IAM統合を使用したデータベース・クロステナンシへのアクセス
あるテナンシ内のユーザーおよびグループは、両方のテナンシ内のポリシーで許可されている場合、別のテナンシのAutonomous AI Databaseインスタンスにアクセスできます。
- DBaaSインスタンスへのIAMユーザーのクロステナンシー・アクセスについて
Oracle Cloud Infrastructure (OCI) DBaaSインスタンスへのクロステナンシー・アクセスは、単一のテナンシのシナリオに似ていますが、マッピングおよびトークン・リクエストにテナンシ情報が必要であり、このクロステナンシー・データベース・リソース・アクセスを許可するために両方のテナンシでポリシーが必要である点を除いています。 - ポリシーの構成
クロステナンシ・データベース・アクセスを許可するポリシーを作成するには、ユーザー・テナンシとデータベース・リソース・テナンシの両方にポリシーを作成する必要があります。 - 別のテナンシのユーザーおよびグループへのデータベース・スキーマとロールのマッピング
このタイプのマッピングを実行する場合は、テナンシOCIDをマッピング情報に追加して、データベースがそのクロテナンシー・アクセスであることを認識できるようにする必要があります。 - クロステナンシ・アクセス用のデータベース・クライアントの構成
一部のデータベース・クライアントを直接構成できます。 - Requesting Cross-Tenancy Tokens Using the OCI Command-Line Interface
You must add the--scopeparameter to the Oracle Cloud Infrastructure (OCI) command-line interface command to get adb-tokenfor a cross-tenancy request. アクセスしているデータベースがユーザー・テナンシのホーム・リージョンとは異なるリージョンにある場合は、--regionパラメータを使用してリージョンをOCI CLIコマンドにも追加する必要があります。
DBaaSインスタンスへのIAMユーザーのクロステナンシ・アクセスについて
Oracle Cloud Infrastructure (OCI) DBaaSインスタンスへのクロステナンシ・アクセスは、単一のテナンシのシナリオに似ていますが、マッピングおよびトークン・リクエストにテナンシ情報が必要であり、このクロステナンシ・データベース・リソース・アクセスを許可するために両方のテナンシでポリシーが必要である点を除きます。
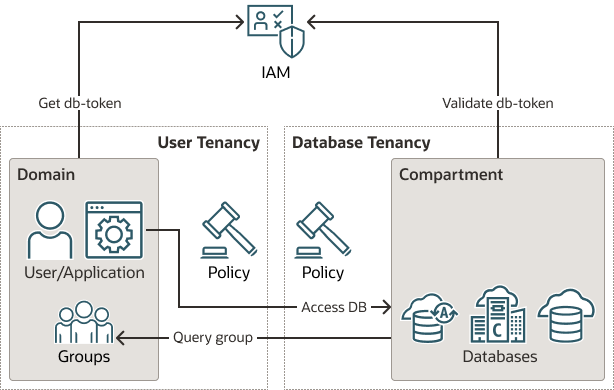
次の図は、OCI DBaaSインスタンスへのクロステナンシ・アクセスのプロセスを示しています。
クロステナンシ・プロセスは次のとおりです:
- ポリシーは、両方のテナンシでクロステナンシへのアクセスを承認および許可するために必要です。
- IAMプリンシパル(ユーザーまたはアプリケーション)は、クロステナンシ・リソースのdb-tokenをリクエストします。
db-tokenが返され、別のテナンシのデータベースへのアクセスに使用されます- データベースは、ユーザーのグループのクロステナンシ・グループ問合せを行い、プリンシパルをグローバル・スキーマおよびオプションのグローバル・ロールにマップします。
データベースが存在するリージョンと同じリージョンにユーザー・テナンシをサブスクライブする必要があります。たとえば、データベース・テナンシのデータベースがPHXおよびIADリージョンにある場合、ユーザー・テナンシをこれらのリージョンにサブスクライブする必要があります。これはホーム・リージョンではなく、ユーザー・テナンシの追加のサブスクライブ済リージョンです。
ポリシーの設定
クロステナンシ・データベース・アクセスを許可するには、ユーザー・テナンシとデータベース・リソース・テナンシの両方にポリシーを作成する必要があります。
- ソース・ユーザー・テナンシの構成
ユーザー・テナンシでクロステナシ・アクセスを許可するには、2つのポリシーが必要です。 - ターゲット・データベース・リソース・テナンシの構成
データベース・テナンシでは、ユーザー・テナンシからのユーザーへのアクセスを有効にする照合方針と、ユーザー・テナンシ内のグループ情報を問い合せます独自のデータベースを許可する照合方針が必要です - クロステナンシ・アクセスのポリシーの例
たとえば、WHERE句を使用してクロステナンシ構成を調整することや、このタイプの構成を実行するその他の方法があります。
ソース・ユーザー・テナンシの構成
ユーザー・テナンシでクロステナンシ・アクセスを許可するには、2つのポリシーが必要です。
親トピック: ポリシーの構成
ターゲット・データベース・リソース・テナンシの構成
データベース・テナンシでは、ユーザー・テナンシからのユーザーへのアクセスを有効にする照合方針と、ユーザー・テナンシ内のグループ情報を問い合せする独自のデータベースを許可する照合方針が必要です
any-userを使用すると、必要なポリシーを簡単に認識しやすくなりますが、Oracleでは、any-userに加えて、またはこれを使用するかわりに、より強力な制約を使用することをお薦めします。any-userオプションを使用すると、すべてのプリンシパルまたはリソースがuser_tenancy内のユーザー・グループを問い合せることができます。理想的には、これを制限して、データベース・リソース(リソース・プリンシパル)がグループ問合せを実行できるようにする必要があります。これを実行するには、ポリシーにWHERE句を追加するか、動的グループのメンバーに制限するための動的グループを追加します。動的グループおよびポリシーを指定する可能なすべての方法の定義は、このトピックの範囲外です。詳細は、次のソースを参照してください:
親トピック: ポリシーの構成
クロステナンシ・アクセスのポリシーの例
たとえば、WHERE句を使用してクロステナンシ構成を調整することや、このタイプの構成を実行するその他の方法があります。
WHERE句を追加して、クロステナンシ・グループ問合せの実行を許可するデータベース・リソースを制限できます:
ADMIT any-user of tenancy db_tenancy to {GROUP_MEMBERSHIP_INSPECT, AUTHENTICATION_INSPECT} in tenancy where request.principal.type = 'dbsystem'この許可ポリシーにより、db_tenancy内の任意のベース・データベース・サービス(リソース・タイプ: dbsystem)は、ユーザー・テナンシからユーザーのグループ情報を問い合せることができます。リソース・タイプ名は次の表にあります。
ポリシーを作成する同様の方法は、Autonomous Databaseのリソース・タイプを動的グループに追加することです:
dynamic group: db_principals any {resource.type = ‘autonomousdatabase’}この例では、any-userのかわりに動的グループを使用します:
ADMIT dynamic group db_principals of tenancy db_tenancy to {GROUP_MEMBERSHIP_INSPECT, AUTHENTICATION_INSPECT} in tenancyresource.compartment.idを使用して、コンパートメント内のすべてのリソース・プリンシパルを追加することもできます。ただし、これによって、他の非データベース・リソース・プリンシパルがクロステナンシ・グループ問合せを実行できる場合もあります。
親トピック: ポリシーの構成
別のテナンシのユーザーおよびグループへのデータベース・スキーマおよびロールのマッピング
このタイプのマッピングを実行する場合は、テナンシOCIDをマッピング情報に追加して、データベースがクロステナンシ・アクセスであることを認識できるようにする必要があります。
CREATE USER文およびCREATE ROLE文を使用するときは、コロンを使用してテナンシOCIDを区切ります。
クロステナンシ・アクセス用のデータベース・クライアントの構成
一部のデータベース・クライアントを直接構成できます。
データベース・テナンシは、OCI IAMからアクセス・トークンを直接取得するようクライアントが構成されている場合、接続文字列またはsqlnet.oraのいずれかで識別する必要があります。特定のパラメータ値(JDBC-thin、ODP.NET-core、Managed)について、クライアント固有のドキュメントを確認します。
OCIコマンドライン・インタフェースを使用したクロステナンシ・トークンのリクエスト
クロステナンシ・リクエストのdb-tokenを取得するには、Oracle Cloud Infrastructure (OCI)コマンドライン・インタフェース・コマンドに--scopeパラメータを追加する必要があります。アクセスしているデータベースがユーザー・テナンシのホーム・リージョンとは異なるリージョンにある場合は、--regionパラメータを使用してリージョンをOCI CLIコマンドにも追加する必要があります。
oci getコマンドのオプション・パラメータの使用方法の詳細は、オプションのパラメータを参照してください。
テナンシ全体に対してスコープを指定することも、テナンシのコンパートメントまたはデータベースにスコープを指定することもできます。クロス・テナンシ・コンパートメントまたはデータベースをスコープ指定する場合、コンパートメントおよびデータベースOCIDsはOCI全体で一意であるため、テナンシ情報も追加する必要はありません。
特定のクライアントは、MSEIから直接トークンをリクエストできます。MSEI OAuth2アクセス・トークンを取得するためのパラメータの設定に関するドキュメントを参照してください。