Manage Master Encryption Keys in Oracle Key Vault
Autonomous AI Database supports customer-managed Transparent Data Encryption (TDE) keys that reside in Oracle Key Vault (OKV).
- Prerequisites to Use Customer-Managed Encryption Keys in Oracle Key Vault
Describes the prerequisite steps to use customer-managed master encryption keys that reside in Oracle Key Vault (OKV) on Autonomous AI Database. - Use Customer-Managed Encryption Keys on Autonomous AI Database with Oracle Key Vault
Shows the steps to encrypt your Autonomous AI Database using customer-managed master encryption keys that reside in Oracle Key Vault (OKV).
Parent topic: Manage Encryption Keys on Autonomous AI Database
Prerequisites to Use Customer-Managed Encryption Keys in Oracle Key Vault
Describes the prerequisite steps to use customer-managed master encryption keys that reside in Oracle Key Vault (OKV) on Autonomous AI Database.
-
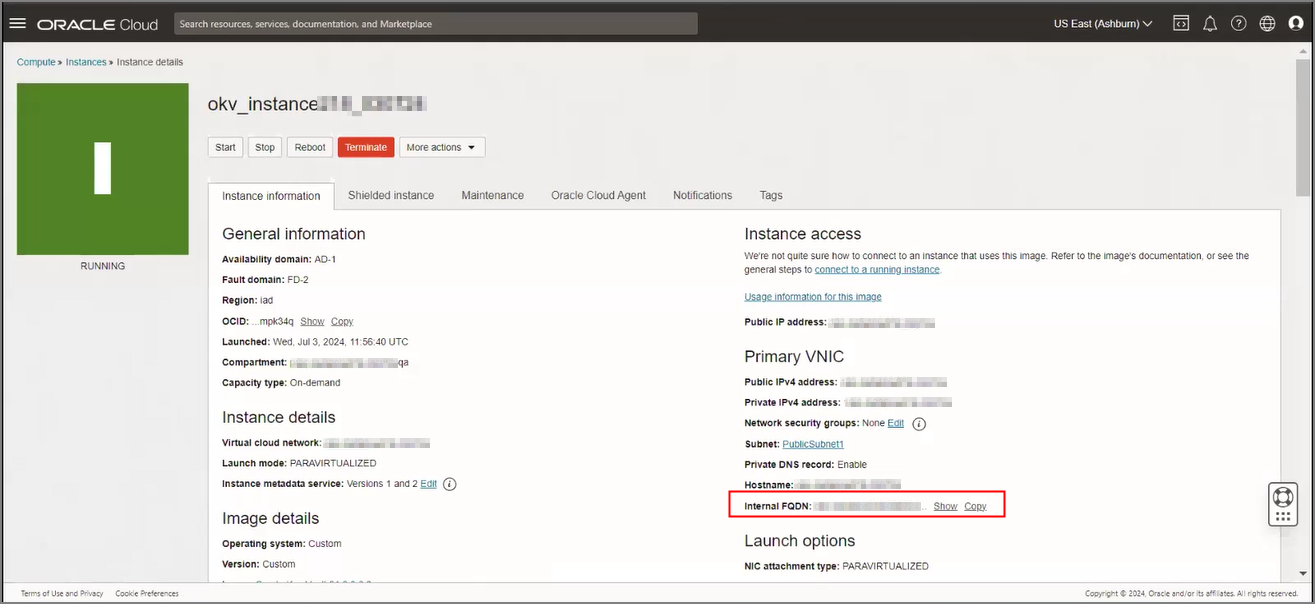
The Autonomous AI Database instance must use private endpoints.
-
Autonomous AI Database supports OKV instances that are in private networks and are accessible from the same network where the Autonomous AI Database resides.
See VCN and Subnet Management and Deploying Oracle Key Vault on an Oracle Cloud Infrastructure VM Compute Instance for more information.
- OKV is not supported in cross-region Autonomous Data Guard standbys.
Follow these steps:
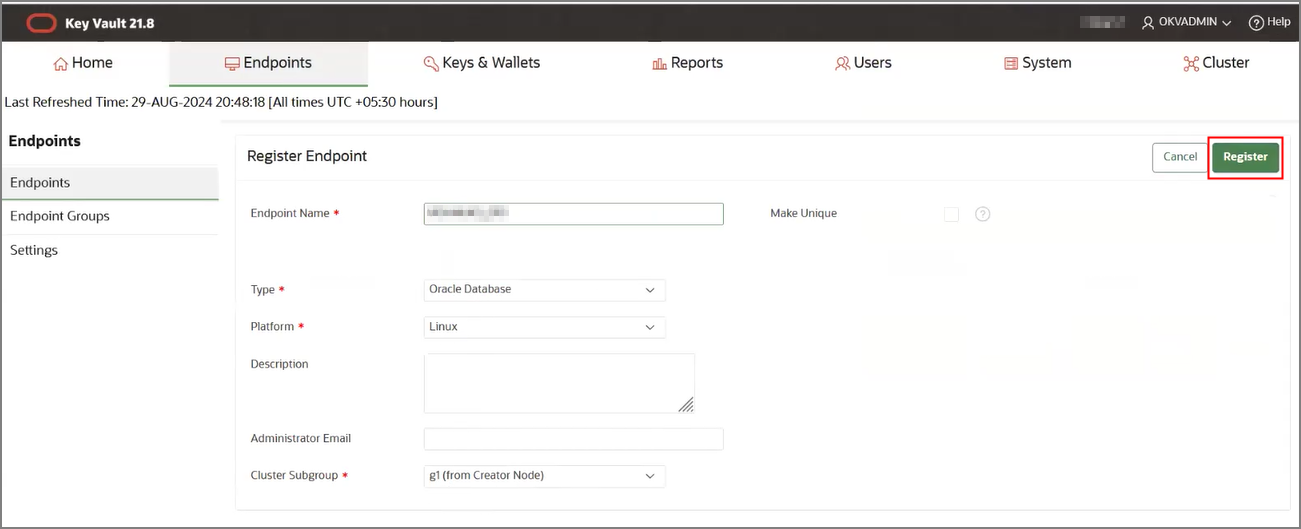
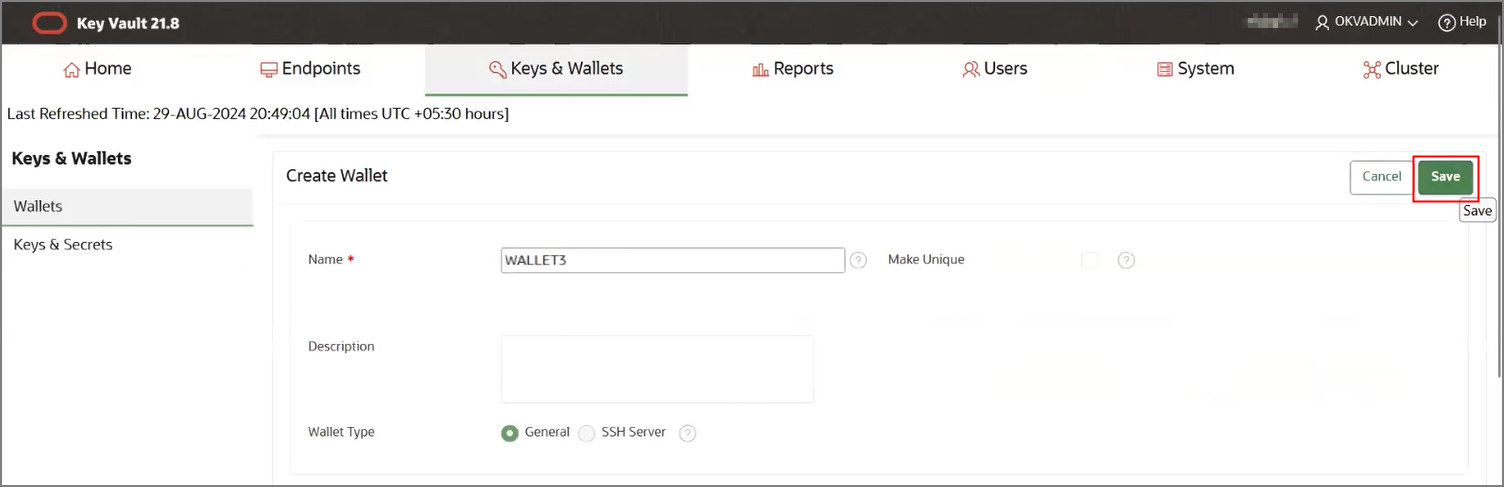
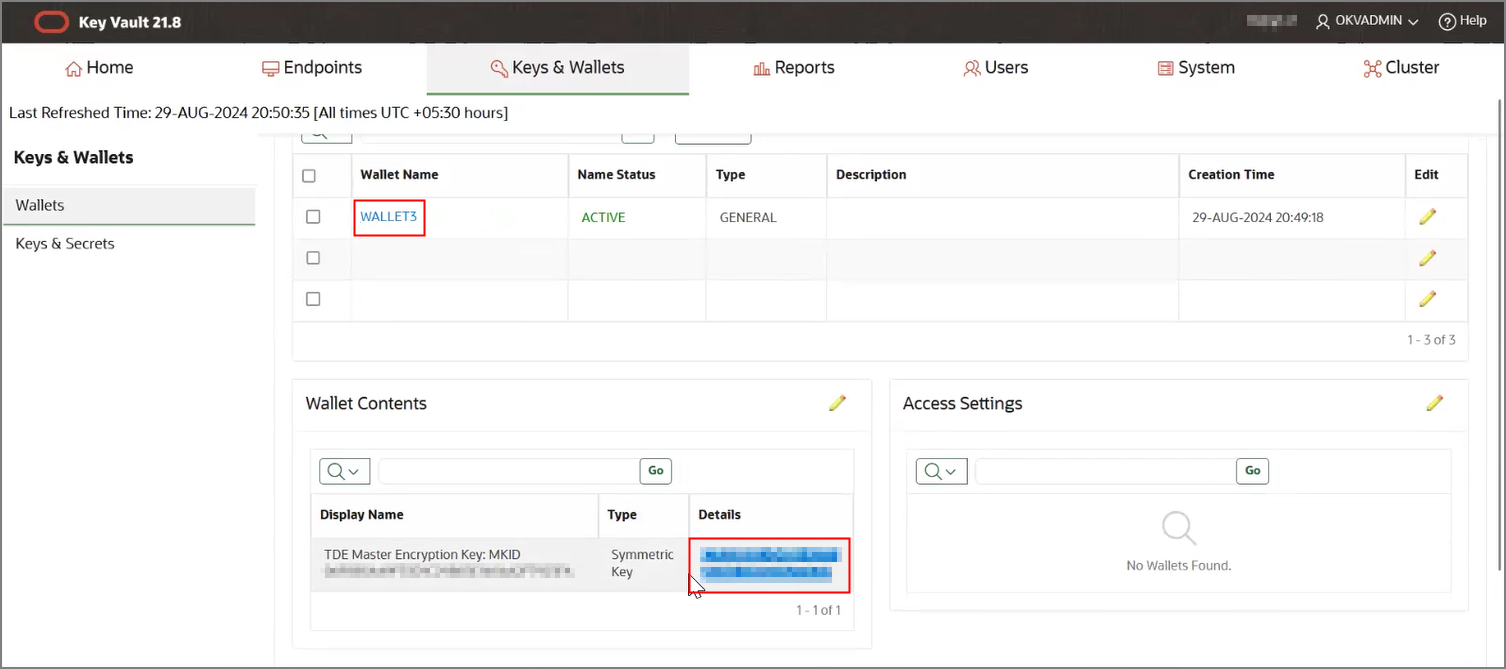
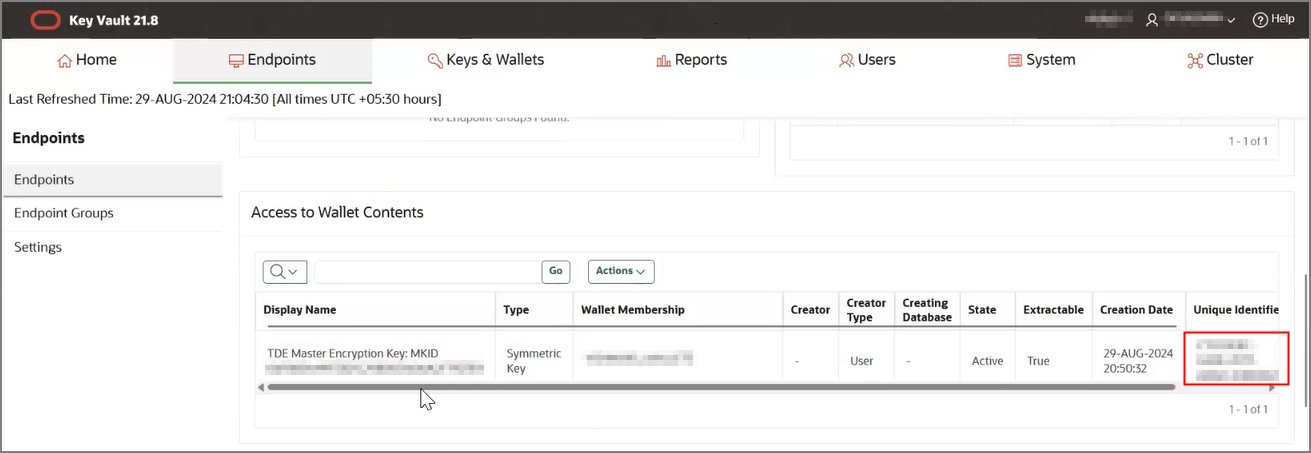
- Create an OKV endpoint, wallet and TDE master key.
- Provision an Autonomous AI Database
instance, with the following required settings:
- For Choose network access, select Private endpoint access only.
- For Virtual cloud network, select the VCN where this database instance is running.
- For Subnet, select the private subnet where this database instance is running.
- For Network security groups (NSGs), select the security group.
- For Encryption key settings, default to Encryption using an Oracle-managed key. These settings are changed to customer managed keys in OKV, after these prerequisite steps are completed. The customer managed keys are disabled during instance provisioning. See Use Customer-Managed Encryption Keys on Autonomous AI Database with Oracle Key Vault for details.
- Connect to the Autonomous AI Database
instance and create a directory for the OKV wallet.
- Download the Endpoint wallet to the directory object created in the Autonomous AI Database instance. This
wallet is not the virtual TDE wallet in OKV that contains the TDE master
encryption key. This wallet contains the necessary certificates to establish an
mTLS 1.2 connection between OKV and Autonomous AI Database.
Parent topic: Manage Master Encryption Keys in Oracle Key Vault
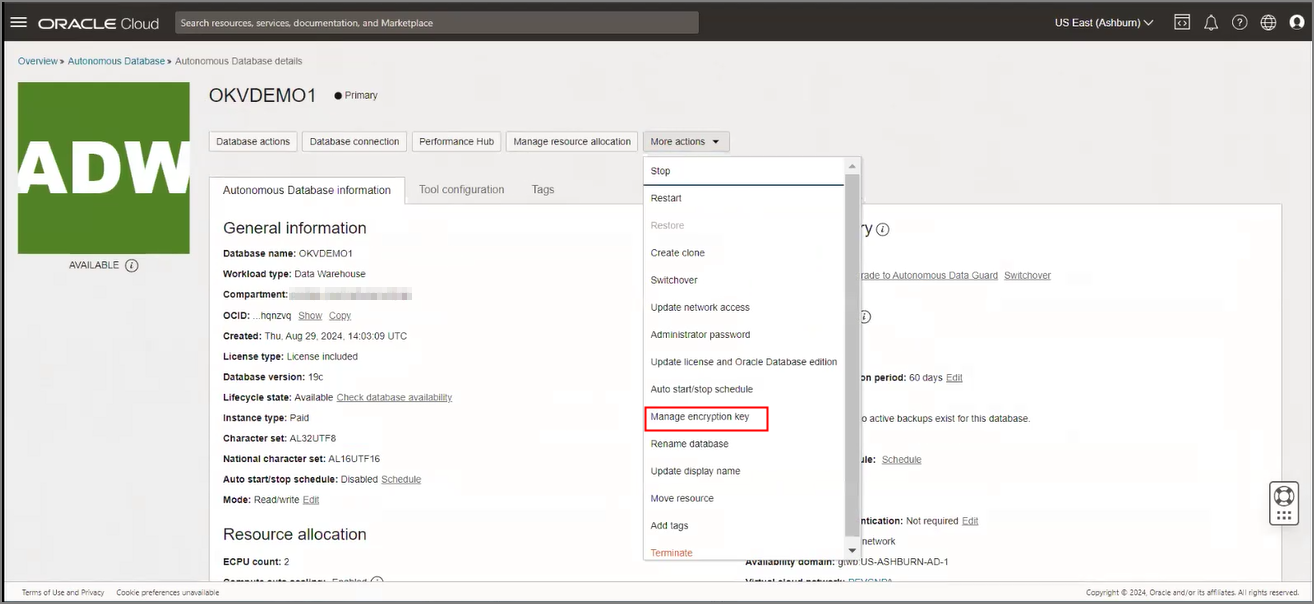
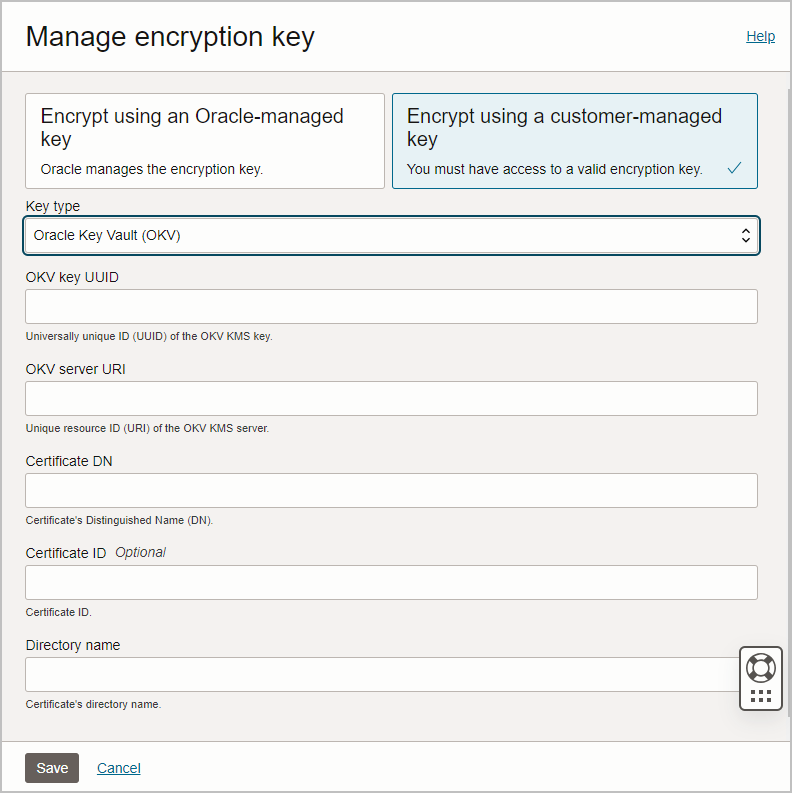
Use Customer-Managed Encryption Keys on Autonomous AI Database with Oracle Key Vault
Shows the steps to encrypt your Autonomous AI Database using customer-managed master encryption keys that reside in Oracle Key Vault (OKV).
Follow these steps:
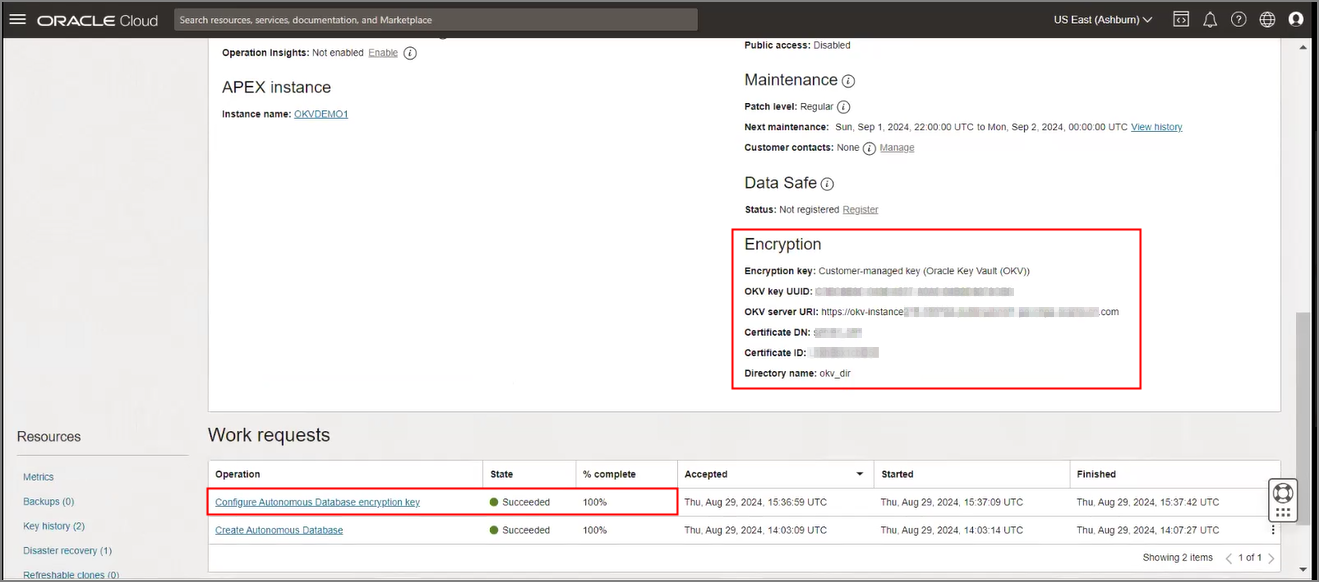
When the save completes successfully, encryption settings for the Autonomous AI Database instance are updated to show Customer-managed key (Oracle Key Vault (OKV)) and the work request state shows succeeded.
See Notes for Using Customer-Managed Keys with Autonomous AI Database for more information.
Parent topic: Manage Master Encryption Keys in Oracle Key Vault