the NAT Gateway in your ACL definition. Clients in the private subnet do not have public IP addresses. See NAT Gateway for more information.
-
If you are using ACLs and TLS connections are allowed, you must change your network configuration to not allow TLS connections before removing all ACLs. See Update your Autonomous AI Database Instance to Require mTLS and Disallow TLS Authentication for more information.
-
To view the network information for your instance, see View Network Information on the OCI Console.